Author: nlqip
An Instant Guide on How to Install SSL Certificate on Apache Server Securing your website is like having a lock on your network that protects it from cyberattacks. SSL/TLS encryption is a communication lock between a web server and a browser. These encryptions ensure that sensitive information, such as passwords, and financial and personal data,…
Read MoreCheyenne, WY – March 14th, 2024 – BlackFog, the leader in ransomware protection and anti data exfiltration, today announces its wins in three categories at the 20th Annual 2024 Globee Awards. The Globee® Cybersecurity Awards, a leading authority in recognizing business excellence globally, has honored BlackFog for outstanding innovation and effectiveness in cybersecurity. The Globee Cybersecurity…
Read MoreMar 14, 2024NewsroomCyber Threat / Malware The threat actor known as Blind Eagle has been observed using a loader malware called Ande Loader to deliver remote access trojans (RATs) like Remcos RAT and NjRAT. The attacks, which take the form of phishing emails, targeted Spanish-speaking users in the manufacturing industry based in North America, eSentire…
Read MoreIn addition to having an inventory of existing tools in use, there also should be a process to onboard and offboard future tools and services from the organizational inventory securely. AI security and privacy training It’s often quipped that “humans are the weakest link,” however that doesn’t need to be the case if an organization…
Read MoreMar 14, 2024The Hacker NewsVulnerability / Network Security Fortinet has warned of a critical security flaw impacting its FortiClientEMS software that could allow attackers to achieve code execution on affected systems. “An improper neutralization of special elements used in an SQL Command (‘SQL Injection’) vulnerability [CWE-89] in FortiClientEMS may allow an unauthenticated attacker to execute…
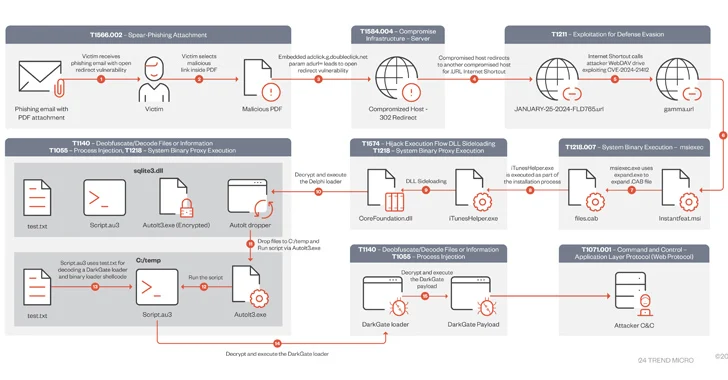
Read MoreMar 14, 2024NewsroomMalware / Cyber Attack A DarkGate malware campaign observed in mid-January 2024 leveraged a recently patched security flaw in Microsoft Windows as a zero-day using bogus software installers. “During this campaign, users were lured using PDFs that contained Google DoubleClick Digital Marketing (DDM) open redirects that led unsuspecting victims to compromised sites hosting…
Read MoreSmashing Security podcast #363: Stuck streaming sticks, TikTok conspiracies, and spying cars
by nlqip
Roku users are revolting after their TVs are bricked by the company, we learn how to make money through conspiracy videos on TikTok, and just how much is your car snooping on your driving? All this and much much more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham…
Read MoreAre you part of an organization that has made significant strides in the realm of cybersecurity? Do you believe your security projects and initiatives have demonstrated outstanding business value and thought leadership? If so, now is the time to showcase your achievements and gain recognition among your peers. The CSO50 Conference + Awards, scheduled for…
Read More“PowerShell allows users to evaluate values inside strings before they are used,” the researcher explained. “This can be done by adding $(<experssion_to_be_evaluated>) to your string […]. Any PowerShell command can be inserted between the parentheses and will be evaluated — such as $(Start-Process cmd), $(Invoke-Expression exp), and other PowerShell treats.” So, for example, if an…
Read MoreIntroducing Microsoft Copilot for Security The marriage of generative AI with proven security solutions can augment the work of security professionals by accelerating processing speeds and pattern detection to help gain an edge over cybercriminals. Sponsored by Microsoft Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreRecent Posts
- Ivanti Releases Security Updates for Connect Secure, Policy Secure, and ZTA Gateways | CISA
- CISA Adds One Vulnerability to the KEV Catalog | CISA
- CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild
- Google Cloud Hires Tech Superstar Francis DeSouza As New COO
- AWS Invests $11B In Georgia To ‘Support The Future Of AI’ Via Data Centers