Category: AI in news
Customers express concerns Dropbox said it swung into action as soon as it discovered the breach and “launched an investigation with industry-leading forensic investigators to understand what happened and mitigate risks to our users.” Its investigation revealed that “a third party gained access to a Dropbox Sign automated system configuration tool.” “The actor compromised a…
Read MoreThe committee emphasized that MFA should be a fundamental expectation for an entity like Change Healthcare, given the vast amount of sensitive data it handles. Witty explained that Change Healthcare, which merged into UnitedHealth towards the end of 2022, utilized older technologies that the company had been updating since its acquisition. However, the timing proved…
Read MoreLegit Security software compliance attestation trust center Legit Security introduced a software compliance attestation trust center, which by using frameworks such as SLSA, PCI DSS, SOC2, and ISO 27001, helps teams quickly assess the state of a software security program to identify gaps that create risk. The trust center also supports new CISA requirements. It…
Read MoreMay 02, 2024NewsroomVulnerability / Data Breach The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting GitLab to its Known Exploited Vulnerabilities (KEV) catalog, owing to active exploitation in the wild. Tracked as CVE-2023-7028 (CVSS score: 10.0), the maximum severity vulnerability could facilitate account takeover by sending password reset emails to…
Read MorePrinciples and objectives driving the NSM The NSM cites eight core principles that drive the NSM. First among these is a sense of shared responsibility by government entities and the owners of critical to come together in a “national unity of effort.” Related to this united effort is the principle that government regulatory and oversight…
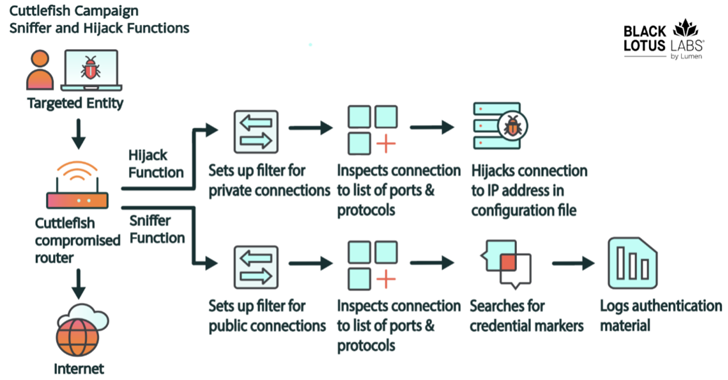
Read MoreMay 02, 2024NewsroomCyber Espionage / Network Security A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from HTTP GET and POST requests. “This malware is modular, designed primarily to steal authentication material found in web…
Read MoreSmashing Security podcast #370: The closed loop conundrum, default passwords, and Baby Reindeer
by nlqip
The UK Government takes aim at IoT devices shipping with weak or default passwords, an identity thief spends two years in jail after being mistaken for the person who stole his name, and are you au fait with the latest scams? All this and much more is discussed in the latest edition of the “Smashing…
Read MoreGoogle’s new round of layoffs hit developers and engineers working inside Google’s Core business unit. Here’s what you need to know. Just one week after reporting $80.5 billion in sales and $23.7 billion in net income during its first quarter 2024, Google is laying off hundreds of employees—including many in its ‘Core’ team roles—while moving…
Read MoreSynthetic Content Risks Today’s first-generation AI systems are capable of maliciously synthesizing images, sound, and video well enough for it to be indistinguishable from genuine content. The guide “Reducing Risks Posed by Synthetic Content” (NIST AI 100-4) examines how developers can authenticate, label, and track the provenance of content using technologies such as watermarking. A…
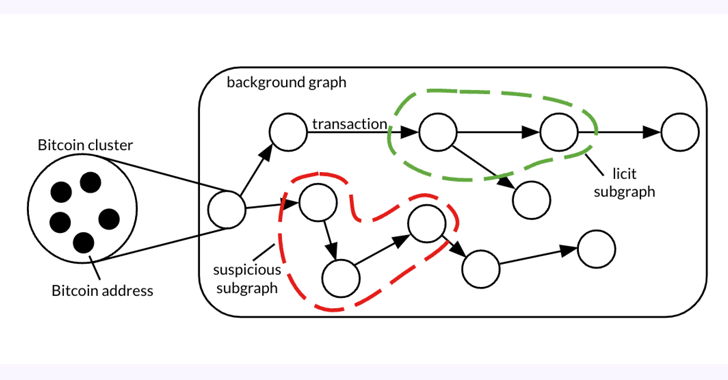
Read MoreMay 01, 2024NewsroomFinancial Crime / Forensic Analysis A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with illicit activity and money laundering, including detecting criminal proceeds sent to a crypto exchange and previously unknown wallets belonging to a Russian darknet market. The findings come from Elliptic in…
Read MoreRecent Posts
- US charges Phobos ransomware admin after South Korea extradition
- CVE-2024-0012, CVE-2024-9474: Zero-Day Vulnerabilities in Palo Alto PAN-OS Exploited In The Wild
- Critical RCE bug in VMware vCenter Server now exploited in attacks
- Nvidia Reveals 4-GPU GB200 NVL4 Superchip, Releases H200 NVL Module
- New AWS Control Policy on the Block