Category: AI in news
Longtime co-CEO Yoav Toussia-Cohen has left cloud channel superstar DoiT International who is a top global Google Cloud and AWS partner. One of the world’s top cloud channel partners DoiT International has lost its longtime co-CEO, who played a critical role in making DoiT a leading global Google Cloud and Amazon Web Services partner. Yoav…
Read MorePrompt injections, the most common form of LLM attacks, involve bypassing filters or manipulating the LLM to make it ignore previous instructions and to perform unintended actions, while training data poisoning involves manipulation of LLM training data to introduce vulnerabilities, backdoors and biases. “The firewall monitors user prompts to pre-emptively identify and mitigate potential malicious…
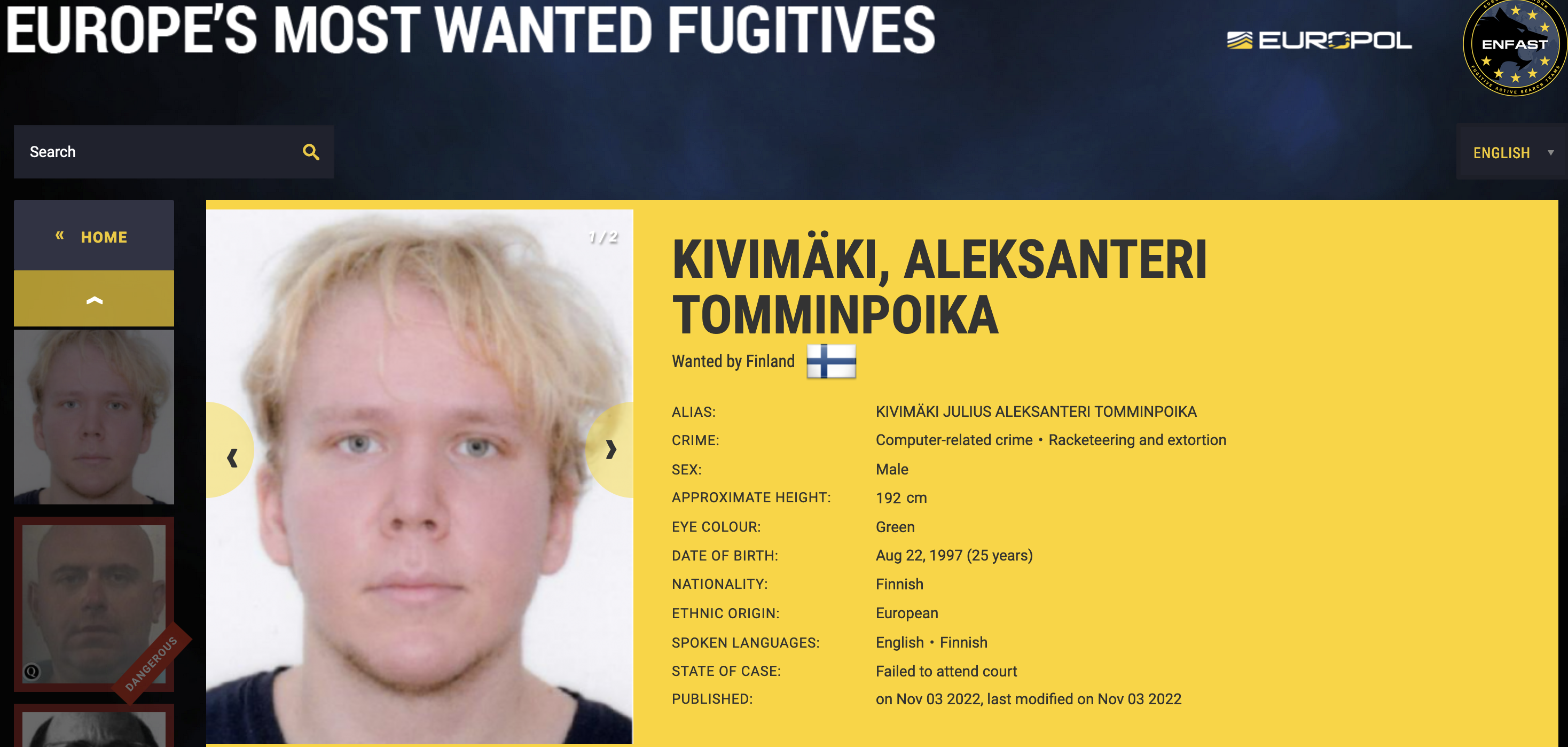
Read MoreA 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an online psychotherapy clinic, leaking tens of thousands of patient therapy records, and attempting to extort the clinic and patients. On October 21, 2020, the Vastaamo Psychotherapy Center in Finland became the target of blackmail…
Read MoreAWS’ global partner leader, Ruba Borno, talks with CRN about the general availability of Amazon Q Tuesday and why the AI-powered assistant is better than rivals Google and Microsoft’s generative AI technology. AWS’ Ruba Borno is bullish that Amazon Q is now the world’s best generative AI-powered assistant as the new AI chatbot becomes generally…
Read MoreAbout Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998. I’m a fellow and lecturer at Harvard’s Kennedy School, a board member of EFF, and the Chief of Security Architecture…
Read MoreApr 30, 2024NewsroomMachine Learning / National Security The U.S. government has unveiled new security guidelines aimed at bolstering critical infrastructure against artificial intelligence (AI)-related threats. “These guidelines are informed by the whole-of-government effort to assess AI risks across all sixteen critical infrastructure sectors, and address threats both to and from, and involving AI systems,” the…
Read MoreCalls for better response amid consolidation Meanwhile, the ransomware attack on Change Healthcare has triggered demands for mandatory baseline security standards for healthcare providers. Earlier this month, UnitedHealth faced criticism for its handling of the attack during a three-hour session before the House Energy and Commerce Committee. Significantly, the incident has brought concerns about healthcare…
Read MoreClose the barn door now! Avoid the risk of not monitoring retained access before it’s a problem
by nlqip
It would be far better if those doing the contracting, hiring, or engagement management had it in their built-in process that when a contract concludes or an employee moves or departs, IT is informed, accounting is informed, and human resources is informed. It’s absurd to allow an employee to simply walk away and wait for…
Read MoreIn early April, a threat actor called DoD offered on BreachForums three gigabytes of data allegedly stolen from the US Environmental Protection Agency’s (EPA) systems, claiming it was a contact list of critical infrastructure organizations worldwide. The EPA said that DoD had confirmed it had never breached the agency and that the data posted was…
Read More“Vulnerabilities that are known to work are a good first bet for a threat actor to try. Attackers are using them because they’re still working.” Bombarding SMBs with exploits for possibly unpatched flaws was simply the easiest way to find the laggards among organizations whose patching routines are not always rigorous. The bigger question, then,…
Read MoreRecent Posts
- Palo Alto Networks patches two firewall zero-days used in attacks
- Vulnerability Summary for the Week of November 11, 2024 | CISA
- US space tech giant Maxar discloses employee data breach
- CISA Adds Two Known Exploited Vulnerabilities to Catalog | CISA
- CISA Adds Three Known Exploited Vulnerabilities to Catalog | CISA