Author: nlqip
Video We break down the fundamentals of threat intelligence and its role in anticipating and countering emerging threats 14 Mar 2024 The threat landscape is becoming ever more complex and perilous by the day. Adversaries, ranging from state-aligned advanced persistent threats (APTs) to opportunistic cybercriminals, are well-funded, adaptable and relentless, targeting various chinks in organizations’…
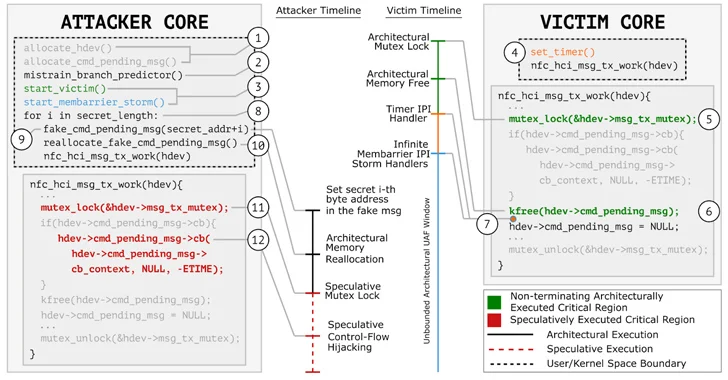
Read MoreMar 15, 2024NewsroomHardware Security / Data Protection A group of researchers has discovered a new data leakage attack impacting modern CPU architectures supporting speculative execution. Dubbed GhostRace (CVE-2024-2193), it is a variation of the transient execution CPU vulnerability known as Spectre v1 (CVE-2017-5753). The approach combines speculative execution and race conditions. “All the common synchronization…
Read MoreTwo firms have been fined $26 million by the US Federal Trade Commission (FTC) for scaring consumers into believing their computers were infected by malware. The FTC claimed that Restoro Cyprus Limited and Reimage Cyprus Limited, both based in Cyprus, operated a tech support scam since at least 2018 that “bilked tens of millions of…
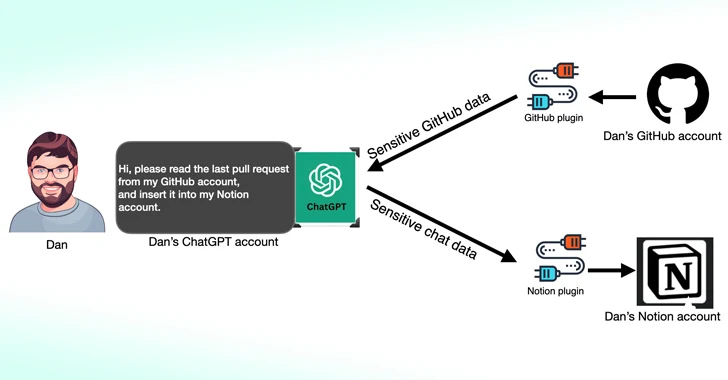
Read MoreMar 15, 2024NewsroomData Privacy / Artificial Intelligence Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act as a new attack surface for threat actors looking to gain unauthorized access to sensitive data. According to new research published by Salt Labs, security flaws found directly in ChatGPT and within the ecosystem could…
Read MoreImproving C++ C++ guru Herb Sutter writes about how we can improve the programming language for better security. The immediate problem “is” that it’s Too Easy By Default™ to write security and safety vulnerabilities in C++ that would have been caught by stricter enforcement of known rules for type, bounds, initialization, and lifetime language safety.…
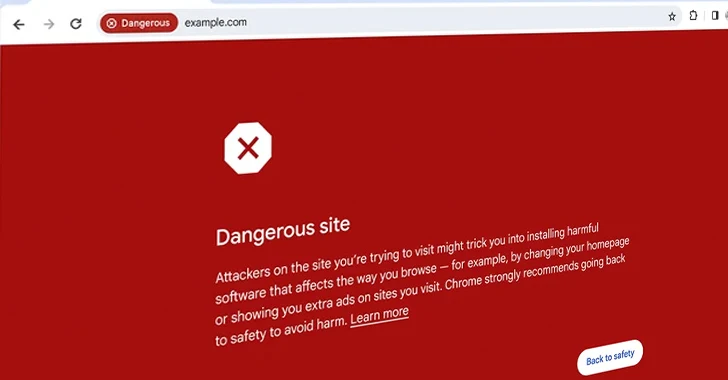
Read MoreMar 15, 2024NewsroomBrowser Security / Phishing Attack Google on Thursday announced an enhanced version of Safe Browsing to provide real-time, privacy-preserving URL protection and safeguard users from visiting potentially malicious sites. “The Standard protection mode for Chrome on desktop and iOS will check sites against Google’s server-side list of known bad sites in real-time,” Google’s…
Read MoreMar 15, 2024NewsroomMalvertising / Threat Intelligence Chinese users looking for legitimate software such as Notepad++ and VNote on search engines like Baidu are being targeted with malicious ads and bogus links to distribute trojanized versions of the software and ultimately deploy Geacon, a Golang-based implementation of Cobalt Strike. “The malicious site found in the notepad++…
Read MoreSecurity analysts receive thousands of alerts daily, and the onslaught is rapidly growing without any signs of slowing down. Meanwhile, cybersecurity talent is extremely difficult to recruit and retain. According to the ISC2 Cybersecurity Workforce Study 2023, the global cybersecurity workforce of about 5.5 million would need to almost double to meet the current need.…
Read MorePersistent threats such as business email compromise (BEC) necessitate an evolution of cybersecurity defenses to protect identities. Transitioning away from a reliance on authenticator apps and IP fencing toward a comprehensive zero-trust framework, incorporating FIDO2 security keys or passkeys, offers a path to more secure and user-friendly authentication experiences. By embracing these technologies, organizations can…
Read MoreHow To Here are a few tips for secure file transfers and what else to consider when sharing sensitive documents so that your data remains safe 13 Mar 2024 • , 4 min. read Our lives are increasingly lived in the digital world. And while this comes with a host of benefits, it also exposes…
Read MoreRecent Posts
- Seven Trends to Watch for in 2025
- Multiple Vulnerabilities in Ivanti Products Could Allow for Remote Code Execution
- Ivanti Releases Security Updates for Connect Secure, Policy Secure, and ZTA Gateways | CISA
- CISA Adds One Vulnerability to the KEV Catalog | CISA
- CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild