Category: AI in news
Security researchers have disclosed almost a dozen security flaws impacting the GE HealthCare Vivid Ultrasound product family that could be exploited by malicious actors to tamper with patient data and even install ransomware under certain circumstances. “The impacts enabled by these flaws are manifold: from the implant of ransomware on the ultrasound machine to the…
Read MoreTo meet the requirements, most public companies take proactive measures to ensure they have systems in place to assess, evaluate, and respond to incidents. “Unfortunately, in many cases, these processes are established outside of the operational resilience framework, and as a result, they are not integrated with the company’s crisis management program,” says Nolan, who…
Read MoreMay 16, 2024NewsroomBrowser Security / Vulnerability Google has rolled out fixes to address a set of nine security issues in its Chrome browser, including a new zero-day that has been exploited in the wild. Assigned the CVE identifier CVE-2024-4947, the vulnerability relates to a type confusion bug in the V8 JavaScript and WebAssembly engine. It…
Read MoreIn addition to QakBot, the Kaspersky researchers have seen other payloads deployed with the exploit for the new CVE-2024-30051 vulnerability, including the Cobalt Strike beacon. As a result, Kaspersky has concluded that the exploit is currently known and being used by multiple groups. It’s worth noting that CVE-2024-30051 cannot be used to gain initial access.…
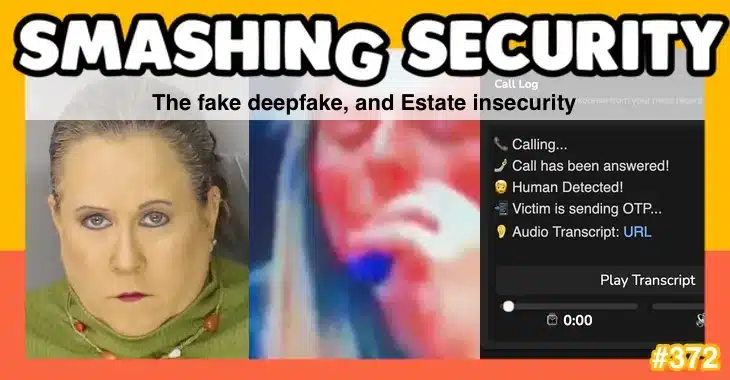
Read MoreRemember when a US mother was accused of distributing explicit deepfake photos and videos to try to get her teenage daughter’s cheerleading rivals kicked off the team? Well, there has been a surprising development. And learn how cybercriminals have been stealing boomers’ one-time-passcodes via a secretive online service. All this and more is discussed in…
Read MoreHow you may be affected by the new proposed Critical Infrastructure Cyber Incident Reporting Rule
by nlqip
Creating a world that is safer and more secure is core to our vision at Palo Alto Networks, but this only can be achieved if we’re collectively making the internet, as a whole, safer. To do this requires more widespread awareness of cyber threats and information sharing, and a newly proposed cyber incident reporting rule…
Read MoreMay 15, 2024NewsroomAndroid Security / Malware Google is unveiling a set of new features in Android 15 to prevent malicious apps installed on the device from capturing sensitive data. This constitutes an update to the Play Integrity API that third-party app developers can take advantage of to secure their applications against malware. “Developers can check…
Read MoreOn December 18, 2023, SRHS confirmed the breach compromised data of 252890 patients, all of whom were notified through mails on January 12, 2023. Similar notifications were sent on May 13, 2024, this time to the 25 Maine patients, confirming the new estimate. “Through the investigation, Singing River identified unauthorized access within its environment between August 16 and August 18,…
Read MoreA threat actor claimed that they have data from Philippines National Police, and advertised the data in breachforums.vc. It is claimed that the data is belonging to Philippines National Police Logistics Data Information and Management System. Some sample data also shared by the threat actor. Breachforums.vc is an English-language forum that has been active since…
Read MoreHPE Aims To ‘Leapfrog’ Competitors With Hybrid Cloud AI Ops Based HPE GreenLake For Block Storage: HPE VP Sanjay Jagad.
by nlqip
The new offerings include HPE GreenLake Block Storage For AWS, which allows HPE partners to “seamlessly manage” block storage across on premise GreenLake and AWS public cloud environments, according to HPE. Hewlett Packard Enterprise Wednesday unleashed a new version of HPE GreenLake for Block Storage designed to “leapfrog” competitors and establish HPE as a leader…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher