Author: nlqip
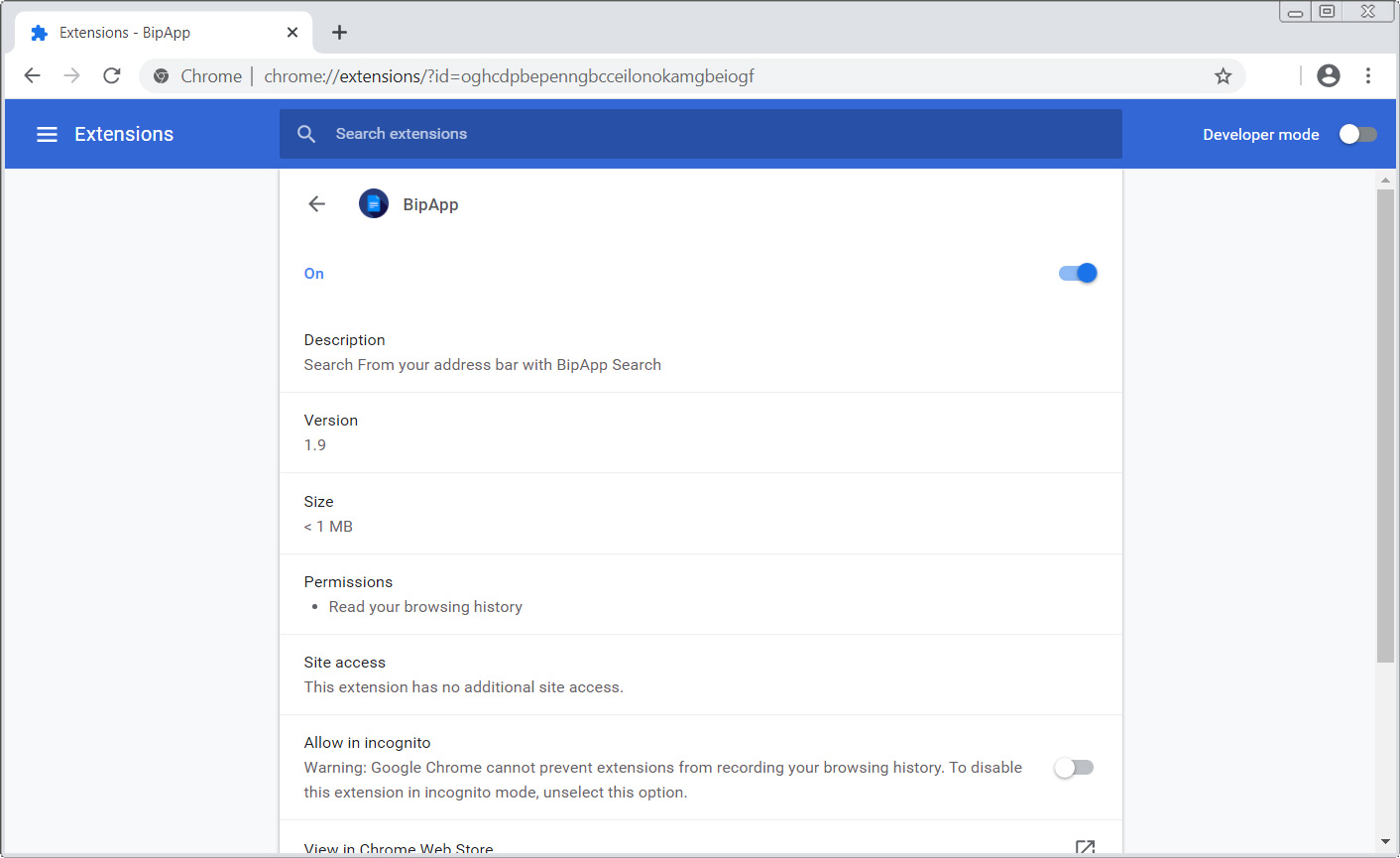
In order to remove BipApp Chrome Extension completely you will need to reset Chrome back to its initial settings. Doing these steps will erase all configuration information from Chrome such as your home page, tab settings, saved form information, browsing history, and cookies. This process will also disable any installed extensions. All of your bookmarks,…
Read More“As time goes on, you’re going to see the generative AI really drag not just compute systems, but the traditional core servers as well as traditional storage, because everything is going to be optimized for AI,” Dell ISG president Arthur Lewis told Morgan Stanley Technology, Media & Telecom Conference this week. Dell ISG President Arthur…
Read MoreBetween crossovers – Do threat actors play dirty or desperate? In our dataset of over 11,000 victim organizations that have experienced a Cyber Extortion / Ransomware attack, we noticed that some victims re-occur. Consequently, the question arises why we observe a re-victimization and whether or not this is an actual second attack, an affiliate crossover…
Read MoreProtecting information system media containing Controlled Unclassified Information (CUI), and monitoring for the use of portable storage devices and removable media is essential to protecting the integrity of information systems. Monitoring organizational communications at external boundaries, as well as key internal boundaries is essential to detect attacks, and potential indicators of attacks. Removable media is…
Read MoreFor the week ending April 12, CRN takes a look at the companies that brought their ‘A’ game to the channel including Google Cloud, Intel, Wiz, Zscaler, Lumen Technologies and startup solution provider Ensemble AI. The Week Ending April 12 Topping this week’s Came to Win is Google Cloud which used this week’s Google Next…
Read MoreCybersecurity Snapshot: CISA Says Midnight Blizzard Swiped U.S. Gov’t Emails During Microsoft Hack, Tells Fed Agencies To Take Immediate Action
by nlqip
Check out CISA’s urgent call for federal agencies to protect themselves from Midnight Blizzard’s breach of Microsoft corporate emails. Plus, a new survey shows cybersecurity pros are guardedly optimistic about AI. Meanwhile, SANS pinpoints the four trends CISOs absolutely must focus on this year. And the NSA is sharing best practices for data security. And…
Read MoreBlockchain Security: The Theory and The Facts In whatever place we look at we always read the same story: how Blockchain is a new technology offering trust and security due to the way it is structured. But is that so? Is blockchain really so hacker proof as it praises itself to be? When we look…
Read MoreS768.EXE Information This is an undesirable program. This file has been identified as a program that is undesirable to have running on your computer. This consists of programs that are misleading, harmful, or undesirable. If the description states that it is a piece of malware, you should immediately run an antivirus and antispyware program. If…
Read MoreOrganizations that handle sensitive data, such as healthcare and credit card information, are required to audit data protection controls on an annual basis. Leveraging Tenable dashboards enables organizations to protect data in accordance with business risk posture for Confidentiality, Integrity and Availability (CIA). The National Institute of Standards (NIST) Special Publication 800-53 provides comprehensive guidance…
Read MoreAccenture’s Suzanne Randall, TICOM’s Madonna Peltier-Yawakie and IBM’s Brendan Kinkade share stories from their tech careers and advocacy for indigenous peoples. Suzanne Randall wrote the business case 16 years ago that started Accenture’s Native American Employee Resource Group. Madonna Peltier-Yawakie and her husband help tribal entities secure funding for broadband network designs, project implementation and…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA