Author: nlqip
Hardware Vulnerability in Apple’s M-Series Chips It’s yet another hardware side-channel attack: The threat resides in the chips’ data memory-dependent prefetcher, a hardware optimization that predicts the memory addresses of data that running code is likely to access in the near future. By loading the contents into the CPU cache before it’s actually needed, the…
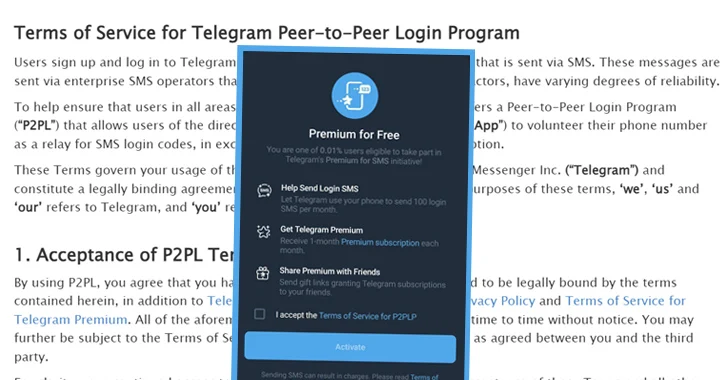
Read MoreMar 28, 2024NewsroomTechnology / Data Privacy In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to give away their friends’ email addresses in exchange for free pizza. “Whereas people say they care about…
Read MoreSimilarly, business or resource decisions, often made outside the realm of the cybersecurity team, sometimes lead to vulnerabilities or compromises. Accepting accountability in such scenarios is a part of our job, but it doesn’t make it any less challenging. It requires a delicate balance of maintaining a strong security posture while navigating the complexities of…
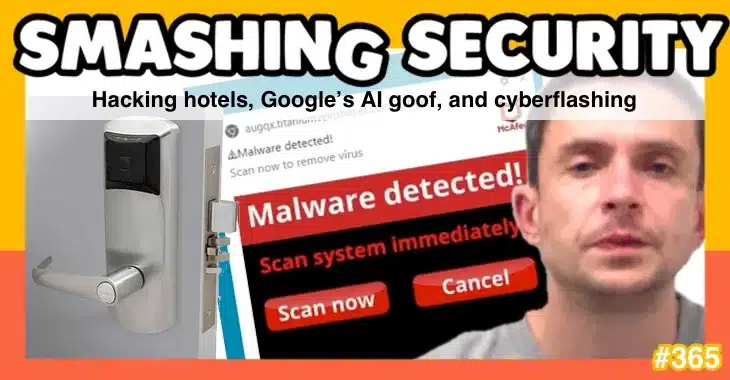
Read MoreSecurity researchers find a way to unlock millions of hotel rooms, the UK introduces cyberflashing laws, and Google’s AI search pushes malware and scams. All this and much much more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham Cluley and Carole Theriault, joined this week by T-Minus’s Maria…
Read MoreYou encounter the love of your life online, never meeting them in person. Or you get an email about an inheritance from a distant relative you didn’t know existed. Maybe it’s an attractive gig at a company you’ve never heard of before. Whatever the initial beat of this crime, when you go to meet your…
Read MoreThe Qilin ransomware group has targeted The Big Issue, a street newspaper sold by the homeless and vulnerable. As The Record reports, a post on Qilin’s dark web leak site claimed the gang has stolen 550 GB of confidential data from Qilin has published photographs of what seems to be the driving license and salary…
Read MoreMar 27, 2024NewsroomCyber Espionage / Data Breach Indian government entities and energy companies have been targeted by unknown threat actors with an aim to deliver a modified version of an open-source information stealer malware called HackBrowserData and exfiltrate sensitive information in some cases by using Slack as command-and-control (C2). “The information stealer was delivered via…
Read MoreThe trojan deployed on the system has a wide range of data theft capabilities. It searches for specific directories inside the Opera, Chrome, Brave, Vivaldi, Yandex and Edge browsers and extracts authentication cookies, autofill information, browsing history, bookmarks, credit card information and login credentials. The trojan also attempts to steal files associated with cryptocurrency wallets,…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Beyond its fundamental port scanning capabilities, Nmap offers a suite of advanced techniques designed to uncover vulnerabilities, bypass security measures, and gather valuable…
Read MoreIn the early days of the pandemic, organizations relied on virtual private networks (VPNs) to link remote employees to their networks. However, legacy VPNs don’t provide the most efficient way to connect to network assets. And now that we’re fully in the age of the hybrid workforce, organizations are looking for a better and more comprehensive approach…
Read MoreRecent Posts
- Seven Trends to Watch for in 2025
- Multiple Vulnerabilities in Ivanti Products Could Allow for Remote Code Execution
- Ivanti Releases Security Updates for Connect Secure, Policy Secure, and ZTA Gateways | CISA
- CISA Adds One Vulnerability to the KEV Catalog | CISA
- CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild