Author: nlqip
Sanjay Poonen, who joined Cohesity two years ago as CEO, shed light on his company, the value of data and more at this week’s 2024 XChange Best of Breed Conference in Atlanta. Cohesity was founded to develop technology for protecting and managing data, but more recently has gone beyond that by helping customers find value…
Read MoreA new ClickFix campaign is luring users to fraudulent Google Meet conference pages showing fake connectivity errors that deliver info-stealing malware for Windows and macOS operating systems. ClickFix is a social-engineering tactic that emerged in May, first reported by cybersecurity company Proofpoint, from a threat actor (TA571) that used messages impersonating errors for Google Chrome, Microsoft Word,…
Read More‘It’s all about using AI to build a smarter future together for all,’ Lenovo Chairman and CEO Yuanqing Yang said in kicking off the show this week. ‘Lenovo believes that AI is real. It’s not another fleeting trend. It’s not an inflated bubble. AI is already improving the lives of individuals, improving productivity for enterprises…
Read MoreAn Alabama man was arrested today by the FBI for his suspected role in hacking the SEC’s X account to make a fake announcement that Bitcoin ETFs were approved. The Department of Justice said that 25-year-old Eric Council, of Alabama, and conspirators conducted a SIM-swap attack to take over the identity of the person in…
Read MoreHere’s where nine solution provider top executives see as the biggest generative AI opportunities in the channel in 2025. Channel partners are bullish about the generative AI opportunities next year as customers still need more guidance around their artificial intelligence strategy and future. From AI advisory services to developing new GenAI offerings for customers, channel…
Read MoreNorth Korean IT professionals who trick Western companies into hiring them are stealing data from the organization’s network and asking for a ransom to not leak it. Dispatching IT workers to seek employment at companies in wealthier nations is a tactic that North Korea has been using for years as a means to obtain privileged…
Read More‘Public enemy number one and where [HPE] is trying to take over business is from Cisco. Even still, they have a long way to go and they are a ways behind Cisco,’ one partner tells CRN after the two CEOs took jabs at each other’s networking strategies this week at CRN parent The Channel Company’s…
Read MoreMeta admitted last month that it was using content posted to its flagship platforms Facebook and Instagram to train its new generative AI platform, named (unimaginatively) Meta AI. This came in the wake of major updates to its privacy policy in June which more or less drafted its roughly 3.5 billion person user base to…
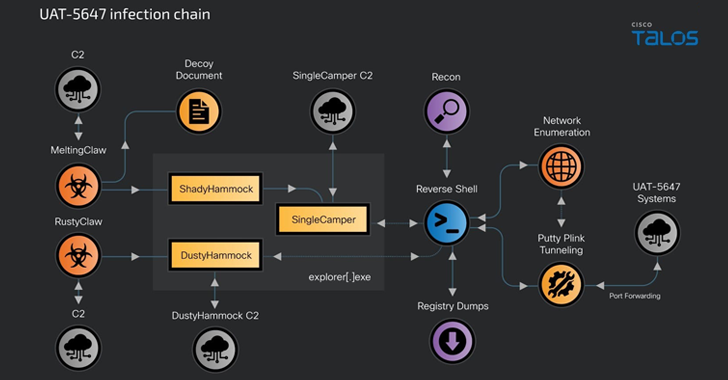
Read MoreOct 17, 2024Ravie LakshmananThreat Intelligence / Malware The Russian threat actor known as RomCom has been linked to a new wave of cyber attacks aimed at Ukrainian government agencies and unknown Polish entities since at least late 2023. The intrusions are characterized by the use of a variant of the RomCom RAT dubbed SingleCamper (aka…
Read MoreGoogle Cloud’s Kapase: Upcoming AI-Powered Chatbot In ‘Earnings Hub’ Will Make Partners’ Journey Easier
by nlqip
“[The chatbot will] help our partners have this integrated experience where they can go and get their questions answered, whether it’s go-to-market resources or … ‘I’m at this program level, I want to move to this next program level. What’s left for me to do to get there?’” Colleen Kapase, vice president of channels and…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day