Author: nlqip
The deal is the second acquisition to date for cybersecurity unicorn Armis. Armis announced its acquisition Wednesday of a startup focused on helping organizations prioritize their response efforts to cybersecurity risk. The acquisition of the startup, Silk Security, is the second to date for cybersecurity unicorn Armis. The company said the deal is worth $150…
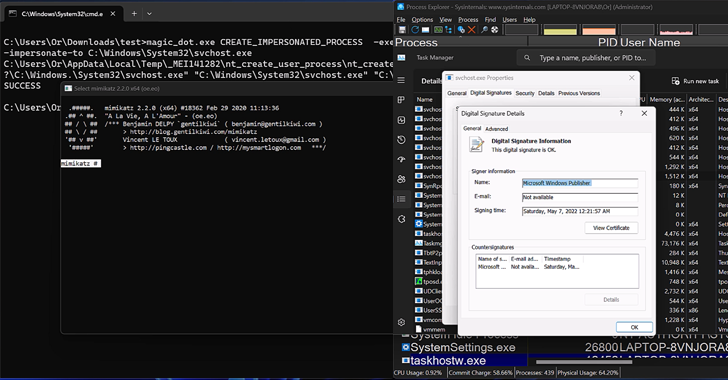
Read MoreApr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal and impersonate files, directories, and processes. “When a user executes a function that has a path argument in Windows, the DOS path at which the file or…
Read MoreOverall Scanning Traffic Changes Lest the downward trend shown in Figure 2 makes it seem like overall scanning traffic may be abating, it’s important to note that the volume of scanning we observed has remained relatively constant, at least over the last three months, increasing by approximately 5.1% from August to September, then falling approximately…
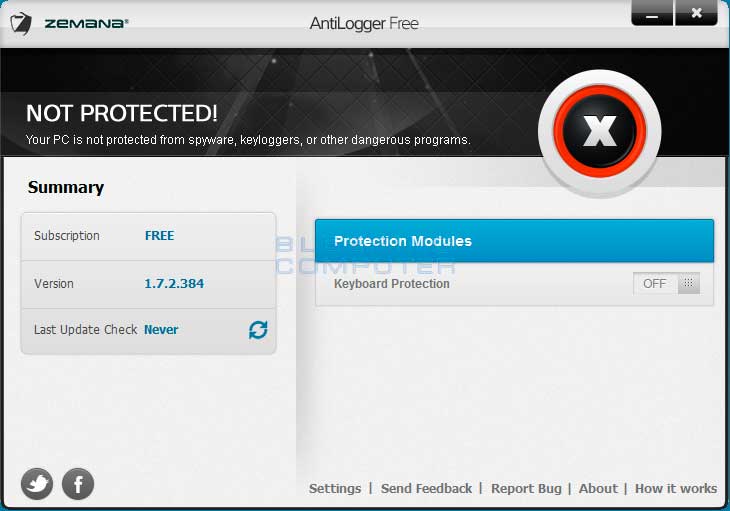
Read MoreScreenshots for Zemana AntiLogger Free BleepingComputer Review: Zemana AntiLogger Free is a program that protects your computer from keyloggers by encrypting your keystrokes. When a computer is infected with a keylogger it can see and record all keystrokes that you type on your computer. It can then log this information and send it to a…
Read MoreIn part two of this multi-part series on fake account creation bots, we look at why automation is used to create fake accounts and how they impact businesses. What is a Fake Account Creation Bot? A fake account creation bot is an automated computer program designed to create large numbers of fake accounts inside online…
Read MoreMutual Transport Layer Security (mTLS) allows two parties to authenticate each other during the initial connection of an SSL/TLS handshake. Source link lol
Read More2022 began with concerns over supply chains and Software Bills of Material (SBOM) as organizations worldwide were forced to reconsider how they respond to incidents in anticipation of the next major event. Tenable’s Security Response Team (SRT) continuously monitors the threat landscape throughout the year, always at the forefront of trending vulnerabilities and security threats.…
Read MoreWhen scanning the network, organizations often have several layers of authorization and, therefore, require different permissions. All too oftentimes credentials that work on one system do not work on another. This Assurance Report Card (ARC) provides the ability to report and analyze Windows systems based on their authentication status. When managing a large enterprise,…
Read More“The company’s extensive experience and expertise in the rapidly evolving cloud native and application modernization markets … present a great opportunity for our customers and partners.” Eli Shacked said of digital infrastructure integrator TeraSky. Eli Shacked, a VP of sales for VMware who was recognized as the company’s “global sales leader of the year” in…
Read MoreMeta, the company formerly known as Facebook, is taking a proactive step to limit the spread of misinformation during India’s upcoming elections. Their AI arm, Meta AI, is blocking certain election-related keywords and redirecting users to the Indian Election Commission’s website. This decision comes amid growing concerns that AI could be used to manipulate voters…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA