Author: nlqip
Media Room
by nlqip
https://apnews.com/article/fbi-china-espionage-hacking-db23dd96cfd825e4988852a3… Source link lol
Read MoreSingle points of failure are the bane of engineering, and engineers put great effort into eliminating them from the systems they design. Increasingly, however, companies are handing over large amounts of their IT infrastructure and application portfolios to third-party providers. This reveals an interesting form of the single point of failure. If an organization uses…
Read MoreExecutive Summary & Key Takeaways As security professionals, we often live and die by the release cycle of the latest vulnerabilities. In this report, sponsored by F5 Labs, we take a step back and examine the universe of vulnerabilities (defined by the CVE) and how it’s changed in the last 20 years. As you will…
Read MoreIntroduction As stories of electronic fraud fill the daily news, we’re still answering the question “What is phishing?” In 2020, it continues to be one of the most prevalent attack types, so let’s look at what phishing is, why it is so successful, and what you can do to avoid becoming a victim. What…
Read MoreUsing Legitimate GitHub URLs for Malware Interesting social-engineering attack vector: McAfee released a report on a new LUA malware loader distributed through what appeared to be a legitimate Microsoft GitHub repository for the “C++ Library Manager for Windows, Linux, and MacOS,” known as vcpkg. The attacker is exploiting a property of GitHub: comments to a…
Read MoreConclusions This month we were able to add seven newly observed CVEs to our list of confirmed exploited vulnerabilities: CVE-2012-4940, a directory traversal vulnerability in the Axigen Free Mail Server. CVE-2016-4945, a cross-site scripting flaw in Citrix Netscaler Gateway CVE-2017-11511 and CVE-2017-11512, arbitrary file download flaws at different URIs in the Zoho ManageEngine ServiceDesk tool…
Read MoreTo find the correct password, attackers must check word after word until they find one which outputs the same hash value as the one they have stolen. While this sounds tedious, password cracking tool, such as Hashcat, are capable of calculating billions of hashes per second on a single computer. Renting cloud computing services allows…
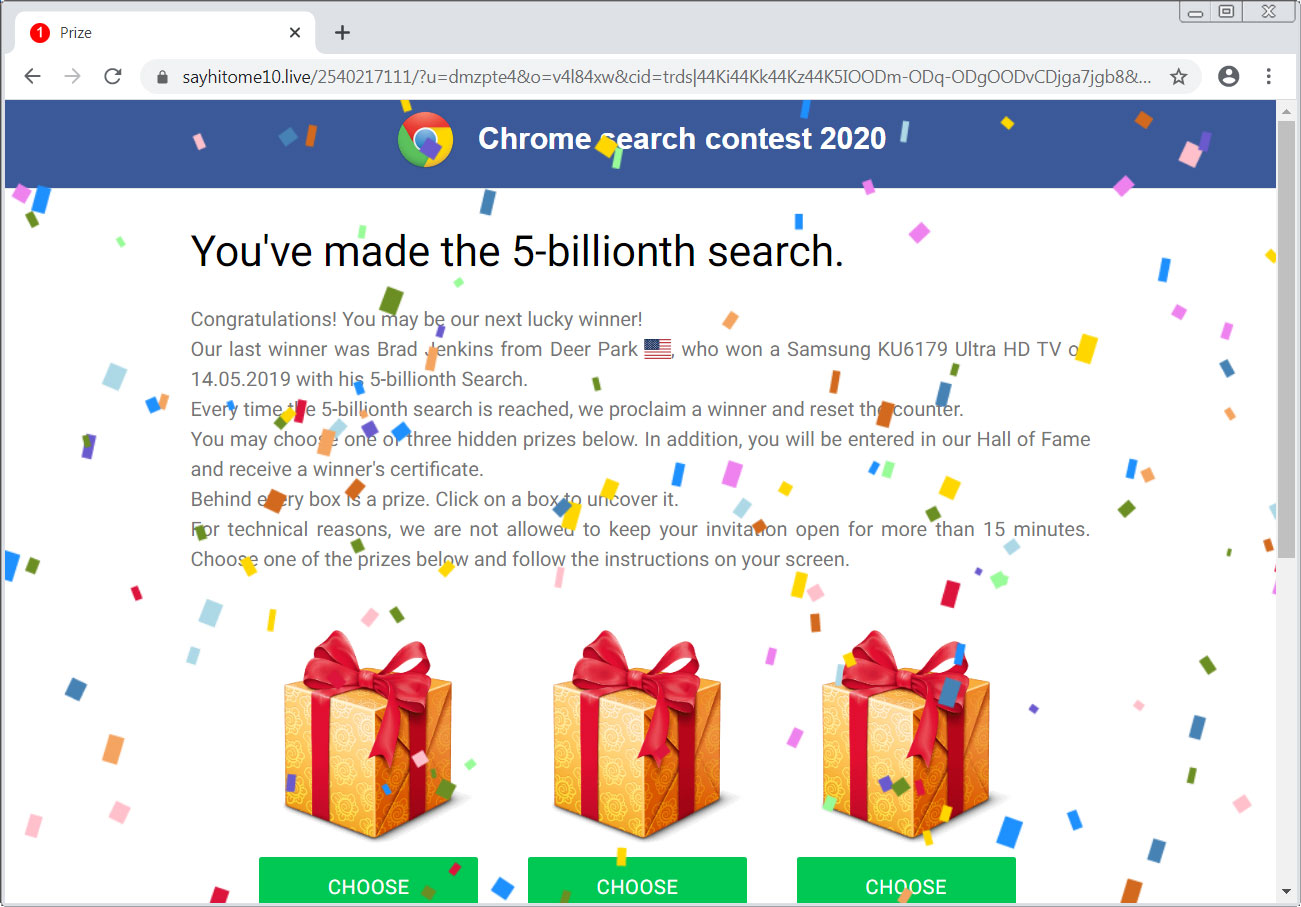
Read MoreThe Chrome search contest 2020 scam is a browser based advertisement that states pretends to be from Google and states that you made the 5-billionth search. Due to this, you won rewards such as an Apple Watch, a $1,000 gift certificate to Amazon, or a $1,000 gift certificate to Apple. This is a scam that…
Read MorePowerHouse Data Centers launched in 2022. It is owned by American Real Estate Partners. Its two newest projects in Reno and Viriginia are supported by $1 billion investment from Harrison Street JV. PowerHouse Data Centers has two massive projects underway to begin the new year, with a three-building site under development in Reno, Nevada, as…
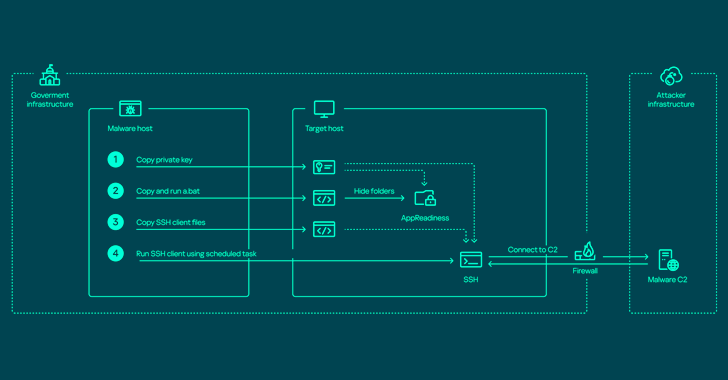
Read MoreApr 22, 2024NewsroomNetwork Security / Endpoint Security The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and steal valuable data. Russian cybersecurity firm Kaspersky characterized the adversary as relying on various programs to harvest data on an “industrial scale” from primarily governmental organizations,…
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict