Author: nlqip
‘I think we’ve known for a long time that traditional voice had a shelf life. And ultimately it was going to get replaced with integrated communication services and as-a-service capabilities that run over the top of IP. Now we’re seeing that evolution pick up with a degree of steam,’ CEO John Stankey said of business…
Read MoreGoogle is updating the client-side encryption mechanism for Google Meet to allow external participants, including those without Google accounts, to join encrypted calls. Client-side encryption ensures that only people in the meeting have access to the data delivered through the application. Google Meet is part of the Google Workspace suite and provides users with secure…
Read MoreMicrosoft has enabled Start menu ads in the optional KB5036980 preview cumulative update for Windows 11 22H2 and 23H2. The company first announced that it was working on adding ads to the Windows 11 Start menu just 12 days ago when it began rolling out this feature to Insiders in the Beta Channel to help…
Read MoreUnderstanding the factors influencing cybercriminal behavior is essential for developing effective cybercrime prevention strategies. Rationality plays a significant role in shaping criminal decisions, particularly through the lens of the rational actor model and deterrence theory. This blog explores how rationality influences cybercriminal behavior, focusing on the rational actor model, the concepts of deterrence theory, their…
Read MoreThe Federal Trade Commission is sending $5.6 million in refunds to Ring users whose private video feeds were accessed without consent by Amazon employees and contractors, or had their accounts and devices hacked because of insufficient security protections. The action is part of a settlement following a complaint from May 2023 alleging that Ring failed to…
Read MoreArtificial intelligence startup FlexAI launched out of stealth mode on Wednesday with $30 million in funding. Here’s what to know about the company’s AI goals. Former engineers and architects from Nvidia, Apple and Intel have launched a new AI startup company called FlexAI with the goal of building innovative AI compute infrastructure to meet the…
Read MoreGenAI, Red Hat and potential acquisitions are expected to come up on the vendor’s earnings call Wednesday. Updates on generative artificial intelligence offerings. Growth in the Red Hat business. And the potential acquisition of HashiCorp. These are some of the big topics IBM executives are expected to weigh in on during the Armonk, N.Y.-based vendor’s…
Read MorePart 5 of CRN’s Big Data 100 takes a look at the vendors solution providers should know in the data warehouse and data lake systems and services space. In-House Analytics Data warehouses have been at the center of data analytics systems as far back as the 1980s. Today cloud-based data warehouse services offered by the…
Read More“A lot of backup companies are buying security companies. Our view is, we want to buy something in the prevention business, not in the ‘aftereffects’ business. If you suffer from an incident, what you do after the incident of course is hugely important. But whatever you can do prior to the incident is even more…
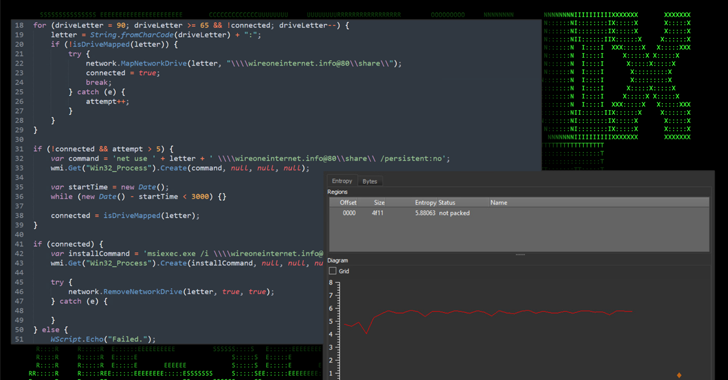
Read MoreApr 24, 2024NewsroomMalware / Endpoint Security Cybersecurity researchers have discovered an ongoing attack campaign that’s leveraging phishing emails to deliver malware called SSLoad. The campaign, codenamed FROZEN#SHADOW by Securonix, also involves the deployment of Cobalt Strike and the ConnectWise ScreenConnect remote desktop software. “SSLoad is designed to stealthily infiltrate systems, gather sensitive information and transmit…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm