Category: AI in news
Paul Robichaux, senior director of product management at cloud security vendor Keepit, agreed that Microsoft’s decision not to address the vulnerability was reasonable. “I think Microsoft called this one correctly. This isn’t nothing, but it’s not a big deal either. It is a theoretical vulnerability if you’re using Azure service tags as a single point…
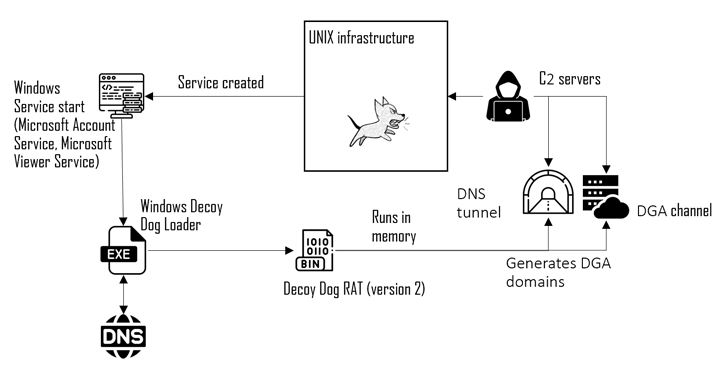
Read MoreJun 04, 2024NewsroomCyber Attack / Malware Russian organizations are at the receiving end of cyber attacks that have been found to deliver a Windows version of a malware called Decoy Dog. Cybersecurity company Positive Technologies is tracking the activity cluster under the name Operation Lahat, attributing it to an advanced persistent threat (APT) group called…
Read MoreBy ARC Labs contributor, Shannon Mong ARC Labs recently analyzed a sample of the Wineloader backdoor for infection chain analysis and detection opportunities to help defenders protect their organizations. Through this analysis, ARC Labs is providing defenders with general detection guidance and specific KQL queries to detect Wineloader activity within Microsoft Sentinel. Additionally, ARC Labs has provided…
Read MoreJun 04, 2024The Hacker NewsBrowser Security / Enterprise Security The landscape of browser security has undergone significant changes over the past decade. While Browser Isolation was once considered the gold standard for protecting against browser exploits and malware downloads, it has become increasingly inadequate and insecure in today’s SaaS-centric world. The limitations of Browser Isolation,…
Read MoreFix includes updating to the latest version The vulnerability affects versions 5.2, 7.19.0, 7.20.0, 8.0.0, 8.1.0, 8.2.0, 8.3.0, 8.4.0, 8.5.0, 8.6.0, 8.8.0, 8.7.1, 8.9.0 of Confluence Data Center as well as Atlassian Server. Fixes for the flawed software are included in the versions 8.9.1, 8.5.9, and 7.19.22, patching all the affected versions. “Atlassian recommends that Confluence Server…
Read MoreCVE-2024-4358, CVE-2024-1800: Exploit Code Available for Critical Exploit Chain in Progress Telerik Report Server
by nlqip
Researchers have released an exploit chain to achieve remote code execution on unpatched instances of Progress Telerik Report Server. Immediate patching is recommended. Background On May 31, security researcher Sina Kheirkhah of the Summoning Team posted on X (formerly known as Twitter) the discovery of an exploit chain involving two vulnerabilities in Progress Telerik Report…
Read MoreBreaking a Password Manager Interesting story of breaking the security of the RoboForm password manager in order to recover a cryptocurrency wallet password. Grand and Bruno spent months reverse engineering the version of the RoboForm program that they thought Michael had used in 2013 and found that the pseudo-random number generator used to generate passwords…
Read MoreRepresentative attack vectors to simulate a wide range of attacks relevant to your company. Realistic attack scenarios that are similar to what attackers are actually using, using frameworks such as MITRE ATT&CK. Customizable scenarios to test unique aspects of your infrastructure. Automated testing so that the simulations can run regularly and efficiently without impacting operations…
Read MoreIs CISM worth it? CISM salary CISM certification involves a number of steps, so the obvious question arises: Is it worth it? If you’re interested in a management position — and the higher salaries such positions command — earning a CISM certification is a great way to signal your expertise, as well as your seriousness…
Read MoreJun 04, 2024NewsroomNetwork Security / Cryptocurrency The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting the Oracle WebLogic Server to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. Tracked as CVE-2017-3506 (CVSS score: 7.4), the issue concerns an operating system (OS) command injection vulnerability that could…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’