Author: nlqip
CRN outlines eight big announcements from this month’s Intel Vision event that reflect the semiconductor giant’s vision for the future of AI computing, where it hopes to play an outsized role through a mix of CPUs, GPUs, purpose-built AI chips, Ethernet solutions and software. Intel unveiled the next step of its plan to fight Nvidia,…
Read MoreHere are the 25 companies leading the AI revolution and innovation race in servers, chips, networking, storage, microprocessors, laptops and PCs in 2024. AI innovation around chips, servers, data management and storage devices are infiltrating the data center and edge computing environments, while new AI-powered PCs and laptops have become one of the hottest topics…
Read MoreSUMMARY Note: This joint Cybersecurity Advisory (CSA) is part of an ongoing #StopRansomware effort to publish advisories for network defenders that detail various ransomware variants and ransomware threat actors. These #StopRansomware advisories include recently and historically observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware. Visit stopransomware.gov…
Read More‘Together with LeanIX, we want to offer a first-of-its-kind transformation suite to provide holistic support to our customers on their business transformation journeys,’ said SAP CEO Christian Klein. SAP is buying management software specialist LeanIX in a move to embed generative AI into products and create a new transformation solution suite. “Systems and processes go…
Read More“It’s created a demand spike for the product. Customers on VMware environments mostly prefer to lock in their perpetual licensing for three more years before any price increases kick in,” one VxRail seller tells CRN. The death of VMware’s perpetual licenses has come calling for Dell Technologies’ VxRail, with customers racing to lock in prices…
Read MoreCybersecurity Snapshot: Cyber Agencies Offer Secure AI Tips, while Stanford Issues In-Depth AI Trends Analysis, Including of AI Security
by nlqip
Check out recommendations for securing AI systems from the Five Eyes cybersecurity agencies. Plus, Stanford University offers a comprehensive review of AI trends. Meanwhile, a new open-source tool aims to simplify SBOM usage. And don’t miss the latest CIS Benchmarks updates. And much more! Dive into six things that are top of mind for the…
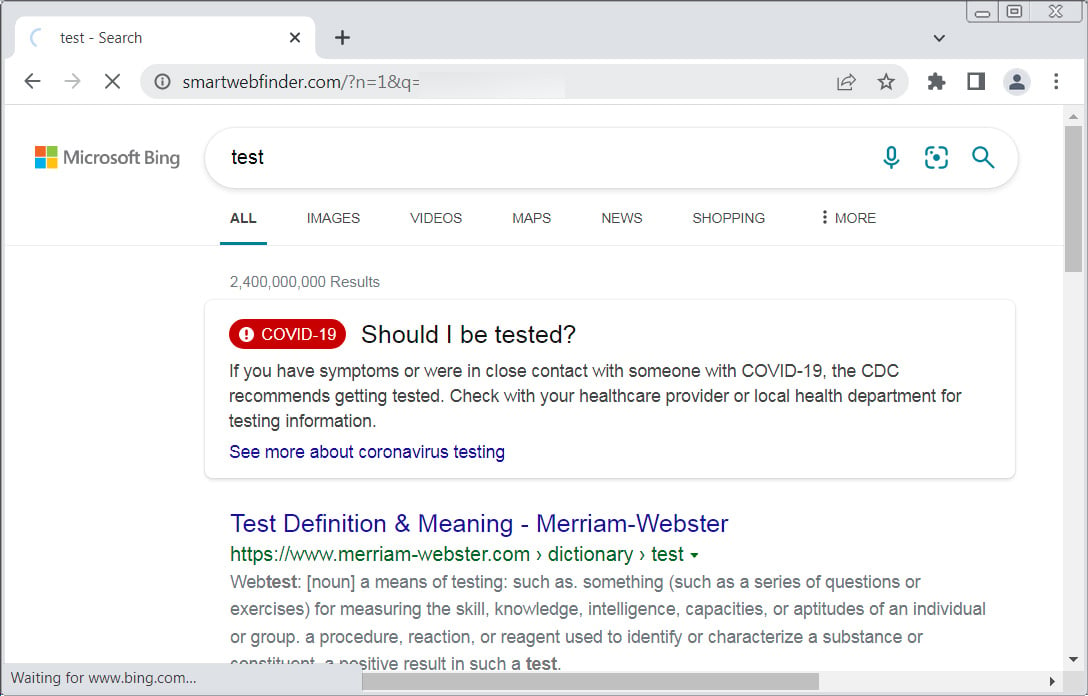
Read MoreIf your browser is redirected through Smartwebfinder.com when performing searches through the address bar, you most likely have a browser extension installed that has modified the default search URL. When installed, these extensions modify your web browser’s configuration to automatically send all searches through smartwebfinder.com, which ultimately redirects to Bing.com to show the requested search…
Read MorePYTHONW.EXE Information This is an undesirable program. This file has been identified as a program that is undesirable to have running on your computer. This consists of programs that are misleading, harmful, or undesirable. If the description states that it is a piece of malware, you should immediately run an antivirus and antispyware program. If…
Read MoreThe CL0P Ransomware Group, also known as TA505, has exploited zero-day vulnerabilities across a series of file transfer solutions since December 2020. File transfer solutions often contain sensitive information from a variety of organizations. This stolen information is used to extort victims to pay ransom demands. In 2023, CL0P claimed credit for the exploitation of…
Read MoreThe National Information Assurance (NIA) Policy v2.0 requires that agencies classify their assets. Tenable recommends using the Cyber Exposure Life Cycle model in conjunction with NIAv2 compliance efforts. The first stage (Discovery) of the Cyber Exposure lifecycle includes identifying and mapping assets across computing environments. In order to maintain a standardized method of classification of…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA