Category: AI in news
Security researchers have warned about a new cyberespionage campaign that targets artificial intelligence experts working in private industry, government and academia. The attackers, likely of Chinese origin, are using a remote access trojan (RAT) called SugarGh0st. “The timing of the recent campaign coincides with an 8 May 2024 report from Reuters, revealing that the US…
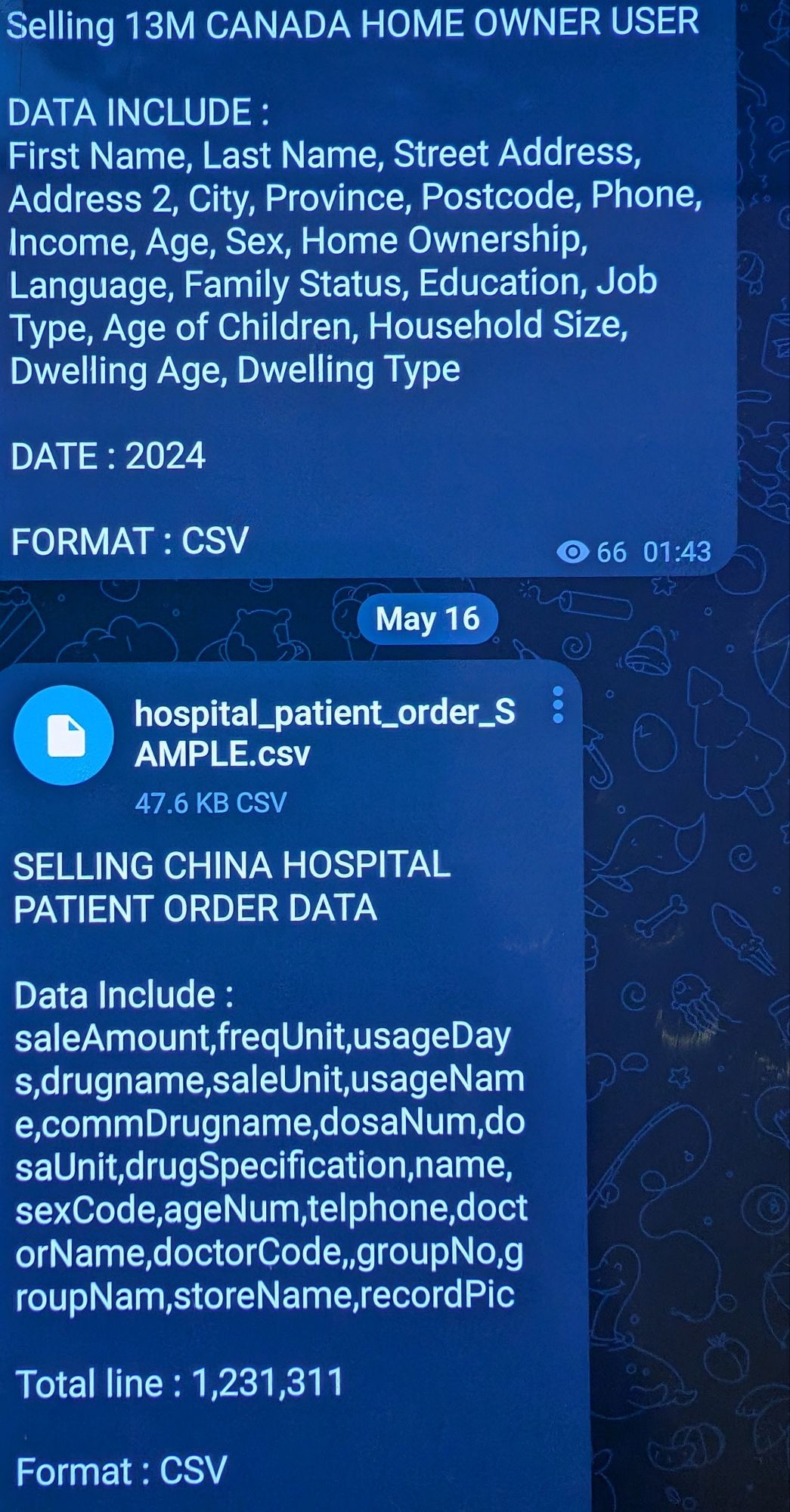
Read MoreIn a Telegram group, two important data advertised by threat actors. The first one is 13 million pieces of Canadian homeowners’ PII. It is claimed that the data includes first name, last name, street Address, address 2, city, province, postal code, phone, income, age, sex, home ownership, language, family status, education, job type, age of…
Read MoreScreenshots for PuTTY BleepingComputer Review: PuTTY is a Windows client for several remote shell protocols such as SSH and Telnet. Included in the installer are auxilliary utilities to generate PuTTY-compatible keyfiles for password-less login. PuTTY is the premier Windows utility for administering remote computers via simple command line. Visitors Also Liked: Source link lol
Read MoreMay 16, 2024NewsroomVulnerability / Network Security Researchers have discovered a new security vulnerability stemming from a design flaw in the IEEE 802.11 Wi-Fi standard that tricks victims into connecting to a less secure wireless network and eavesdrop on their network traffic. The SSID Confusion attack, tracked as CVE-2023-52424, impacts all operating systems and Wi-Fi clients,…
Read MoreThe move is still good news for CSOs looking to better manage application security, she stressed, just not necessarily industry-moving. “They are absolutely solving a problem but I don’t think the marketplace aspect of it is that interesting. I think they wanted to highlight 100 integrations out of the box. That is solid and it…
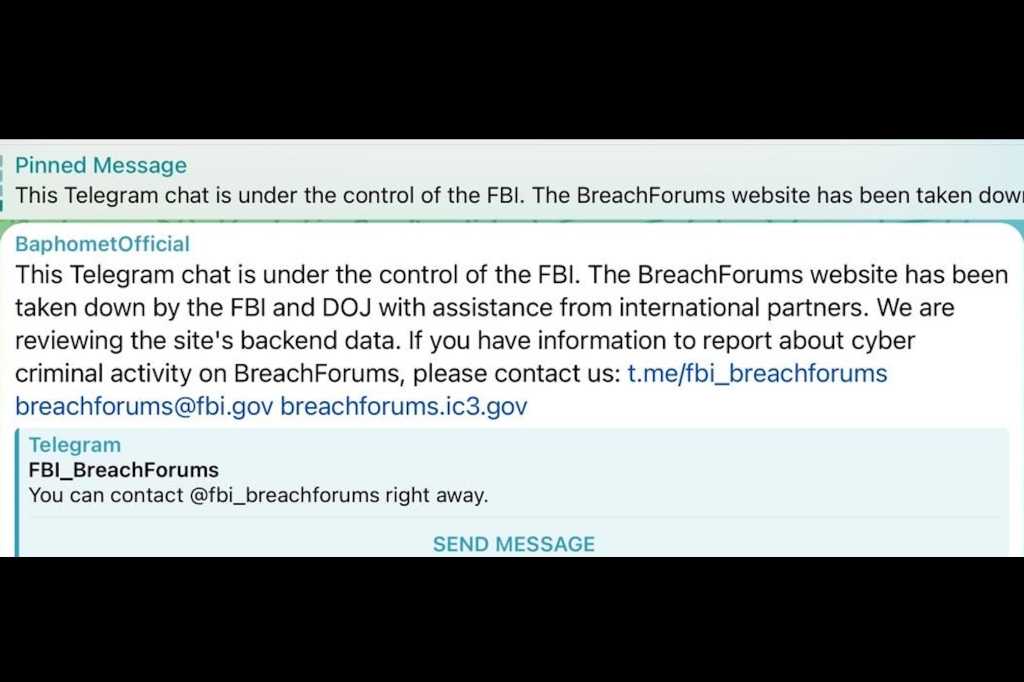
Read MoreBreachForums seized! One of the world’s largest hacking forums is taken down by the FBI… again
by nlqip
Law enforcement agencies worldwide have coordinated to take down one of the world’s largest hacker forums, scoring a victory against cybercrime. BreachForums, a notorious marketplace for stolen data, was seized by the authorities on Wednesday, according to a message on its website. BREACHFORUMS IS UNDER THE CONTROL OF THE FBIThis website has been taken…
Read MoreThe seizure comes two days after IntelBroker, a prominent hacker on BreachForums, put up for sale some classified data stolen from one of Europol’s websites. The FBI’s claim that it is reviewing the hacking forum’s backend data is raising speculation regarding its possession of forum members’ email addresses, IP addresses, and private messages. “While details…
Read MoreThe International Monetary Fund (IMF) Managing Director, Kristalina Georgieva, has sounded the alarm about the potentially disruptive impact of artificial intelligence (AI) on the global workforce. Speaking at a conference in London, Georgieva predicted a coming “tsunami” of job losses, driven by the rapid advancement of AI technologies. Georgieva’s warning highlights a growing concern among…
Read MoreBackground Cloud cryptomining has become an emerging trend in recent years, powered by the scalability and flexibility of cloud platforms. Unlike traditional on-premises infrastructure, cloud infrastructure allows attackers to quickly deploy resources for cryptomining, making it easier to exploit. One of the most common cryptomining threats for cloud environments is the Kinsing malware. Kinsing is…
Read MoreZero-Trust DNS Microsoft is working on a promising-looking protocol to lock down DNS. ZTDNS aims to solve this decades-old problem by integrating the Windows DNS engine with the Windows Filtering Platform—the core component of the Windows Firewall—directly into client devices. Jake Williams, VP of research and development at consultancy Hunter Strategy, said the union of…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher