Category: AI in news
To many, Kubernetes is a black box that’s difficult to understand, manage and secure. If you’re using stateful persistent volumes – cloud resources that live and manage data outside the scope of your pods – it can be even darker. Many organizations use stateful persistent volumes to provide stable storage for certain applications, such as…
Read More‘Over the last 25 years, how many times have the analysts come and said print is dead. Print is declining. It’s shifting. It’s not going away. I don’t believe in our lifetime we’re going to see it disappear completely. And as a dealer, you just have to be ready to adapt to whatever changes. And…
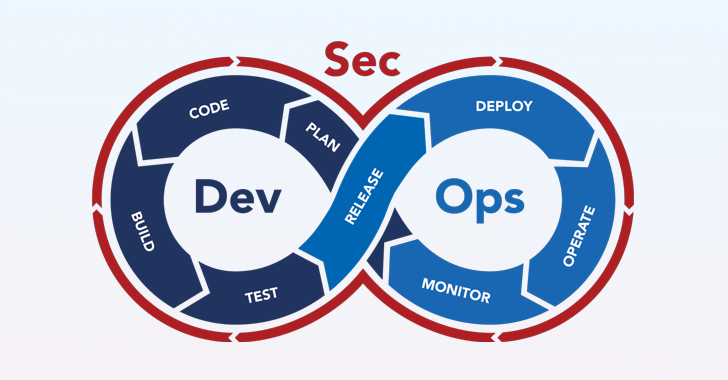
Read MoreOne of the enduring challenges of building modern applications is to make them more secure without disrupting high-velocity DevOps processes or degrading the developer experience. Today’s cyber threat landscape is rife with sophisticated attacks aimed at all different parts of the software supply chain and the urgency for software-producing organizations to adopt DevSecOps practices that…
Read MoreDetecting Malicious Trackers From Slashdot: Apple and Google have launched a new industry standard called “Detecting Unwanted Location Trackers” to combat the misuse of Bluetooth trackers for stalking. Starting Monday, iPhone and Android users will receive alerts when an unknown Bluetooth device is detected moving with them. The move comes after numerous cases of trackers…
Read MoreMay 21, 2024NewsroomWindows 11 Security Microsoft on Monday confirmed its plans to deprecate NT LAN Manager (NTLM) in Windows 11 in the second half of the year, as it announced a slew of new security measures to harden the widely-used desktop operating system. “Deprecating NTLM has been a huge ask from our security community as…
Read MoreMay 21, 2024NewsroomHealthcare / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a security flaw impacting NextGen Healthcare Mirth Connect to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The flaw, tracked as CVE-2023-43208 (CVSS score: N/A), concerns a case of unauthenticated remote code execution arising from an…
Read MoreMay 21, 2024NewsroomCyber Attack / API Security Cybersecurity researchers have discovered a critical security flaw in a popular logging and metrics utility called Fluent Bit that could be exploited to achieve denial-of-service (DoS), information disclosure, or remote code execution. The vulnerability, tracked as CVE-2024-4323, has been codenamed Linguistic Lumberjack by Tenable Research. It impacts versions…
Read MoreWatch for discontent in the shadows When it comes to IRM, CISOs focus predominantly on technologies: user entity behavior analytics (UEBA), security information and event management (SIEM), data loss prevention, and the like. There isn’t as much emphasis on stepping outside the view of their colleagues as streams of user data, to instead see them…
Read MoreWith its acquisition of Locuz, slated to close during the third quarter, SHI gains an 800-person team with extensive experience in CloudOps, SecOps, HPCOps, AIOps, and insight as a service. Global IT solution provider SHI International Monday said it plans to acquire India-based Locuz Enterprise Solutions, a provider of cybersecurity and digital transformation services. With…
Read MoreFrom the editors of Network World, this enterprise buyer’s guide helps network and security IT staff understand the issues their organizations face around protecting corporate data in a hybrid cloud environment and how to choose the right solution. Source link lol
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher