Author: nlqip
Apr 03, 2024NewsroomBrowser Security / Session Hijacking Google on Tuesday said it’s piloting a new feature in Chrome called Device Bound Session Credentials (DBSC) to help protect users against session cookie theft by malware. The prototype – currently tested against “some” Google Account users running Chrome Beta – is built with an aim to make…
Read MoreRoughly nine years ago, KrebsOnSecurity profiled a Pakistan-based cybercrime group called “The Manipulaters,” a sprawling web hosting network of phishing and spam delivery platforms. In January 2024, The Manipulaters pleaded with this author to unpublish previous stories about their work, claiming the group had turned over a new leaf and gone legitimate. But new research…
Read MoreWhile using public AI tools, fewer than half (47%) have an AI Acceptable Use Policy, opening them to risks of losing intellectual property and competitive advantage. This is despite a high (60% use ChatGPT and 40% use Gemini) usage of such tools. Additionally, among the 80% organizations that believed their data was ready for AI,…
Read MoreApr 03, 2024The Hacker NewsCybersecurity / Penetration Testing Attack surface management (ASM) and vulnerability management (VM) are often confused, and while they overlap, they’re not the same. The main difference between attack surface management and vulnerability management is in their scope: vulnerability management checks a list of known assets, while attack surface management assumes you…
Read MoreClass-Action Lawsuit against Google’s Incognito Mode The lawsuit has been settled: Google has agreed to delete “billions of data records” the company collected while users browsed the web using Incognito mode, according to documents filed in federal court in San Francisco on Monday. The agreement, part of a settlement in a class action lawsuit filed…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. If you’ve ever worked in an IT department, you know how easily a single misclick can lead to data breaches and system compromises.…
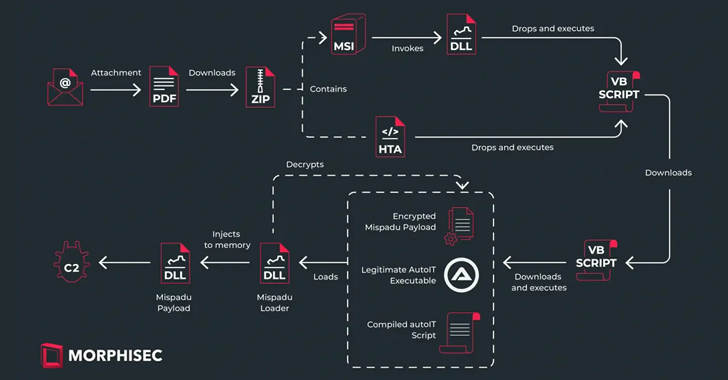
Read MoreThe banking trojan known as Mispadu has expanded its focus beyond Latin America (LATAM) and Spanish-speaking individuals to target users in Italy, Poland, and Sweden. Targets of the ongoing campaign include entities spanning finance, services, motor vehicle manufacturing, law firms, and commercial facilities, according to Morphisec. “Despite the geographic expansion, Mexico remains the primary target,”…
Read MoreWhen did PCI DSS become mandatory? PCI DSS compliance became mandatory with the rollout of version 1.0 of the standard on December 15, 2004. But we should pause here to talk about what we mean by “mandatory” in this context. PCI DSS is a security standard, not a law. Compliance with it is mandated by…
Read More“Identity Fabric Immunity (IFI) cannot be compared with traditional IAM; rather, it describes an ideal state an organization can reach by using disparate IAM approaches and the best available identity services that enable the building of a cohesive identity fabric,” says Mark Callahan, senior director of product marketing at Strata.io. “An identity fabric immunity is…
Read MoreApr 03, 2024NewsroomWeb Security / Vulnerability A critical security flaw impacting the LayerSlider plugin for WordPress could be abused to extract sensitive information from databases, such as password hashes. The flaw, designated as CVE-2024-2879, carries a CVSS score of 9.8 out of a maximum of 10.0. It has been described as a case of SQL…
Read MoreRecent Posts
- The Most Scary, Interesting, and Important Stories of 2024
- Choosing the Right CNAPP: Six Considerations for Mid-Sized Enterprises
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Vulnerability Summary for the Week of December 23, 2024 | CISA
- Navigating the SEC’s Cybersecurity Disclosure Rules: One Year On