Category: AI in news
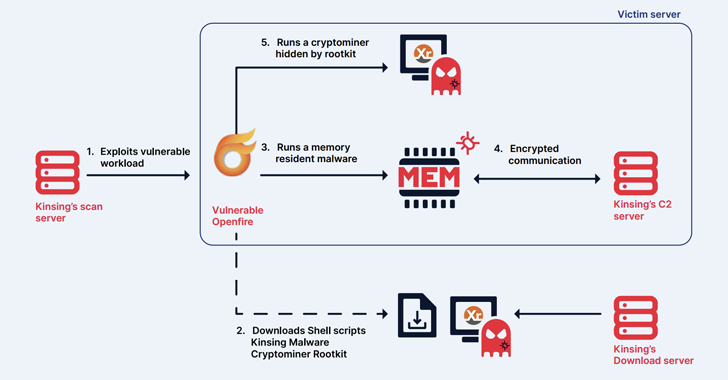
May 17, 2024NewsroomCryptojacking / Malware The cryptojacking group known as Kinsing has demonstrated its ability to continuously evolve and adapt, proving to be a persistent threat by swiftly integrating newly disclosed vulnerabilities to exploit arsenal and expand its botnet. The findings come from cloud security firm Aqua, which described the threat actor as actively orchestrating…
Read MoreOne SEC Commissioner, Hester Peirce, voted for the new rule, but expressed concerns it might generate notification fatigue, which could lead to people eventually ignoring all security notifications. “My greatest concern about the rule is that its breadth could undermine the value of the customer notifications by making them so commonplace that people ignore them.…
Read MoreCybersecurity Snapshot: CISA Warns Hospitals about Black Basta, as Tenable Study Finds Cloud-Related Breaches Pervasive
by nlqip
Find out why healthcare organizations must beware of the Black Basta ransomware group. Meanwhile, a Tenable study found that 95% of surveyed organizations suffered a cloud-related breach, and offers insights for boosting cloud security. Plus, a Cloud Security Alliance report delves into how AI systems can create risky gaps in your cloud environment. And much…
Read MoreA new report from XM Cyber has found – among other insights – a dramatic gap between where most organizations focus their security efforts, and where the most serious threats actually reside. The new report, Navigating the Paths of Risk: The State of Exposure Management in 2024, is based on hundreds of thousands of attack…
Read MoreFBI Seizes BreachForums Website The FBI has seized the BreachForums website, used by ransomware criminals to leak stolen corporate data. If law enforcement has gained access to the hacking forum’s backend data, as they claim, they would have email addresses, IP addresses, and private messages that could expose members and be used in law enforcement…
Read MoreIn general, though, the best way to mitigate against DDoS attacks is to simply have the capacity to withstand large amounts of inbound traffic. Depending on your situation, that might mean beefing up your own network, or making use of a content delivery network (CDN), a service designed to accommodate huge amounts of traffic. Your…
Read MoreMay 17, 2024NewsroomLinux / Malware The Kimsuky (aka Springtail) advanced persistent threat (APT) group, which is linked to North Korea’s Reconnaissance General Bureau (RGB), has been observed deploying a Linux version of its GoBear backdoor as part of a campaign targeting South Korean organizations. The backdoor, codenamed Gomir, is “structurally almost identical to GoBear, with…
Read More“It is vital that communication over the internet remains secure,” Rosenworcel said in the statement. “Although there have been efforts to help mitigate BGP’s security risks since its original design, more work needs to be done. With this proposal, we would require broadband providers to report to the FCC on their efforts to implement industry…
Read MoreMay 17, 2024NewsroomVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two security flaws impacting D-Link routers to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The list of vulnerabilities is as follows – CVE-2014-100005 – A cross-site request forgery (CSRF) vulnerability impacting D-Link DIR-600…
Read MoreTo meet the requirements, most public companies take proactive measures to ensure they have systems in place to assess, evaluate, and respond to incidents. “Unfortunately, in many cases, these processes are established outside of the operational resilience framework, and as a result, they are not integrated with the company’s crisis management program,” says Nolan, who…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher