Author: nlqip
CISA and MS-ISAC Release Advisory on Compromised Account Used to Access State Government Organization | CISA
by nlqip
Today, CISA and the Multi-State Information Sharing & Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory (CSA), Threat Actor Leverages Compromised Account of Former Employee to Access State Government Organization to provide network defenders with the tactics, techniques, and procedures (TTPs) utilized by a threat actor and methods to protect against similar exploitation. Following an incident…
Read MoreThreat Actor Leverages Compromised Account of Former Employee to Access State Government Organization | CISA
by nlqip
SUMMARY The Cybersecurity and Infrastructure Security Agency (CISA) and the Multi-State Information Sharing & Analysis Center (MS-ISAC) conducted an incident response assessment of a state government organization’s network environment after documents containing host and user information, including metadata, were posted on a dark web brokerage site. Analysis confirmed that an unidentified threat actor compromised network…
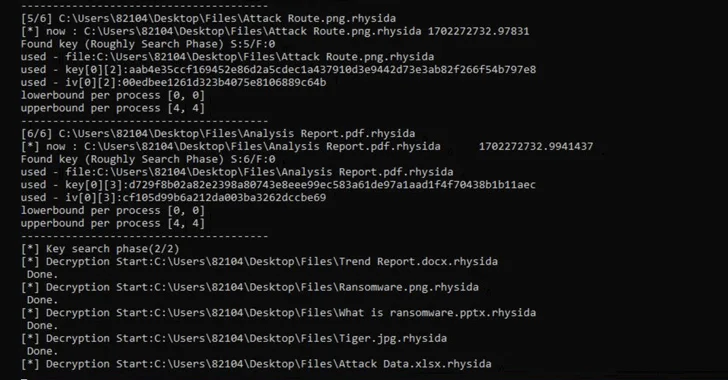
Read MoreGood news for organisations who have fallen victim to the notorious Rhysida ransomware. A group of South Korean security researchers have uncovered a vulnerability in the infamous ransomware. This vulnerability provides a way for encrypted files to be unscrambled. Researchers from Kookmin University describe how they exploited an implementation flaw in Rhysida’s code to regenerate…
Read MoreA reverse engineering of the firmware running on Ivanti Pulse Secure appliances has revealed numerous weaknesses, once again underscoring the challenge of securing software supply chains. Eclypsiusm, which acquired firmware version 9.1.18.2-24467.1 as part of the process, said the base operating system used by the Utah-based software company for the device is CentOS 6.4. “Pulse…
Read MoreFeb 15, 2024NewsroomMalware / Cyber Espionage The Russia-linked threat actor known as Turla has been observed using a new backdoor called TinyTurla-NG as part of a three-month-long campaign targeting Polish non-governmental organizations in December 2023. “TinyTurla-NG, just like TinyTurla, is a small ‘last chance’ backdoor that is left behind to be used when all other…
Read MoreApart from the visibility it provides into an organization’s sensitive permissions and exposed data, the capability is also aimed at assisting with the organization’s remediation efforts. “BigID’s access governance capability doesn’t just detect overexposed data and overprivileged accounts, it also goes one step further,” Young added.“It can help facilitate access remediation management and actions by natively…
Read MoreOn the Insecurity of Software Bloat Good essay on software bloat and the insecurities it causes. The world ships too much code, most of it by third parties, sometimes unintended, most of it uninspected. Because of this, there is a huge attack surface full of mediocre code. Efforts are ongoing to improve the quality of…
Read MoreHow Nation-State Actors Target Your Business: New Research Exposes Major SaaS Vulnerabilities
by nlqip
Feb 15, 2024The Hacker NewsSaaS Security / Risk Management With many of the highly publicized 2023 cyber attacks revolving around one or more SaaS applications, SaaS has become a cause for genuine concern in many boardroom discussions. More so than ever, considering that GenAI applications are, in fact, SaaS applications. Wing Security (Wing), a SaaS…
Read More‘Cyber insecurity’ is among the most pressing issues facing organizations globally in 2024, according to new research from the World Economic Forum (WEF). In its Global Cybersecurity Outlook 2024 report, the WEF found that more than eight in ten organizations surveyed feel more or as exposed to cyber crime than last year. How can businesses implement…
Read MoreA Chinese-speaking threat actor codenamed GoldFactory has been attributed to the development of highly sophisticated banking trojans, including a previously undocumented iOS malware called GoldPickaxe that’s capable of harvesting identity documents, facial recognition data, and intercepting SMS. “The GoldPickaxe family is available for both iOS and Android platforms,” Singapore-headquartered Group-IB said in an extensive report…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA