Category: AI in news
Linguistic Lumberjack: Attacking Cloud Services via Logging Endpoints (Fluent Bit – CVE-2024-4323)
by nlqip
Tenable Research has discovered a critical memory corruption vulnerability dubbed Linguistic Lumberjack in Fluent Bit, a core component in the monitoring infrastructure of many cloud services. Key takeaways Fluent Bit is a logging utility heavily used by all major cloud providers. Tenable Research discovered a critical vulnerability dubbed Linguistic Lumberjack (CVE-2024-4323) within Fluent Bit’s built-in…
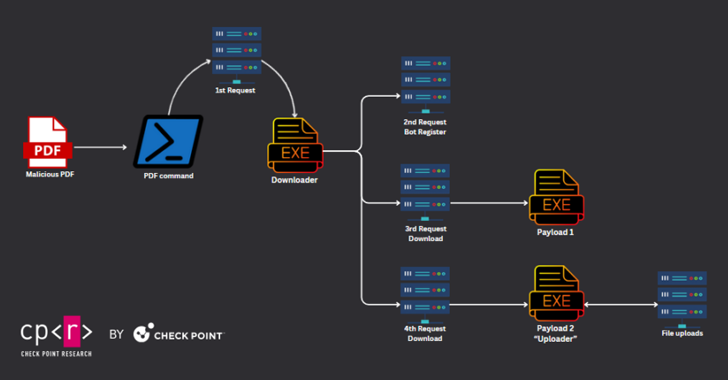
Read MoreMultiple threat actors are weaponizing a design flaw in Foxit PDF Reader to deliver a variety of malware such as Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm. “This exploit triggers security warnings that could deceive unsuspecting users into executing harmful commands,” Check Point said in a technical report. “This exploit…
Read MoreIBM Sells Cybersecurity Group IBM is selling its QRadar product suite to Palo Alto Networks, for an undisclosed—but probably surprisingly small—sum. I have a personal connection to this. In 2016, IBM bought Resilient Systems, the startup I was a part of. It became part if IBM’s cybersecurity offerings, mostly and weirdly subservient to QRadar. That…
Read More“On the other hand, several China-aligned threat actors exploited vulnerabilities in public-facing appliances, such as VPNs and firewalls, and software, such as Confluence and Microsoft Exchange Server, for initial access to targets in multiple verticals,” the researchers wrote. “North Korea-aligned groups continued to target aerospace and defense companies and the cryptocurrency industry.” Russia-aligned APT groups…
Read MoreMay 20, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have observed a spike in email phishing campaigns starting early March 2024 that delivers Latrodectus, a nascent malware loader believed to be the successor to the IcedID malware. “These campaigns typically involve a recognizable infection chain involving oversized JavaScript files that utilize WMI’s ability to invoke msiexec.exe…
Read More“When you go to the combatant commands, they’re, of course, worried that you’re standing up a new combatant command with separate authorities, and how will that work? A big part of our outreach was going to those combatant commands and talking about how Cybercom would support them as opposed to how Cybercom would be supported.…
Read MoreThe U.S. Department of Justice (DoJ) has charged two arrested Chinese nationals for allegedly orchestrating a pig butchering scam that laundered at least $73 million from victims through shell companies. The individuals, Daren Li, 41, and Yicheng Zhang, 38, were arrested in Atlanta and Los Angeles on April 12 and May 16, respectively. The foreign…
Read MoreMay 19, 2024NewsroomBanking Troja / Email Security The threat actors behind the Windows-based Grandoreiro banking trojan have returned in a global campaign since March 2024 following a law enforcement takedown in January. The large-scale phishing attacks, likely facilitated by other cybercriminals via a malware-as-a-service (MaaS) model, target over 1,500 banks across the world, spanning more…
Read MoreFriday Squid Blogging: Emotional Support Squid When asked what makes this an “emotional support squid” and not just another stuffed animal, its creator says: They’re emotional support squid because they’re large, and cuddly, but also cheerfully bright and derpy. They make great neck pillows (and you can fidget with the arms and tentacles) for travelling,…
Read MoreNissan North America has revealed that extortionists who demanded a ransom after breaking into its external VPN and disrupted systems last year also stole the social security numbers of over 53,000 staff. The security breach occurred on November 7, 2023. Upon initial investigation, Nissan and external experts brought in by the firm found that although…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher