Author: nlqip
Oct 14, 2024Ravie LakshmananRansomware / Vulnerability Threat actors are actively attempting to exploit a now-patched security flaw in Veeam Backup & Replication to deploy Akira and Fog ransomware. Cybersecurity vendor Sophos said it has been tracking a series of attacks in the past month leveraging compromised VPN credentials and CVE-2024-40711 to create a local account…
Read MoreUsing Anti Data Exfiltration (ADX) to Stop Ransomware and Other Threats to Data Dr. EDWARD AMOROSO, FOUNDER & CEO, TAG This series of blogs developed by TAG Infosphere highlights a powerful new cybersecurity solution known as Anti Data Exfiltration (ADX) which provides on-device data security and threat protection. Commercial vendor BlackFog pioneered ADX which is…
Read MoreGoogle’s Chrome Web Store is now warning that the uBlock Origin ad blocker and other extensions may soon be blocked as part of the company’s deprecation of the Manifest V2 extension specification. “This extension may soon no longer be supported because it doesn’t follow best practices for Chrome extensions,” reads the Chrome Web Store page for…
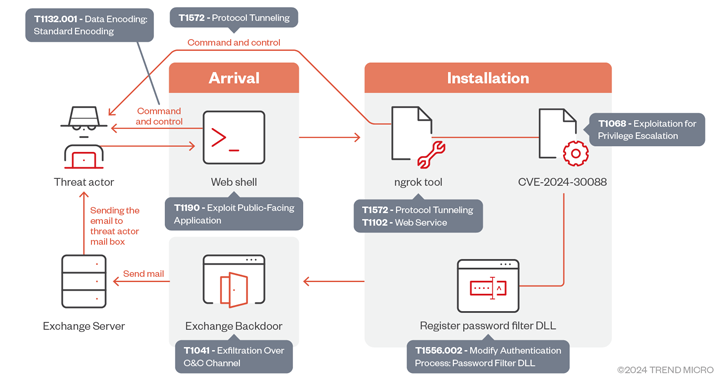
Read MoreThe Iranian state-sponsored hacking group APT34, aka OilRig, has recently escalated its activities with new campaigns targeting government and critical infrastructure entities in the United Arab Emirates and the Gulf region. In these attacks, spotted by Trend Micro researchers, OilRig deployed a novel backdoor, targeting Microsoft Exchange servers to steal credentials, and also exploited the Windows…
Read MoreOct 13, 2024Ravie Lakshmanan The Iranian threat actor known as OilRig has been observed exploiting a now-patched privilege escalation flaw impacting the Windows Kernel as part of a cyber espionage campaign targeting the U.A.E. and the broader Gulf region. “The group utilizes sophisticated tactics that include deploying a backdoor that leverages Microsoft Exchange servers for…
Read MoreVideo ESET research dives deep into a series of attacks that leveraged bespoke toolsets to compromise air-gapped systems belonging to governmental and diplomatic entities 11 Oct 2024 This week, ESET researchers published the results of their probe into a series of attacks that leveraged bespoke toolsets to compromise air-gapped systems belonging to governmental and diplomatic…
Read MoreOpenAI has disrupted over 20 malicious cyber operations abusing its AI-powered chatbot, ChatGPT, for debugging and developing malware, spreading misinformation, evading detection, and conducting spear-phishing attacks. The report, which focuses on operations since the beginning of the year, constitutes the first official confirmation that generative mainstream AI tools are used to enhance offensive cyber operations.…
Read MoreMicrosoft has officially deprecated the Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling Protocol (L2TP) in future versions of Windows Server, recommending admins switch to different protocols that offer increased security. For over 20 years, the enterprise has used the PPTP and L2TP VPN protocols to provide remote access to corporate networks and Windows servers.…
Read MoreOct 12, 2024Ravie LakshmananCryptocurrency / Cybercrime The U.S. Department of Justice (DoJ) has announced arrests and charges against several individuals and entities in connection with allegedly manipulating digital asset markets as part of a widespread fraud operation. The law enforcement action – codenamed Operation Token Mirrors – is the result of the U.S. Federal Bureau…
Read More“Seamlessly integrated into your experience, the AI assistant continues your conversation as you navigate through Partner Center,” according to Microsoft. Microsoft is previewing an artificial intelligence-powered assistant in its Partner Center with capabilities ranging from support ticket creation to quick answers. The Partner Center AI assistant – notably not called a “copilot,” Microsoft’s typical name…
Read MoreRecent Posts
- QNAP addresses critical flaws across NAS, router software
- New Windows 10 0x80073CFA fix requires installing WinAppSDK 3 times
- Blue Yonder ransomware attack disrupts grocery store supply chain
- DOJ: Man hacked networks to pitch cybersecurity services
- Microsoft blocks Windows 11 24H2 on some PCs with USB scanners