Author: nlqip
Today, CISA, the Environmental Protection Agency (EPA), and the Federal Bureau of Investigation (FBI) released the joint fact sheet Top Cyber Actions for Securing Water Systems. This fact sheet outlines the following practical actions Water and Wastewater Systems (WWS) Sector entities can take to better protect water systems from malicious cyber activity and provides actionable…
Read MoreMozilla released security updates to address vulnerabilities in Firefox, Firefox ESR, and Thunderbird. A cyber threat actor could exploit one of these vulnerabilities to take control of an affected system. CISA encourages users and administrators to review the following Mozilla Security Advisories and apply the necessary updates: Source link ddde ddde ddde ddde ddde ddde…
Read MoreThis article provides a comprehensive look at crypters, software that disguises malware to evade antivirus detection. The discussion covers the basic operations of crypters, their increasing use in cybercrime, as well as the specifics of how PolyCrypt functions. Any tool or technique that promotes secrecy is music to the ears of dubious malicious attackers, who…
Read MoreTelikom LimitedIndustry: TelecommunicationsCountry: Papua New GuineaLocations: 22Employees: 1000+Web: Telikom.com.pg Download PDF Telikom Limited is the leading telecommunications company in the South Pacific region operating its own leading systems and technology. It offers both retail and wholesale voice & data broadband services, through its entirely digital network and extensive optical fibre systems spanning over five decades. At Telikom…
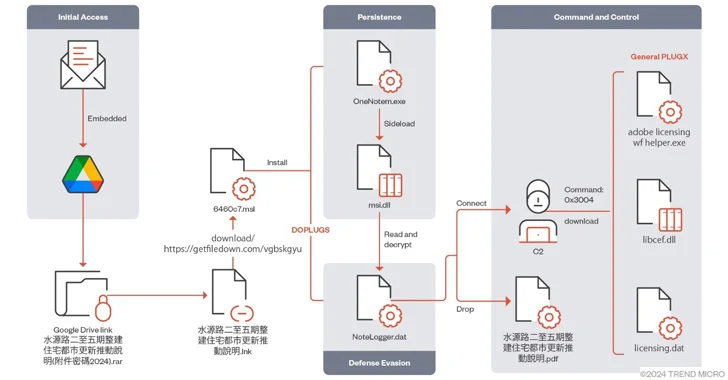
Read MoreFeb 21, 2024NewsroomMalware / Cyber Espionage The China-linked threat actor known as Mustang Panda has targeted various Asian countries using a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS. “The piece of customized PlugX malware is dissimilar to the general type of the PlugX malware that contains a completed backdoor command module, and that…
Read More“In terms of phishing, while I believe that the threat remains in the critical category for organizations, because many phishing campaigns seek account credentials as the primary outcome, if cybercriminals have access to valid account credentials via other means (as noted in the report), the need to run a phishing campaign will decline,” said Michael Sampson,…
Read MoreThis article looks at ransomware trends of 2023, such as an increase in supply chain attacks, the use of double extortion, law enforcement actions against large networks, a focus on small and medium-sized businesses more than ever and calls for payments to be banned in lieu of ransomware. 1. Double Extortion Became a Key Tactic…
Read MoreWith SaaS applications now making up the vast majority of technology used by employees in most organizations, tasks related to identity governance need to happen across a myriad of individual SaaS apps. This presents a huge challenge for centralized IT teams who are ultimately held responsible for managing and securing app access, but can’t possibly…
Read MoreDetails of a Phone Scam First-person account of someone who fell for a scam, that started as a fake Amazon service rep and ended with a fake CIA agent, and lost $50,000 cash. And this is not a naive or stupid person. The details are fascinating. And if you think it couldn’t happen to you,…
Read MoreCompany: Bonanza CasinoIndustry: GamingCountry: Reno, NevadaEmployees: 150+Web: bonanzacasino.com Download PDF A favorite with Reno locals, the Bonanza Casino, a family owned and operated business, first opened its doors in 1973. The casino is home to two restaurants, the Cactus Creek Prime Steakhouse, ten-time “Best of Nevada” winner and the Branding Iron Café. As an independent boutique casino,…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm