Category: AI in news
The concept of living inside a computer-generated world, much like Neo in The Matrix, has long intrigued minds across science and philosophy. Now, a controversial concept called the Second Law of Infodynamics proposes evidence that the very fabric of our reality might be digital. Dr. Melvin Vopson of the University of Portsmouth believes the universe…
Read MoreThe key to minimize personal liability for CSOs and CISOs after a data breach is to act responsibly and reasonably. The current state of the law is that those involved in an organization that is threatened or affected by a data breach are expected to react reasonably under the circumstances. To meet this standard, one…
Read MoreIt’s a similar story in Australia where the chairman of the country’s corporate regulator, Australian Securities and Investments Commission, Joe Longo, previously stated he wants to hold cyber executives and boards accountable for not taking sufficient steps to protect customers and infrastructure from hackers if a company is compromised. Bob Zukis, CEO and founder of Digital Directors…
Read MoreCSO ASEAN is proud to launch the fourth edition of the CSO30 ASEAN Awards in 2024 – recognising the top 30 cybersecurity executives driving innovation, strengthening resilience, and influencing industry change. In 2024, CSO30 ASEAN nominees will be judged based on the core pillars of business value and leadership. Judges will assess cybersecurity initiatives introduced…
Read MoreApr 28, 2024NewsroomCredential Stuffing / Data Breach Identity and access management (IAM) services provider Okta has warned of a spike in the “frequency and scale” of credential stuffing attacks aimed at online services. These unprecedented attacks, observed over the last month, are said to be facilitated by “the broad availability of residential proxy services, lists…
Read MoreInternational Business Machines (IBM) has announced its intention to acquire HashiCorp, a cloud infrastructure automation company, in a deal valued at $6.4 billion. This strategic move aims to expand IBM’s cloud-based software offerings and capitalize on the surging demand driven by artificial intelligence (AI). The deal comes as IBM experiences mixed results, with its software…
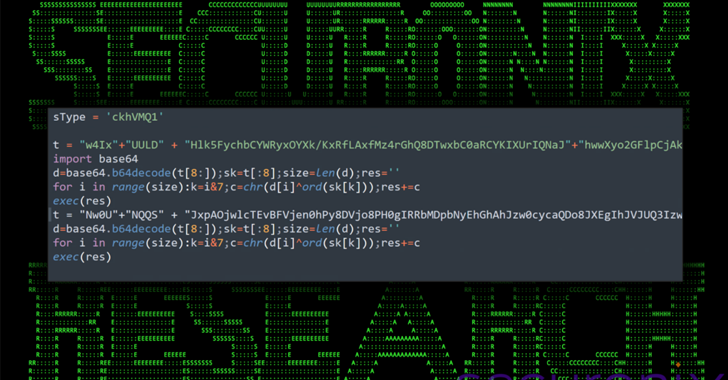
Read MoreApr 27, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging a nearly seven-year-old flaw in Microsoft Office to deliver Cobalt Strike on compromised systems. The attack chain, which took place at the end of 2023 according to Deep Instinct, employs a PowerPoint slideshow file (“signal-2023-12-20-160512.ppsx”)…
Read MoreIn a major move within the cybersecurity sector, KnowBe4, a leading security awareness training platform, has announced the acquisition of Egress, a prominent cloud email security provider. This strategic partnership blends two powerful forces in the battle against cyber threats. Who are KnowBe4 and Egress? KnowBe4: A pioneer in security awareness training, KnowBe4 empowers organizations…
Read MoreApr 27, 2024NewsroomMalware / Software Security An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity firm Securonix is tracking the activity under the name DEV#POPPER, linking it to North Korean threat actors. “During these fraudulent…
Read MoreFriday Squid Blogging: Searching for the Colossal Squid A cruise ship is searching for the colossal squid. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: squid Posted on April 26, 2024 at 5:07 PM…
Read MoreRecent Posts
- Chinese hackers exploit Fortinet VPN zero-day to steal credentials
- Multiple Vulnerabilities in Palo Alto PAN-OS Could Allow for Authentication Bypass
- Brave on iOS adds new “Shred” button to wipe site-specific data
- Palo Alto Networks patches two firewall zero-days used in attacks
- Vulnerability Summary for the Week of November 11, 2024 | CISA