Category: AI in news
An unnamed European Ministry of Foreign Affairs (MFA) and its three diplomatic missions in the Middle East were targeted by two previously undocumented backdoors tracked as LunarWeb and LunarMail. ESET, which identified the activity, attributed it with medium confidence to the Russia-aligned cyberespionage group Turla (aka Iron Hunter, Pensive Ursa, Secret Blizzard, Snake, Uroburos, and…
Read MoreHere’s How to Enhance Your Cyber Resilience with CVSS In late 2023, the Common Vulnerability Scoring System (CVSS) v4.0 was unveiled, succeeding the eight-year-old CVSS v3.0, with the aim to enhance vulnerability assessment for both industry and the public. This latest version introduces additional metrics like safety and automation to address criticism of lacking granularity…
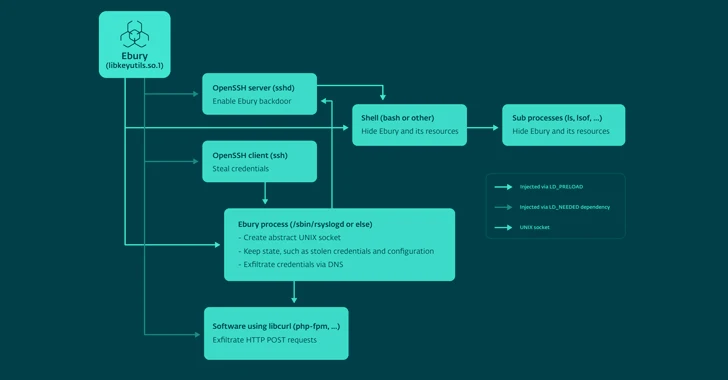
Read MoreA malware botnet called Ebury is estimated to have compromised 400,000 Linux servers since 2009, out of which more than 100,000 were still compromised as of late 2023. The findings come from Slovak cybersecurity firm ESET, which characterized it as one of the most advanced server-side malware campaigns for financial gain. “Ebury actors have been…
Read Moreffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreMay 15, 2024NewsroomCryptocurrency / Anonymity A Dutch court on Tuesday sentenced one of the co-founders of the now-sanctioned Tornado Cash cryptocurrency mixer service to 5 years and 4 months in prison. While the name of the defendant was redacted in the verdict, it’s known that Alexey Pertsev, a 31-year-old Russian national, has been awaiting trial…
Read MoreTime is running out for businesses to prepare for looming new EU cyber security legislation and risk severe penalties for noncompliance. The Network and Information Systems Directive 2022/0383 – shortened to NIS2 – has been introduced by the EU to strengthen the bloc’s existing cybersecurity policies. It sets a minimum level of requirement for certain…
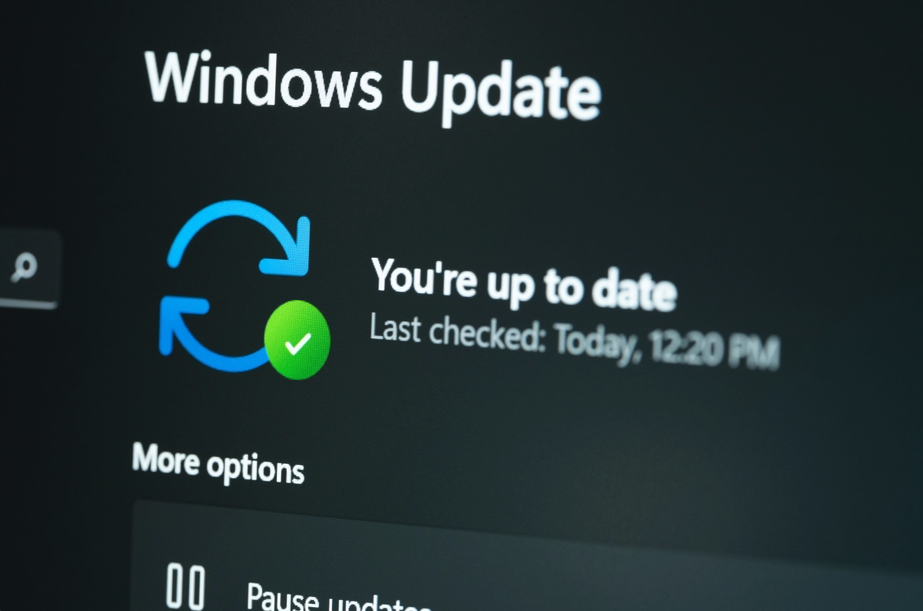
Read MoreMay 15, 2024NewsroomPatch Tuesday / Vulnerability Microsoft has addressed a total of 61 new security flaws in its software as part of its Patch Tuesday updates for May 2024, including two zero-days which have been actively exploited in the wild. Of the 61 flaws, one is rated Critical, 59 are rated Important, and one is…
Read More“This is something our team at Chainguard tracks quite closely, as we patch CVEs daily in open-source security projects. We are now relying on industry alternatives and social media to ensure we are triaging CVEs as quickly as we can versus waiting for NVD to triage and publish.” The NVD situation became so desperate that…
Read MoreIn the beginning, Black Basta affiliates used to break into organizations by using email spear phishing techniques to deploy some sort of trojan or backdoor via malicious attachments or links. Spear phishing remains one of the most common techniques to deploy malware and is used by nearly all cybercriminal gangs. Another method is to buy…
Read MoreMicrosoft today released updates to fix more than 60 security holes in Windows computers and supported software, including two “zero-day” vulnerabilities in Windows that are already being exploited in active attacks. There are also important security patches available for macOS and Adobe users, and for the Chrome Web browser, which just patched its own zero-day…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher