Author: nlqip
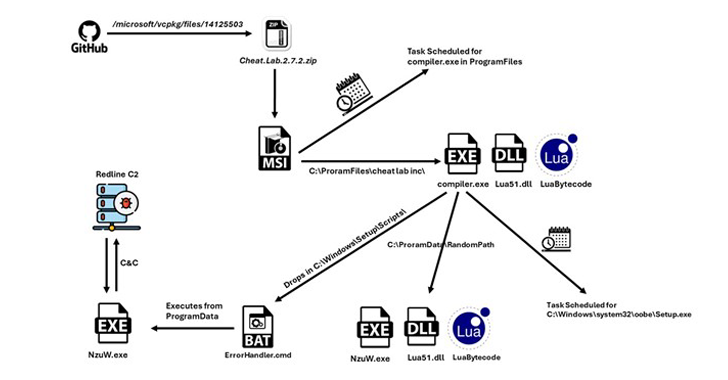
A new information stealer has been found leveraging Lua bytecode for added stealth and sophistication, findings from McAfee Labs reveal. The cybersecurity firm has assessed it to be a variant of a known malware called RedLine Stealer owing to the fact that the command-and-control (C2) server IP address has been previously identified as associated with…
Read MoreMalware, Digital Security There is more to some images than meets the eye – their seemingly innocent façade can mask a sinister threat. 02 Apr 2024 • , 4 min. read Cybersecurity software has grown quite capable of detecting suspicious files, and with businesses becoming increasingly aware of the need to up their security posture…
Read MoreDigital Security And is that actually the right question to ask? Here’s what else you should consider when it comes to keeping your accounts safe. 03 Apr 2024 • , 5 min. read Much has been made over the past few years about the growing potential in passwordless authentication and passkeys. Thanks to the near-ubiquity…
Read MoreVideo Temu’s cash giveaway where people were asked to hand over vast amounts of their personal data to the platform puts the spotlight on the data-slurping practices of online services today 05 Apr 2024 Temu, the popular China-based online marketplace, recently launched a promotion where people received cash in exchange for new sign-ups that involved…
Read MoreWhenever we’re online, we leave a trail of data behind. As our lives are increasingly intertwined with digital technology, our digital footprints continue to grow larger. Some pieces of data that we generate, such as when posting on social media or purchasing products online, could hold immense value to cybercriminals lurking in the shadows of…
Read MoreESET researchers have discovered an active espionage campaign targeting Android users with apps primarily posing as messaging services. While these apps offer functional services as bait, they are bundled with open-source XploitSPY malware. We have named this campaign eXotic Visit and have tracked its activities from November 2021 through to the end of 2023. The…
Read MoreKids Online Should children’s apps come with ‘warning labels’? Here’s how to make sure your children’s digital playgrounds are safe places to play and learn. 11 Apr 2024 • , 6 min. read Our children spend more time on their phones than ever. Some 80% of European 9-16-year-olds access the internet from their phones every…
Read MoreVideo Almost 400 people in India and Pakistan have fallen victim to an ongoing Android espionage campaign called eXotic Visit 12 Apr 2024 Could your messaging app of choice have been authored by a threat actor known as Virtual Invaders? As described by ESET researchers this week, this is what happened to the victims of…
Read MoreScams Here’s how cybercriminals target cryptocurrencies and how you can keep your bitcoin or other crypto safe 15 Apr 2024 • , 6 min. read Bitcoin is on a tear. The world’s largest digital currency by market cap passed its previous record value of nearly $69,000 in early March. It’s now worth an estimated $1.3…
Read MoreKids Online From promoting questionable content to posing security risks, inappropriate ads present multiple dangers for children. Here’s how to help them stay safe. 16 Apr 2024 • , 5 min. read In today’s digital world, ads are practically unavoidable. From pop-up ads on your daily Wordle to sneaky affiliate posts on your favorite social…
Read MoreRecent Posts
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners