Category: AI in news
Capgemini, Miracle Software Systems and Presidio were among the standout solution providers at Red Hat Summit 2024. One of the central messages throughout Red Hat’s Summit 2024 event was that the open source enterprise tools vendor sees solution providers as integral in meeting customer demand in multiple technology opportunities, including artificial intelligence and virtualization. During…
Read MoreThe type of information stolen is believed to include name, physical address, and purchase order details. No sensitive information breached On April 28, Menelik listed stolen data from Dell on BreachForum that included customer information with non-financial fields such as City, Full Name, Address, Province, Postal Code, Warranty plan, Company name, Dell Order Number, Dell…
Read MoreMay 10, 2024NewsroomBrowser Security / Vulnerability Google on Thursday released security updates to address a zero-day flaw in Chrome that it said has been actively exploited in the wild. Tracked as CVE-2024-4671, the high-severity vulnerability has been described as a case of use-after-free in the Visuals component. It was reported by an anonymous researcher on…
Read MoreEven if you’ve got all the bells and whistles when it comes to securing your data center, your cloud deployments, your building’s physical security, and you’ve invested in defensive technologies, have the right security policies and processes in place and measure their effectiveness and continuously improve, still a crafty social engineer can weasel his way…
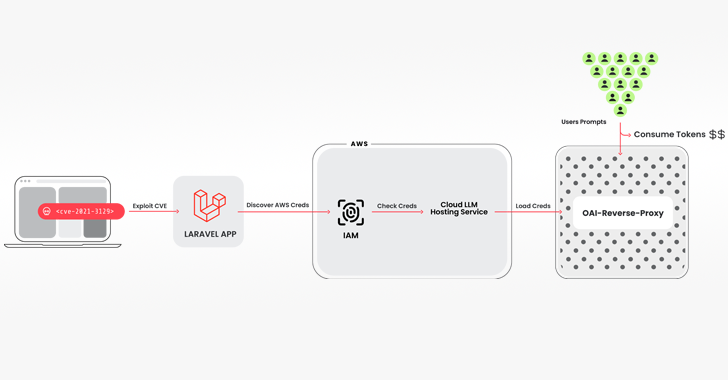
Read MoreMay 10, 2024NewsroomVulnerability / Cloud Security Cybersecurity researchers have discovered a novel attack that employs stolen cloud credentials to target cloud-hosted large language model (LLM) services with the goal of selling access to other threat actors. The attack technique has been codenamed LLMjacking by the Sysdig Threat Research Team. “Once initial access was obtained, they…
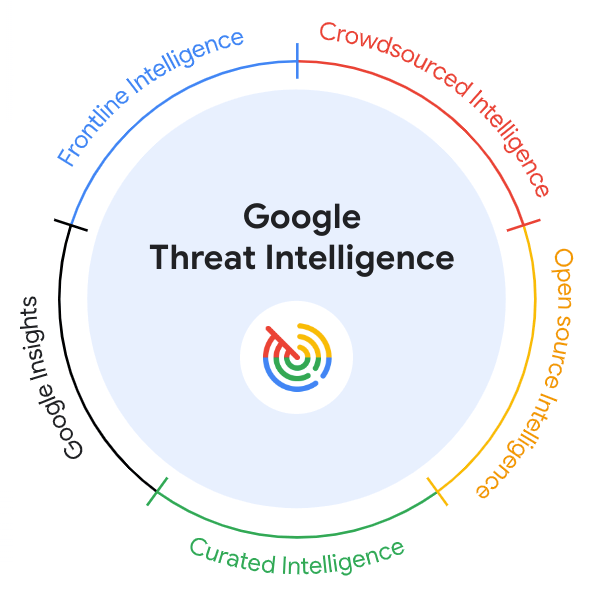
Read MoreAt the RSA Conference in San Francisco, Google announced the launch of Google Threat Intelligence, a groundbreaking new offering that leverages the company’s vast resources and expertise in cybersecurity to provide actionable threat intelligence at an unprecedented scale. Unparalleled Depth and Breadth of Intelligence This new platform combines the front-line expertise of Mandiant, the global…
Read MoreCISOs can protect themselves by making responsibilities clear With cyber incidents becoming more frequent and prominent, the role of CISOs has become a lightning rod. “Historically, the risk calculus was bad stuff happens, I’m going to get fired, I’ll go on to my next job,” said Charles Blauner, partner and CISO in residence at Team8…
Read MoreDo you know Dmitry Yuryevich Khoroshev? If you do, there’s a chance that you might well on the way to receiving a reward of up to $10 million. Read more in my article on the Exponential-e blog. Source link lol
Read MoreSnowflake Is Building World’s ‘No. 1 AI, Apps And Expertise’ Ecosystem, Says Global Partner Leader
by nlqip
Tyler Prince, Snowflake’s worldwide leader of Alliances and Channel, explains to CRN Snowflake’s mission to create the best AI, app and expertise partner ecosystem in the world as the AI era heats up. Snowflake is assembling the world’s best partner ecosystem for AI and applications with a unique approach that only Snowflake can provide, according…
Read MoreMay 09, 2024NewsroomEncryption / Data Privacy Researchers have detailed a Virtual Private Network (VPN) bypass technique dubbed TunnelVision that allows threat actors to snoop on victim’s network traffic by just being on the same local network. The “decloaking” method has been assigned the CVE identifier CVE-2024-3661 (CVSS score: 7.6). It impacts all operating systems that…
Read MoreRecent Posts
- Everything That You Need to Know About the Dark Web and Cybercrime | BlackFog
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches