Category: AI in news
Memcyco Report Reveals Only 6% Of Brands Can Protect Their Customers From Digital Impersonation Fraud
by nlqip
Memcyco Inc., provider of digital trust technology designed to protect companies and their customers from digital impersonation fraud, released its inaugural 2024 State of Website Impersonation Scams report. Notably, Memcyco’s research indicates that the majority of companies do not have adequate solutions to counter digital impersonation fraud, and that most only learn about attacks from…
Read MoreMay 23, 2024NewsroomEndpoint Security / Data Privacy Microsoft on Wednesday outlined its plans to deprecate Visual Basic Script (VBScript) in the second half of 2024 in favor of more advanced alternatives such as JavaScript and PowerShell. “Technology has advanced over the years, giving rise to more powerful and versatile scripting languages such as JavaScript and…
Read MoreSmashing Security podcast #373: iPhone undeleted photos, and stealing Scarlett Johansson’s voice
by nlqip
iPhone photos come back from the dead! Scarlett Johansson sounds upset about GPT-4o, and there’s a cockup involving celebrity fakes. All this and much more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham Cluley and Carole Theriault, joined this week by special guest Anna Brading of Malwarebytes. Plus!…
Read MoreIn July that year, NIST selected four encryption algorithms to become part of the agency’s post-quantum cryptographic standard. At the time, Secretary of Commerce Gina M. Raimondo welcomed the announcement, hailing it is “an important milestone in securing our sensitive data against the possibility of future cyberattacks from quantum computers,” and saying, “Thanks to NIST’s…
Read MoreThe Microsoft Azure CTO revealed that just by changing 1% of the data set — for example, using a backdoor — an attacker could cause a model to misclassify items or produce malware. Some of these data poisoning efforts are easily demonstrated, such as the effect of adding just a small amount of digital noise…
Read MoreCybersecurity researchers have disclosed details of a previously undocumented threat group called Unfading Sea Haze that’s believed to have been active since 2018. The intrusion singled out high-level organizations in South China Sea countries, particularly military and government targets, Bitdefender said in a report shared with The Hacker News. “The investigation revealed a troubling trend…
Read More23-year-old alleged founder of dark web Incognito Market arrested after FBI tracks cryptocurrency payments
by nlqip
The United States Department of Justice has dealt a blow to dark web drug traffickers by arresting a man alleged to operate the dark web drugs marketplace Incognito Market. According to a DOJ press release, the alleged operator of a darknet platform sold over $100 million worth of narcotics worldwide. 23-year-old Rui-Siang Lin (also known…
Read MoreMay 22, 2024NewsroomICS Security / Vulnerability Rockwell Automation is urging its customers to disconnect all industrial control systems (ICSs) not meant to be connected to the public-facing internet to mitigate unauthorized or malicious cyber activity. The company said it’s issuing the advisory due to “heightened geopolitical tensions and adversarial cyber activity globally.” To that end,…
Read MoreUnredacting Pixelated Text Experiments in unredacting text that has been pixelated. Tags: redaction, steganography Posted on May 22, 2024 at 7:03 AM • 0 Comments Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
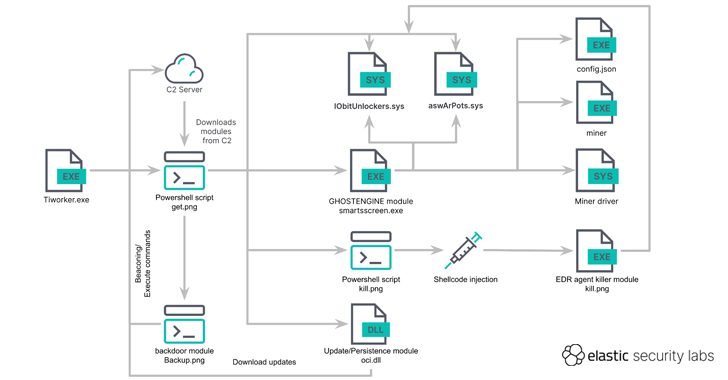
Read MoreCybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart detection in what’s called a Bring Your Own Vulnerable Driver (BYOVD) attack. Elastic Security Labs is tracking the campaign under the name REF4578 and the primary payload as GHOSTENGINE. Previous research from Chinese cybersecurity firm…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher