Author: nlqip
CISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-21338 Microsoft Windows Kernel Exposed IOCTL with Insufficient Access Control Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the…
Read MoreNavigating the Dark Web, facilitated by specialized browsers like Tor, introduces significant risks and challenges for businesses. This hidden realm attracts various users, from ordinary individuals seeking online anonymity to cybercriminals actively engaging in illegal activities. Forums and marketplaces on the dark web facilitate criminal endeavors, offering a platform for the sale of hacking tools,…
Read MoreRansomware is one of the biggest cybersecurity threats facing businesses in the current environment. While this form of cyberattack has been around for a while, it has exploded in popularity among criminals in recent years. In 2023, it was reported by Verizon that almost a quarter of data breaches (24 percent) involved ransomware, while our…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Comprehending and effectively addressing cybersecurity threats is paramount to organizational security. As artificial intelligence continues to evolve, how companies respond to cybersecurity threats…
Read MoreCheyenne, Wyoming, March 4—BlackFog, the leader in ransomware protection and anti data exfiltration, has been honored with the Best Threat Intelligence Technology award from teissAwards2024. This award highlights BlackFog’s ongoing commitment to safeguarding an organizations most valuable asset, its data, from the latest AI based threats. The teiss awards celebrate excellence in cyber and information…
Read MoreCybercriminals are using a network of hired money mules in India using an Android-based application to orchestrate a massive money laundering scheme. The malicious application, called XHelper, is a “key tool for onboarding and managing these money mules,” CloudSEK researchers Sparsh Kulshrestha, Abhishek Mathew, and Santripti Bhujel said in a report. Details about the scam…
Read MoreThe capability is developed by leveraging a combination of heuristics and proprietary AI layers to evaluate prompts and identify abuses and threats. “Firewall for AI will protect against Model Denial of Service and Sensitive Information Disclosure, which leverage tools and features available to all customers as part of the Web Application Firewall,” the Cloudflare spokesperson said.…
Read MoreMar 04, 2024The Hacker NewsSaaS Security / Vulnerability Assessment A company’s lifecycle stage, size, and state have a significant impact on its security needs, policies, and priorities. This is particularly true for modern mid-market companies that are either experiencing or have experienced rapid growth. As requirements and tasks continue to accumulate and malicious actors remain…
Read MoreLLM Prompt Injection Worm Researchers have demonstrated a worm that spreads through prompt injection. Details: In one instance, the researchers, acting as attackers, wrote an email including the adversarial text prompt, which “poisons” the database of an email assistant using retrieval-augmented generation (RAG), a way for LLMs to pull in extra data from outside its…
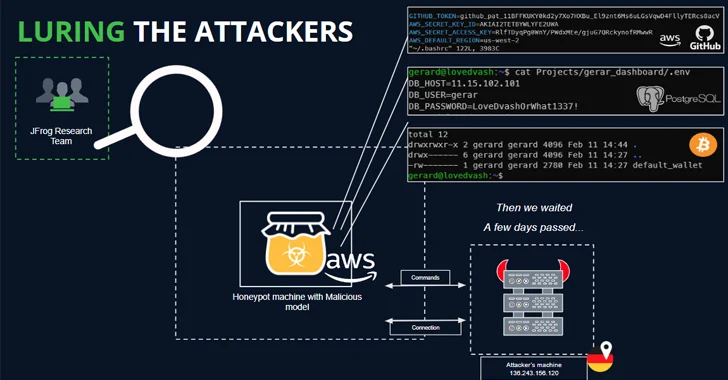
Read MoreMar 04, 2024NewsroomAI Security / Vulnerability As many as 100 malicious artificial intelligence (AI)/machine learning (ML) models have been discovered in the Hugging Face platform. These include instances where loading a pickle file leads to code execution, software supply chain security firm JFrog said. “The model’s payload grants the attacker a shell on the compromised…
Read MoreRecent Posts
- Seven Trends to Watch for in 2025
- Multiple Vulnerabilities in Ivanti Products Could Allow for Remote Code Execution
- Ivanti Releases Security Updates for Connect Secure, Policy Secure, and ZTA Gateways | CISA
- CISA Adds One Vulnerability to the KEV Catalog | CISA
- CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild