Category: AI in news
Another 38% of apps inside government organizations have vulnerabilities that are not yet one-year old but can become security debt if left unfixed and only 3% are completely free of known flaws, compared to 6% across other sectors. “So, while (slightly) fewer public sector organizations have security debt, they tend to accumulate more of it,”…
Read MoreSecurity leaders are in a tricky position trying to discern how much new AI-driven cybersecurity tools could actually benefit a security operations center (SOC). The hype about generative AI is still everywhere, but security teams have to live in reality. They face constantly incoming alerts from endpoint security platforms, SIEM tools, and phishing emails reported…
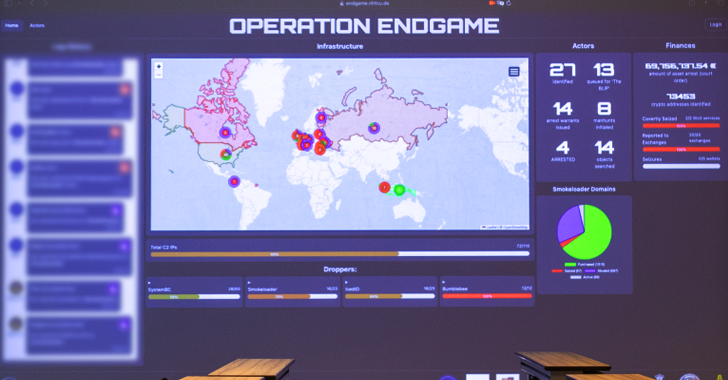
Read MoreMay 30, 2024NewsroomMalware / Cyber Crime Europol on Thursday said it shut down the infrastructure associated with several malware loader operations such as IcedID, SystemBC, PikaBot, SmokeLoader, Bumblebee, and TrickBot as part of a coordinated law enforcement effort codenamed Operation Endgame. “The actions focused on disrupting criminal services through arresting High Value Targets, taking down…
Read MoreSupply Chain Attack against Courtroom Software No word on how this backdoor was installed: A software maker serving more than 10,000 courtrooms throughout the world hosted an application update containing a hidden backdoor that maintained persistent communication with a malicious website, researchers reported Thursday, in the latest episode of a supply-chain attack. The software, known…
Read MoreWang allegedly managed approximately 150 dedicated servers worldwide, 76 of which he had leased from US-based service providers. “Using the dedicated servers, Wang deployed and managed applications, commanded and controlled the infected devices, operated his 911 S5 service, and provided paying customers with access to proxied IP addresses associated with the infected devices,” the Justice…
Read MoreThe U.S. Department of Justice (DoJ) on Wednesday said it dismantled what it described as “likely the world’s largest botnet ever,” which consisted of an army of 19 million infected devices that was leased to other threat actors to commit a wide array of offenses. The botnet, which has a global footprint spanning more than…
Read MoreEffective security awareness training The emphasis here is should probably be on effective. That’s because, according to Arctic Wolf, 88% of companies worldwide already have some form of IT security training in place, and another 10% are in the process of introducing such a program within the next 12 months. But not all security awareness training programs are equal.…
Read MoreMicrosoft Defender for Cloud Apps: Microsoft Defender for Cloud Apps is a full-featured CASB focused on protection for SaaS applications. It includes shadow IT discovery, visibility into cloud app usage, protection against app-based threats, information protection, and compliance assessments. Advanced capabilities include SaaS security posture management (SSPM), which enables security teams to improve the organization’s…
Read MoreThe U.S. Department of Justice (DOJ) today said they arrested the alleged operator of 911 S5, a ten-year-old online anonymity service that was powered by what the director of the FBI called “likely the world’s largest botnet ever.” The arrest coincided with the seizure of the 911 S5 website and supporting infrastructure, which the government…
Read MoreNetwork support: Ensure that your network infrastructure, including access points and controllers, support WPA3 and (if desired) the optional OWE for Open Networks. While many newer network devices are WPA3-compatible, older hardware may require updates or replacements. If you’re wanting to utilize certain optional functionality in WPA3, do the research and consider all requirements for…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’