Author: nlqip
Last year, the Open Worldwide Application Security Project (OWASP) published multiple versions of the “OWASP Top 10 For Large Language Models,” reaching a 1.0 document in August and a 1.1 document in October. These documents not only demonstrate the rapidly evolving nature of Large Language Models, but the evolving ways in which they can be…
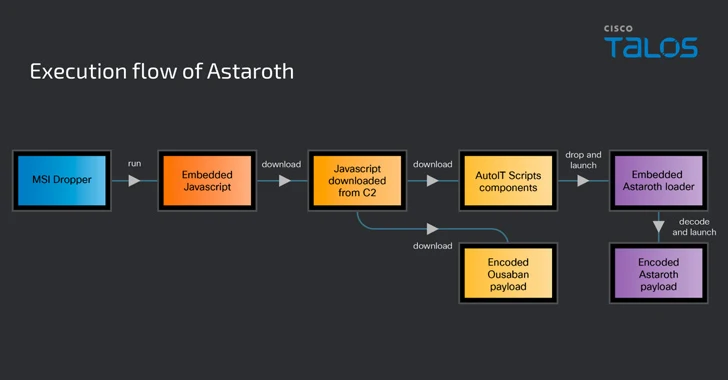
Read MoreCybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka Guildma), Mekotio, and Ousaban (aka Javali) to targets across Latin America (LATAM) and Europe. “The infection chains associated with these malware families feature the use of malicious…
Read MoreCommunication skills are some of the most fundamental learned in life. Whether in written, verbal, non-verbal, or visual form, the ability to communicate clearly and effectively is quickly becoming a top prerequisite for cybersecurity jobs. In fact, it’s become so highly valued that Hays’ first global cybersecurity report, released in 2023, identified communication as one…
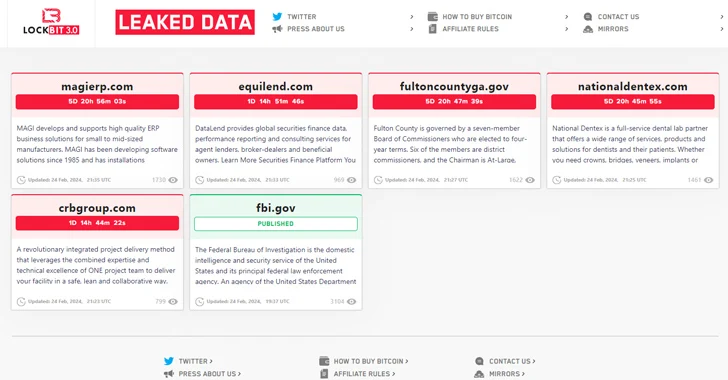
Read MoreThe threat actors behind the LockBit ransomware operation have resurfaced on the dark web using new infrastructure, days after an international law enforcement exercise seized control of its servers. To that end, the notorious group has moved its data leak portal to a new .onion address on the TOR network, listing 12 new victims as…
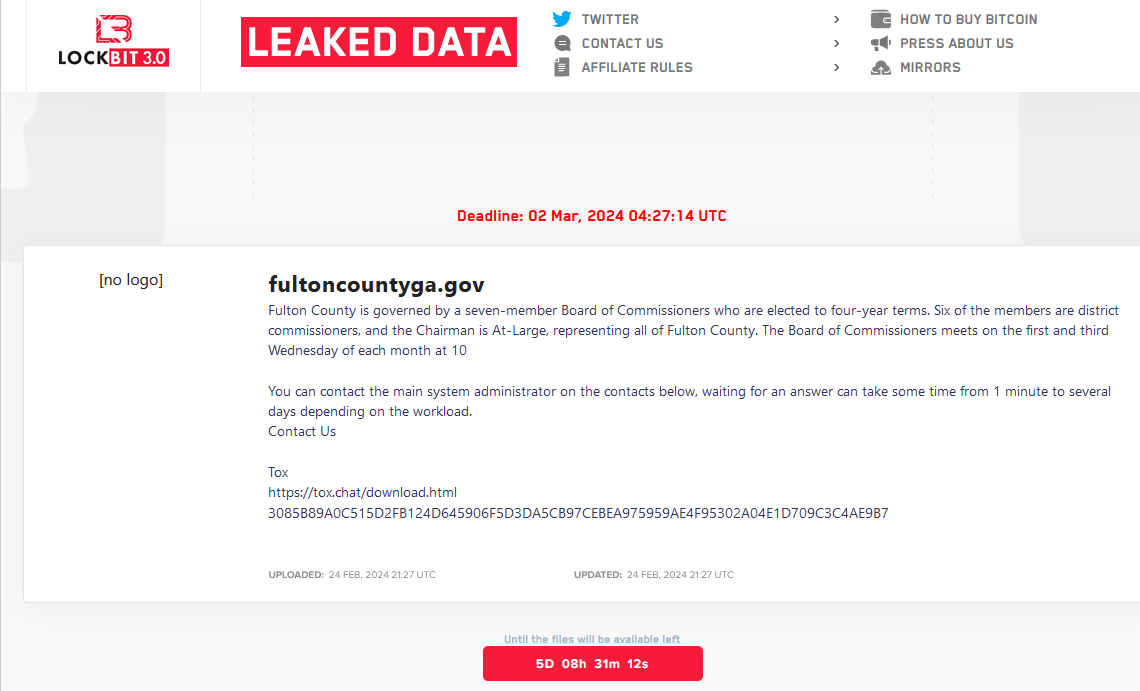
Read MoreFBI’s Lockbit Takedown Postponed a Ticking Time Bomb in Fulton County, Ga. – Krebs on Security
by nlqip
The FBI’s takedown of the LockBit ransomware group last week came as LockBit was preparing to release sensitive data stolen from government computer systems in Fulton County, Ga. But LockBit is now regrouping, and the gang says it will publish the stolen Fulton County data on March 2 unless paid a ransom. LockBit claims the…
Read MoreLockBitSupp, the individual(s) behind the persona representing the LockBit ransomware service on cybercrime forums such as Exploit and XSS, “has engaged with law enforcement,” authorities said. The development comes following the takedown of the prolific ransomware-as-a-service (RaaS) operation as part of a coordinated international operation codenamed Cronos. Over 14,000 rogue accounts on third-party services like…
Read MoreFeb 24, 2024NewsroomActive Directory / Data Protection Microsoft has expanded free logging capabilities to all U.S. federal agencies using Microsoft Purview Audit irrespective of the license tier, more than six months after a China-linked cyber espionage campaign targeting two dozen organizations came to light. “Microsoft will automatically enable the logs in customer accounts and increase…
Read MoreVideo Coming in two waves, the campaign sought to demoralize Ukrainians and Ukrainian speakers abroad with disinformation messages about war-related subjects 23 Feb 2024 This week, ESET researchers revealed their findings about Operation Texonto, a disinformation/psychological (PSYOP) campaign where Russia-aligned threat actors sought to demoralize Ukrainians and Ukrainian speakers abroad with disinformation messages about war-related…
Read MoreToday, CISA, the Environmental Protection Agency (EPA), and the Federal Bureau of Investigation (FBI) updated the joint fact sheet Top Cyber Actions for Securing Water Systems. This update includes additional resources—from American Water Works Association, the WaterISAC, and MS-ISAC—to support water systems in defending against from malicious cyber activity. The fact sheet outlines the following…
Read MoreFriday Squid Blogging: Illex Squid and Climate Change There are correlations between the populations of the Illex Argentines squid and water temperatures. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid Posted on February…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm