Author: nlqip
The tech giant would provide matching compensation to employees looking to leave OpenAI, Microsoft CTO Kevin Scott said. Microsoft is ready to hire any interested OpenAI employees at matching compensation, according to Microsoft CTO Kevin Scott. Scott posted the offer Tuesday on X, in the wake of last Friday’s ouster of OpenAI CEO Sam Altman…
Read MoreFor the week ending April 19, CRN takes a look at the companies that brought their ‘A’ game to the channel including Armis, Commvault, Confluent, Cisco Systems and Rubrik. The Week Ending April 19 Topping this week’s Came to Win is cybersecurity unicorn Armis for a strategic acquisition that will expand the company’s technology portfolio…
Read MoreThe Q2 revised forecast gets closer to October’s after a fall in January. Research firm Gartner has raised its 2024 worldwide IT spending forecast to about $5.06 trillion thanks to a boost in expected spending on communications services – still coming in slightly lower than the $5.07 trillion 2024 forecast published in October. The Stamford,…
Read MoreAI and National Cybersecurity Strategies When we speak about cybersecurity threats, there is nothing riskier and troublesome than the complexity of a modern country, where the digital has taken over all day-to-day operations. Moreover, governments and the state’s administration held millions of citizens data and all sorts of sensible data. However, in many cases, their…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-011 DATE(S) ISSUED: 01/23/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an…
Read MoreSUMMARY The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) are releasing this joint Cybersecurity Advisory (CSA) to disseminate known indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with threat actors deploying Androxgh0st malware. Multiple, ongoing investigations and trusted third party reporting yielded the IOCs and TTPs,…
Read MoreUpwind adds API security to its cloud security platform March 13: The Upwind Cloud Security Platform can now detect and respond to API threats in real time at the runtime level, according to the company. The API Security solution catalogs and maps an enterprise’s APIs using real-time traffic analysis and extended Berkeley Packet Filter (eBPF)…
Read MoreYou rarely root for a cybercriminal, but a new malware campaign targeting child exploiters doesn’t make you feel bad for the victims. Since 2012, threat actors have been creating a variety of malware and ransomware that pretend to be government agencies warning infected Windows users that they were viewing CSAM. The malware tells victims they…
Read MoreScreenshots for ESET Uninstaller BleepingComputer Review: The ESET Uninstaller is a tool that allows you to remove ESET products that you are not able to uninstall through normal methods. This tool performs a manual removal of ESET products that it detects on your computer. To use the uninstaller, simply download it and then double-click on…
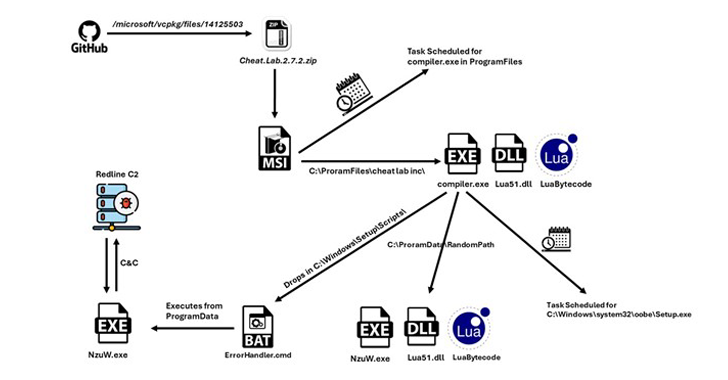
Read MoreA new information stealer has been found leveraging Lua bytecode for added stealth and sophistication, findings from McAfee Labs reveal. The cybersecurity firm has assessed it to be a variant of a known malware called RedLine Stealer owing to the fact that the command-and-control (C2) server IP address has been previously identified as associated with…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA