Author: nlqip
Today’s AI PCs are moving power-hungry, GPU-driven AI training and inference tasks, leading to potential big performance and sustainability gains. Today’s AI PCs are moving some of the power-hungry, GPU-driven AI training and inference tasks from the data center to the edge, leading to potential big performance and sustainability gains. HP Inc. and Dell Technologies…
Read MoreIn today’s cybersecurity landscape, evolving threats require security solutions that match the sophistication of modern threats. As businesses rapidly adopt emerging technologies, their exposure to cyberattacks increases. To mitigate these risks, cybersecurity teams need adaptable and comprehensive tools to protect their digital ecosystems effectively. Security Information and Event Management (SIEM) and Extended Detection and Response…
Read MoreA group of pro-Ukrainian hacktivists has claimed responsibility for the September breach of Russian security company Doctor Web (Dr.Web). Dr.Web confirmed last month that its network was breached on September 14, which forced it to disconnect all internal servers and stop pushing virus database updates to customers while investigating the incident. In a Tuesday Telegram…
Read MoreCISA has added three new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-23113 Fortinet Multiple Products Format String Vulnerability CVE-2024-9379 Ivanti Cloud Services Appliance (CSA) SQL Injection Vulnerability CVE-2024-9380 Ivanti Cloud Services Appliance (CSA) OS Command Injection Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant…
Read MoreOct 09, 2024Ravie LakshmananIndustrial Security / Critical Infrastructure Details have emerged about multiple security vulnerabilities in two implementations of the Manufacturing Message Specification (MMS) protocol that, if successfully exploited, could have severe impacts in industrial environments. “The vulnerabilities could allow an attacker to crash an industrial device or in some cases, enable remote code execution,”…
Read MoreAn international law enforcement operation led to the arrest of one of the three administrators of the dual dark web market ‘Bohemia/Cannabia,’ known for hosting ads for drug sales and distributed denial of service (DDoS) attacks. The man was arrested at the Schiphol airport in Amsterdam on June 27, 2024, and electronic devices containing incriminating…
Read MoreWe’ve collected details on the biggest product announcements and acquisitions by major SASE vendors this year. Big Moves In SASE With security and networking continuing to converge and remote access remaining a necessity for many organizations, the momentum around SASE (secure access service edge) continues to grow. As just one indicator, Gartner analysts recently forecast…
Read MoreOct 09, 2024Ravie LakshmananPhishing Attack / Malware Threat actors with ties to North Korea have been observed targeting job seekers in the tech industry to deliver updated versions of known malware families tracked as BeaverTail and InvisibleFerret. The activity cluster, tracked as CL-STA-0240, is part of a campaign dubbed Contagious Interview that Palo Alto Networks…
Read MoreThe new Cloudera AI Inference Service leverages Nvidia NIM microservices to boost the development of large-scale AI models that can tap into the huge volumes of data stored on the Cloudera Data Platform. Data platform provider Cloudera is taking a deeper dive into AI with a new service, powered by Nvidia’s NIM microservices, for deploying…
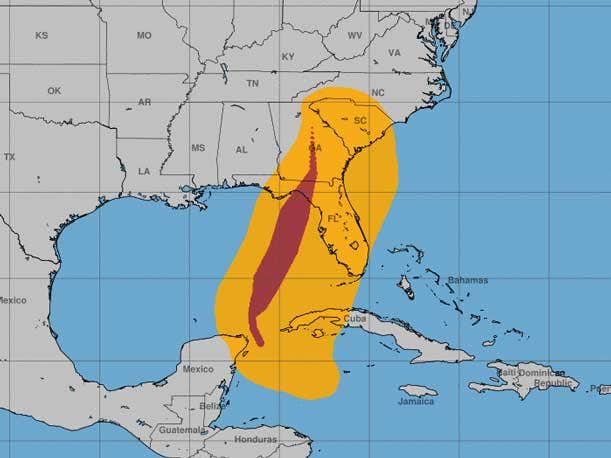
Read MoreHere’s how some solution providers, vendors and distributors have been helping customers, employees and individuals living in the areas impacted by Hurricane Helene and how they’re preparing for the impact of Hurricane Milton. Source link lol
Read More