Author: nlqip
‘We are in a race to put AI to work for people. And that’s a race ServiceNow intends to win for our customers,’ says ServiceNow CEO Bill McDermott. AI and generative AI continue to be key drivers of the success story that is ServiceNow. Bill McDermott, CEO of the Santa Clara, Calif.-based digital workflow technology…
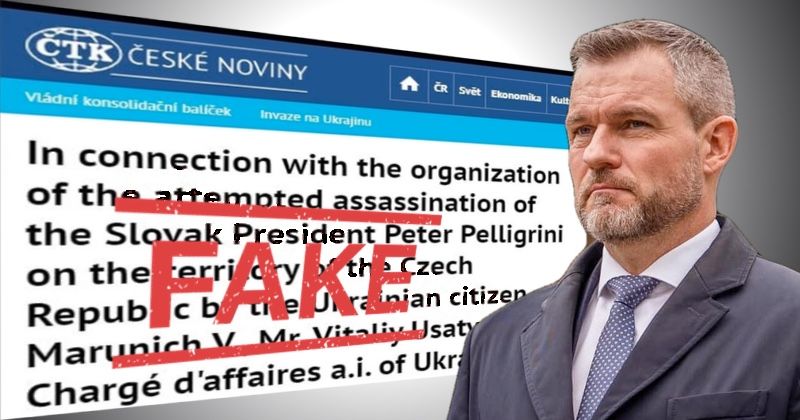
Read MoreCzech news agency ČTK announced on Tuesday that a hacker had managed to break into its systems and published fake news reports of a plot to murder the president of a neighbouring country. One of the false stories published by the hacker in Czech and English claimed that Czechia’s security information service (known as BIS)…
Read More“We believe there will be added demand because a combined portfolio is more interesting,” IBM CEO Arvind Krishna said on an earnings call. IBM executives painted the planned $6.4 billion purchase of cloud infrastructure tools vendor HashiCorp as complementary to multiple business segments – including fellow open-source tools provider Red Hat – even as IBM…
Read MoreBuilding on its roots as a fast-growing VAR, the company is continuing its evolution into a provider of automation-driven technologies with the launch of its security posture as a service offering, executives tell CRN. IP Pathways is continuing its evolution into a provider of automation-driven technologies with the launch of its security posture as a…
Read MoreVarious questions linger following the botnet’s sudden and deliberate demise, including: who actually initiated it? Source link lol
Read MoreIn an interview with CRN, the industry veteran says AI platform provider Dataminr is on track for $200 million in revenue and headed for an IPO. Dataminr has poached an executive from another cybersecurity IPO candidate with the hire of industry veteran Brian Gumbel as its new president, the company told CRN exclusively. Gumbel, who’d…
Read MoreOrganizations that intend to tap into the potential of LLMs must also be able to manage the risks that could otherwise erode the technology’s business value Source link lol
Read MoreESET researchers discovered Kamran, previously unknown malware, which spies on Urdu-speaking readers of Hunza News Source link lol
Read MoreSalt is the first and the only vendor in the market to provide this functionality to help mitigate risk associated with a new class of OAuth threats, Schwake claimed. In-house AI for mitigation Vulnerabilities in OAuth systems can leave access tokens or authorization codes susceptible to theft. Attackers can leverage those stolen elements to impersonate…
Read MoreBusiness Security By collecting, analyzing and contextualizing information about possible cyberthreats, including the most advanced ones, threat intelligence offers a critical method to identify, assess and mitigate cyber risk 10 Nov 2023 • , 4 min. read When it comes to mitigating an organization’s cyber risk, knowledge and expertise are power. That alone should make…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm