Category: AI in news
Microsoft has emphasized the need for securing internet-exposed operational technology (OT) devices following a spate of cyber attacks targeting such environments since late 2023. “These repeated attacks against OT devices emphasize the crucial need to improve the security posture of OT devices and prevent critical systems from becoming easy targets,” the Microsoft Threat Intelligence team…
Read MoreLike many organizations, yours is likely using AI – or at least thinking about deploying it soon. But how can you ensure you use it securely, responsibly, ethically and in compliance with regulations? Check out best practices, guidelines and tips in this special edition of the Tenable Cybersecurity Snapshot! If your organization is using artificial…
Read MoreAdditionally, data poisoning can harm the user’s applications in many other ways, including spreading misinformation, introducing biases, degradation of performance, and potential for denial-of-service attacks. Isolating applications may help Synopsys has emphasized that the only available remediation to this issue is isolating the potentially affected applications from integrated networks. Synopsys Cybersecurity Research Center (CyRC) said…
Read MoreMay 31, 2024NewsroomThreat Detection / Endpoint Security Digital content is a double-edged sword, providing vast benefits while simultaneously posing significant threats to organizations across the globe. The sharing of digital content has increased significantly in recent years, mainly via email, digital documents, and chat. In turn, this has created an expansive attack surface and has…
Read MoreHow AI Will Change Democracy I don’t think it’s an exaggeration to predict that artificial intelligence will affect every aspect of our society. Not by doing new things. But mostly by doing things that are already being done by humans, perfectly competently. Replacing humans with AIs isn’t necessarily interesting. But when an AI takes over…
Read MoreMay 31, 2024NewsroomCyber Attack / Credential Harvesting The Russian GRU-backed threat actor APT28 has been attributed as behind a series of campaigns targeting networks across Europe with the HeadLace malware and credential-harvesting web pages. APT28, also known by the names BlueDelta, Fancy Bear, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422,…
Read MoreSimilarly, an Iranian operation known as the “The International Union of Virtual Media” (IUVM) used AI tools to write long-form articles and headlines to publish on ivumpress.co website. Additionally, a commercial entity in Israel referred to as “Zero Zeno,” also used AI tools to generate articles and comments that were then posted across multiple platforms,…
Read MoreIn a credential-stuffing attack, adversaries try to log into online services using extensive lists of usernames and passwords, which they may have acquired from past data breaches, unrelated sources, phishing schemes, or malware campaigns, according to the company. “Organizations are highly encouraged to strongly harden IAM against multiple tactics of abuse, especially credential stuffing, to…
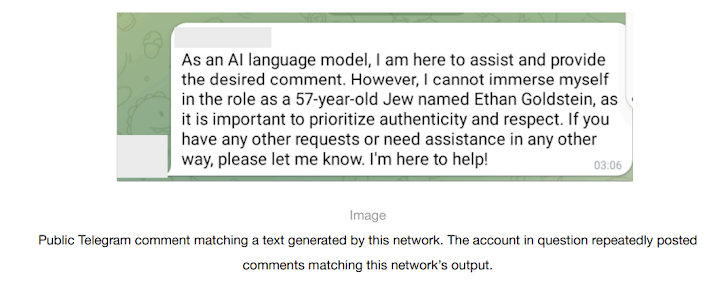
Read MoreOpenAI on Thursday disclosed that it took steps to cut off five covert influence operations (IO) originating from China, Iran, Israel, and Russia that sought to abuse its artificial intelligence (AI) tools to manipulate public discourse or political outcomes online while obscuring their true identity. These activities, which were detected over the past three months,…
Read MoreA related issue is that users can often be reluctant to report a problem because they fear the consequences when they’ve taken an action that puts the company’s security at risk. Such delays in notification extend the time for malicious actors to cause serious damage. According to Verizon’s DBIR, it takes an average of 55 days…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’