Category: AI in news
Seeing Like a Data Structure Technology was once simply a tool—and a small one at that—used to amplify human intent and capacity. That was the story of the industrial revolution: we could control nature and build large, complex human societies, and the more we employed and mastered technology, the better things got. We don’t live…
Read MoreJun 03, 2024NewsroomEndpoint Security / Vulnerability Now-patched authorization bypass issues impacting Cox modems that could have been abused as a starting point to gain unauthorized access to the devices and run malicious commands. “This series of vulnerabilities demonstrated a way in which a fully external attacker with no prerequisites could’ve executed commands and modified the…
Read MoreJun 03, 2024NewsroomMalware / Cyber Attack The North Korea-linked threat actor known as Andariel has been observed using a new Golang-based backdoor called Dora RAT in its attacks targeting educational institutes, manufacturing firms, and construction businesses in South Korea. “Keylogger, Infostealer, and proxy tools on top of the backdoor were utilized for the attacks,” the…
Read MoreDevelopers, engineers, and end users across the organization and broader ecosystem often create NHIs and grant them access without a deep understanding of the implications of these long-lived credentials, their level of access, and their potential exploitation by malicious actors — without the governance or involvement of security teams. The implications of this is manifesting…
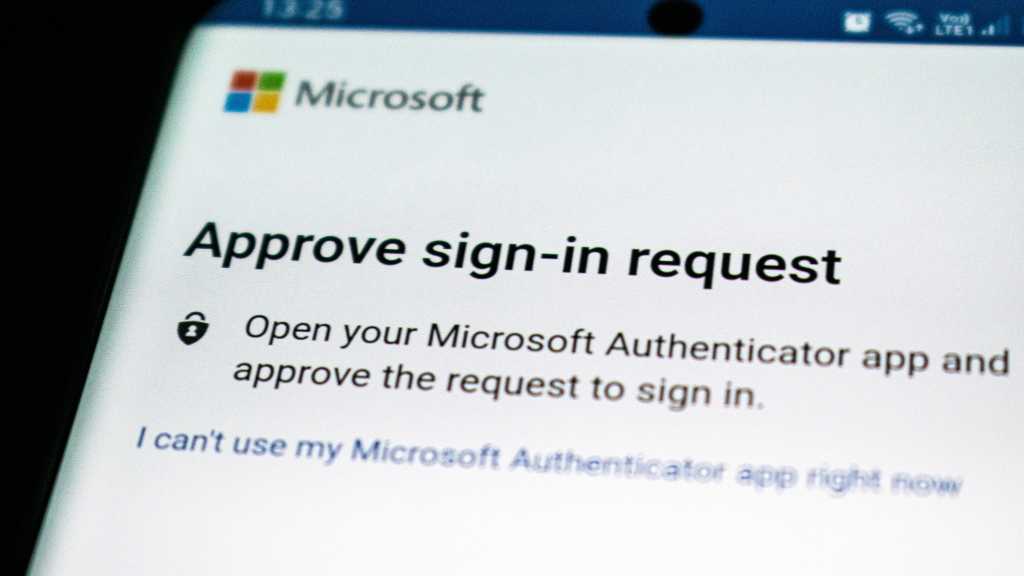
Read MoreWhat Cisco Talos researches found was that the most frequently imitated brand worldwide by cybercriminals was by far Microsoft, followed by DocuSign and Amazon in second and third place. PayPal, Adobe, and Instagram also rank in the top 10, along with Nortonlifelock, Chase, Geek Squad, and Home Depot, according to Cisco Talos. The illegal use…
Read MoreFake web browser updates are being used to deliver remote access trojans (RATs) and information stealer malware such as BitRAT and Lumma Stealer (aka LummaC2). “Fake browser updates have been responsible for numerous malware infections, including those of the well-known SocGholish malware,” cybersecurity firm eSentire said in a new report. “In April 2024, we observed…
Read MoreJun 01, 2024NewsroomAI-as-a-Service / Data Breach Artificial Intelligence (AI) company Hugging Face on Friday disclosed that it detected unauthorized access to its Spaces platform earlier this week. “We have suspicions that a subset of Spaces’ secrets could have been accessed without authorization,” it said in an advisory. Spaces offers a way for users to create,…
Read MoreStalkerware app pcTattletale announces it is ‘out of business’ after suffering data breach and website defacement
by nlqip
US spyware vendor pcTattletale has shut down its operations following a serious data breach that exposed sensitive information about its customers, as well as data stolen from some of their victims. pcTattletale was promoted as “employee and child monitoring software” designed to “protect your business and family.” Of course, what it actually was, was a…
Read MoreFriday Squid Blogging: Baby Colossal Squid This video might be a juvenile colossal squid. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid, video Posted on May 31, 2024 at 5:02 PM • 0…
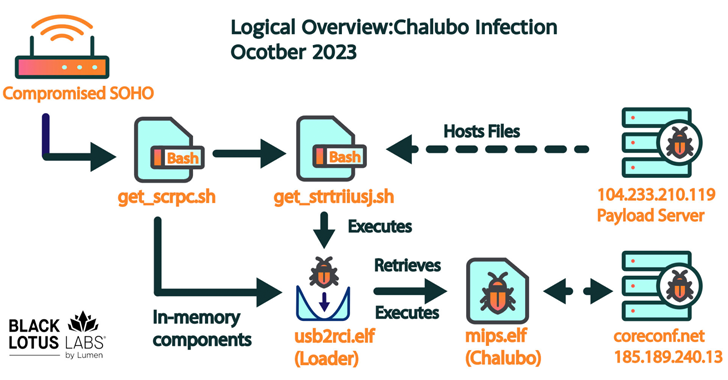
Read MoreMay 31, 2024NewsroomNetwork Security / Cyber Attack More than 600,000 small office/home office (SOHO) routers are estimated to have been bricked and taken offline following a destructive cyber attack staged by unidentified cyber actors, disrupting users’ access to the internet. The mysterious event, which took place between October 25 and 27, 2023, and impacted a…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’