Category: AI in news
May 14, 2024The Hacker NewsCyber Threat / Machine Learning Deploying advanced authentication measures is key to helping organizations address their weakest cybersecurity link: their human users. Having some form of 2-factor authentication in place is a great start, but many organizations may not yet be in that spot or have the needed level of authentication…
Read MoreAnother Chrome Vulnerability Google has patched another Chrome zero-day: On Thursday, Google said an anonymous source notified it of the vulnerability. The vulnerability carries a severity rating of 8.8 out of 10. In response, Google said, it would be releasing versions 124.0.6367.201/.202 for macOS and Windows and 124.0.6367.201 for Linux in subsequent days. “Google is…
Read MoreBlack Basta ransomware group's techniques evolve, as FBI issues new warning in wake of hospital attack
by nlqip
Security agencies in the United States have issued a new warning about the Black Basta ransomware group, in the wake of a high-profile attack against the healthcare giant Ascension. The cyber attack last week forced the Ascension computer systems offline, and caused some hospital emergency departments to turn away ambulances “in order to ensure emergency…
Read MoreMicrosoft’s cloud licensing practices are under fire once again, with critics alleging anti-competitive behavior and concerns about vendor lock-in. The controversy centers around the complexity and lack of transparency in Microsoft’s licensing terms, which are accused of favoring its own Azure cloud platform over competitors like Amazon Web Services (AWS) and Google Cloud Platform (GCP).…
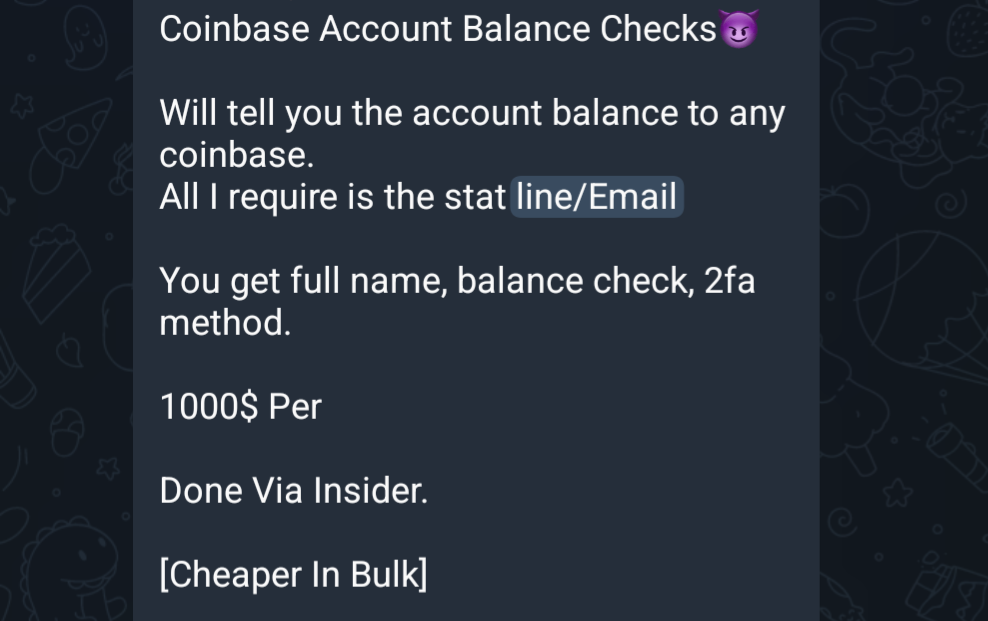
Read MoreA threat actor claimed that they have an access to Coinbase with ability to check the balance of any account. The advertisement shared in Telegram group. Coinbase is a leading cryptocurrency exchange platform founded in 2012, headquartered in the United States. It allows users to buy, sell, and store various cryptocurrencies like Bitcoin, Ethereum, and…
Read MoreHyatt’s team recently identified a rogue USB drive used to install the Raspberry Robin malware, which acts as a launchpad for subsequent attacks and gives bad actors the ability to fulfil the three key elements of a successful attack — establish a presence, maintain access and enable lateral movement. “Because it has a loader capability,…
Read MoreApple and Google Launch Cross-Platform Feature to Detect Unwanted Bluetooth Tracking Devices
by nlqip
May 14, 2024NewsroomLocation Tracking / Privacy Apple and Google on Monday officially announced the rollout of a new feature that notifies users across both iOS and Android if a Bluetooth tracking device is being used to stealthily keep tabs on them without their knowledge or consent. “This will help mitigate the misuse of devices designed…
Read MoreShifting the Paradigm: Why the Cyber Insurance Industry Should Focus on Preventive Security
by nlqip
Does your organization currently have a cyber insurance policy? Without it, you are missing a critical piece of a holistic security strategy. With increased cyberattacks and expansion in cloud and digital operational technology (OT) assets, organizations face significant costs during and after breaches. This has led to expensive claim payouts by cyber insurance providers, and,…
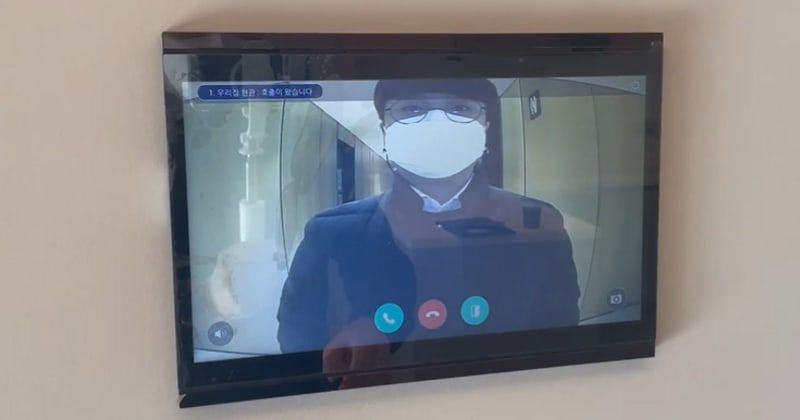
Read MoreA Korean cybersecurity expert has been sentenced to prison for illegally accessing and distributing private videos from vulnerable “wallpad” cameras in 400,000 private households. The 41-year-old man, who has not been officially named, succeeded in remotely accessing 638 apartment complexes in South Korea. He exploited over 400,000 smart home devices used by residents to operate…
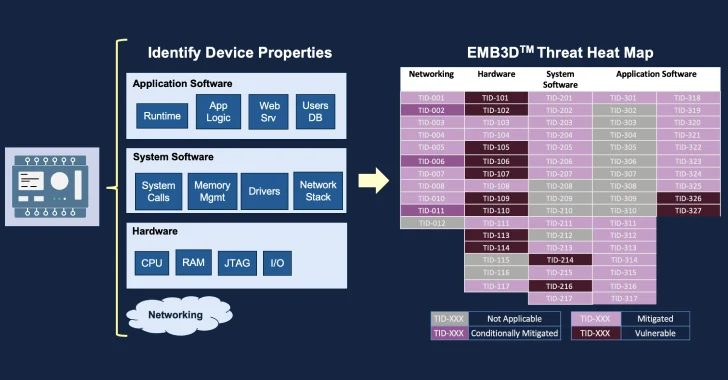
Read MoreMay 13, 2024Newsroom The MITRE Corporation has officially made available a new threat-modeling framework called EMB3D for makers of embedded devices used in critical infrastructure environments. “The model provides a cultivated knowledge base of cyber threats to embedded devices, providing a common understanding of these threats with the security mechanisms required to mitigate them,” the…
Read MoreRecent Posts
- Everything That You Need to Know About the Dark Web and Cybercrime | BlackFog
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches