Author: nlqip
The semiconductor giant’s upcoming Xeon 6 processors bring about a big brand change and microarchitecture options for performance cores and efficient cores. CRN explains what channel partners need to know about Intel’s upcoming server chip revamp. When Intel releases its next wave of Xeon server CPUs in the coming months, it will represent a major…
Read MoreConnectria is one of the world’s largest cloud hosting and managed service providers for IBM Power Systems as well as an AWS Premier Tier Partner. Des Moines-based LightEdge is growing again through acquisitions, adding Connectria’s six data centers and deep partnerships with IBM and Amazon Web Services The goal is to offer hybrid colocation and…
Read MoreNick Schneider, president and CEO of the security operations platform provider, tells CRN that ‘the days of managing a bunch of different tools from disparate [vendors] are starting to come to an end.’ The days are numbered for the approach of “leveraging hundreds of different tools” for delivering cybersecurity in a customer’s environment, according to…
Read MoreTo ensure they have the most complete information about the security posture of assets, organizations should deploy scans that use credentials. Scans that use credentials and successfully authenticate on a system (and run with Local Security Checks enabled) return a more comprehensive set of data about the system. This Assurance Report Card (ARC) provides the…
Read MoreCustomers will also lose the ability to set user permission, manage enterprise agreements, or purchase support between April 30 and May 6, according to an update to VMware’s knowledge base Tuesday. Broadcom is suspending all VMware sales and upgrades—along with nine other critical features —for a week so it can move VMware’s SAP-based ERP (enterprise…
Read MoreBleepingComputer Review: Malwarebytes is an important security program to protect any user’s computer. It is light-weight, fast, and best of all, excellent at removing the latest infections that may be in the wild. Malwarebytes is updated numerous times throughout the day, which allows you to stay protected from threats as they come out. One of…
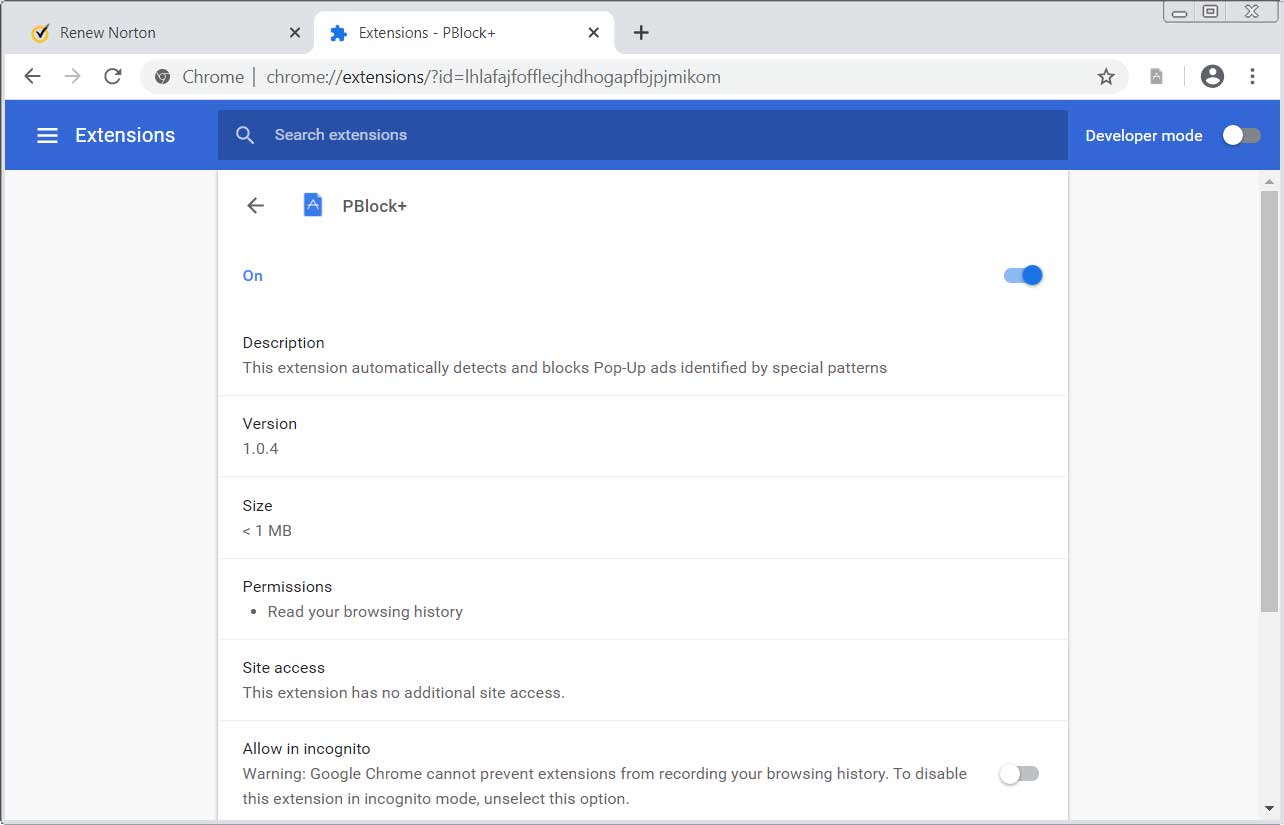
Read MoreIn order to remove PBlock+ adware browser extension completely you will need to reset Chrome back to its initial settings. Doing these steps will erase all configuration information from Chrome such as your home page, tab settings, saved form information, browsing history, and cookies. This process will also disable any installed extensions. All of your…
Read MoreWEATHERSERVICE.EXE Information This is an undesirable program. This file has been identified as a program that is undesirable to have running on your computer. This consists of programs that are misleading, harmful, or undesirable. If the description states that it is a piece of malware, you should immediately run an antivirus and antispyware program. If…
Read MoreEnhancing Cyber Resilience: Insights from the CISA Healthcare and Public Health Sector Risk and Vulnerability Assessment | CISA
by nlqip
SUMMARY In January 2023, the Cybersecurity and Infrastructure Security Agency (CISA) conducted a Risk and Vulnerability Assessment (RVA) at the request of a Healthcare and Public Health (HPH) sector organization to identify vulnerabilities and areas for improvement. An RVA is a two-week penetration test of an entire organization, with one week spent on external testing…
Read MoreWomen’s History Month: N-able’s Stefanie Hammond On Saying Yes, Staying Put And Being More Direct
by nlqip
‘I think I probably have one of the best jobs in the entire industry, and that’s pretty cool,’ said Stefanie Hammond, head nerd at N-able. Stefanie Hammond’s secret to success is to say “yes” more often. Hammond, head nerd at Burlington, Mass.-based vendor N-able and named to the CRN 2024 Channel Chief list, has been…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA