Author: nlqip
Friday Squid Blogging: New Species of Squid Discovered A new species of squid was discovered, along with about a hundred other species. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid Posted on March…
Read MoreSecurity researchers have released technical details and a proof-of-concept (PoC) exploit for a critical vulnerability patched last week in Fortinet’s FortiClient Enterprise Management Server (FortiClient EMS), an endpoint security management solution. The vulnerability, tracked as CVE-2023-48788, was reported to Fortinet as a zero-day by the UK National Cyber Security Centre (NCSC) and was actively exploited…
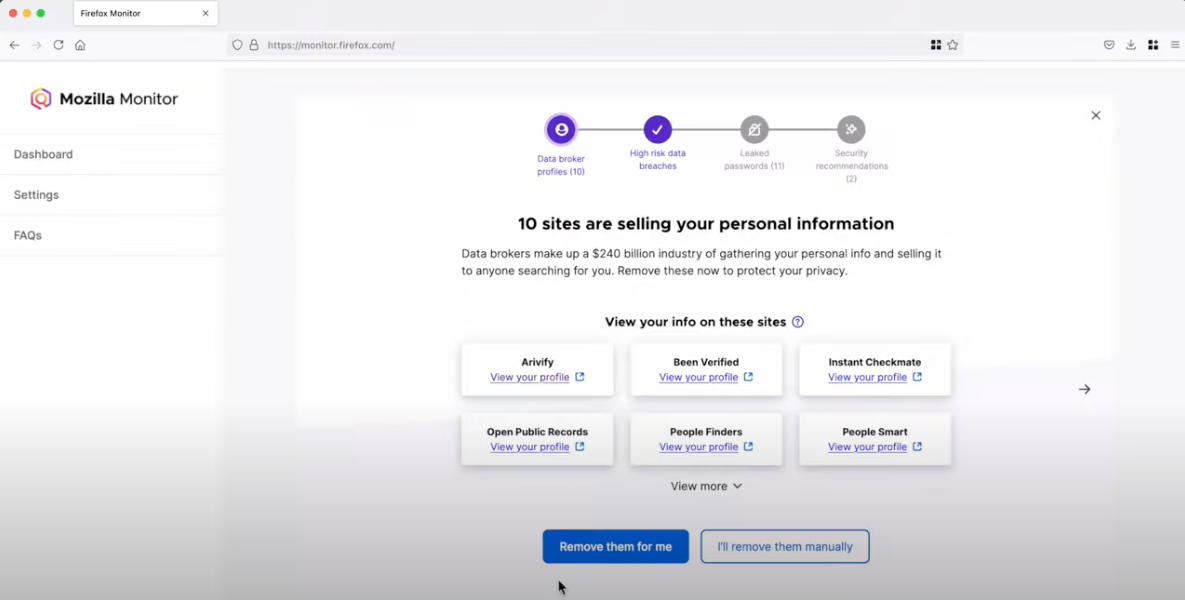
Read MoreMozilla Drops Onerep After CEO Admits to Running People-Search Networks – Krebs on Security
by nlqip
The nonprofit organization that supports the Firefox web browser said today it is winding down its new partnership with Onerep, an identity protection service recently bundled with Firefox that offers to remove users from hundreds of people-search sites. The move comes just days after a report by KrebsOnSecurity forced Onerep’s CEO to admit that he…
Read MoreCybersecurity researchers have detected a new wave of phishing attacks that aim to deliver an ever-evolving information stealer referred to as StrelaStealer. The campaigns impact more than 100 organizations in the E.U. and the U.S., Palo Alto Networks Unit 42 researchers said in a new report published today. “These campaigns come in the form of…
Read MoreMar 22, 2024NewsroomWeb Security / Vulnerability A massive malware campaign dubbed Sign1 has compromised over 39,000 WordPress sites in the last six months, using malicious JavaScript injections to redirect users to scam sites. The most recent variant of the malware is estimated to have infected no less than 2,500 sites over the past two months…
Read MoreMar 22, 2024NewsroomCyber Defense / Vulnerability A China-linked threat cluster leveraged security flaws in Connectwise ScreenConnect and F5 BIG-IP software to deliver custom malware capable of delivering additional backdoors on compromised Linux hosts as part of an “aggressive” campaign. Google-owned Mandiant is tracking the activity under its uncategorized moniker UNC5174 (aka Uteus or Uetus), describing…
Read MoreMar 22, 2024NewsroomAmazon Web Services / Vulnerability Cybersecurity researchers have shared details of a now-patched security vulnerability in Amazon Web Services (AWS) Managed Workflows for Apache Airflow (MWAA) that could be potentially exploited by a malicious actor to hijack victims’ sessions and achieve remote code execution on underlying instances. The vulnerability, now addressed by AWS,…
Read MoreThe US Cybersecurity and Infrastructure Security Agency (CISA), the FBI, and the multistate information sharing, and analysis center (MS-ISAC) have, in a joint effort, released an advisory to defend against distributed denial of service (DDoS) attacks. Especially popular with Russia-backed hacktivists and nation-state actors, DDoS attacks refer to malicious attempts to disrupt the normal traffic…
Read MoreThe ThreatLocker® Zero Trust Endpoint Protection Platform implements a strict deny-by-default, allow-by-exception security posture to give organizations the ability to set policy-based controls within their environment and mitigate countless cyber threats, including zero-days, unseen network footholds, and malware attacks as a direct result of user error. With the capabilities of the ThreatLocker® Zero Trust Endpoint…
Read MoreGoogle Pays $10M in Bug Bounties in 2023 BleepingComputer has the details. It’s $2M less than in 2022, but it’s still a lot. The highest reward for a vulnerability report in 2023 was $113,337, while the total tally since the program’s launch in 2010 has reached $59 million. For Android, the world’s most popular and…
Read More