Category: AI in news
Because of its ubiquity as a network platform, Windows all too often gets blamed as the source of a host of network security vulnerabilities. But recent events have shown the truth — that all sorts of network components have flaws and that there are many nefarious means attackers can use to enter and take control.…
Read MoreAs we near the halfway point of the year, organizations are under tremendous pressure to grow businesses across all industries. It’s no secret: bottom lines must rise and 2024 has been earmarked as a pivotal year to revert to growth mode. Many organizations will find an uphill battle here; the previous few years have taken…
Read MoreJust one month after purchasing a data center campus in Pennsylvania for $650 million, AWS CEO Adam Selipsky says the cloud company will invest $11 billion to build a new data center campus in Indiana. Amazon Web Services CEO Adam Selipsky said the cloud company’s plan to invest $11 billion in building a new cloud…
Read MoreApr 25, 2024NewsroomMalware / Cyber Threat The North Korea-linked threat actor known as Lazarus Group employed its time-tested fabricated job lures to deliver a new remote access trojan called Kaolin RAT. The malware could, “aside from standard RAT functionality, change the last write timestamp of a selected file and load any received DLL binary from…
Read MoreWhat’s going on? A wave of cheap, crude, amateurish ransomware has been spotted on the dark web – and although it may not make as many headlines as LockBit, Rhysida, and BlackSuit, it still presents a serious threat to organizations. What’s “junk gun” ransomware? It’s a name coined by Sophos researchers for unsophisticated ransomware that…
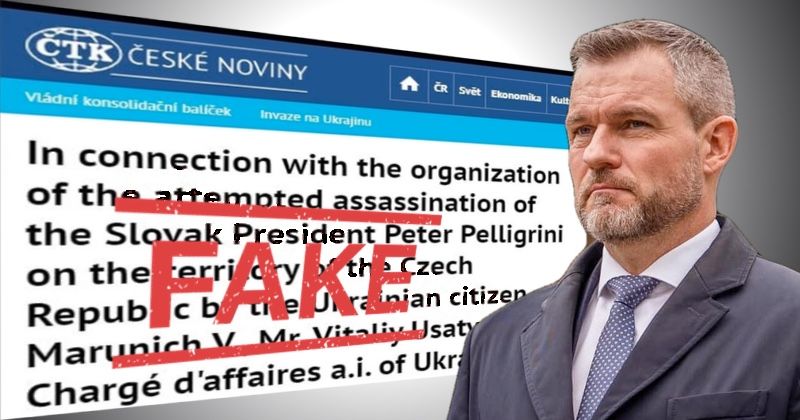
Read MoreCzech news agency ČTK announced on Tuesday that a hacker had managed to break into its systems and published fake news reports of a plot to murder the president of a neighbouring country. One of the false stories published by the hacker in Czech and English claimed that Czechia’s security information service (known as BIS)…
Read More“We believe there will be added demand because a combined portfolio is more interesting,” IBM CEO Arvind Krishna said on an earnings call. IBM executives painted the planned $6.4 billion purchase of cloud infrastructure tools vendor HashiCorp as complementary to multiple business segments – including fellow open-source tools provider Red Hat – even as IBM…
Read MoreSalt is the first and the only vendor in the market to provide this functionality to help mitigate risk associated with a new class of OAuth threats, Schwake claimed. In-house AI for mitigation Vulnerabilities in OAuth systems can leave access tokens or authorization codes susceptible to theft. Attackers can leverage those stolen elements to impersonate…
Read MoreThe Rise of Large-Language-Model Optimization The web has become so interwoven with everyday life that it is easy to forget what an extraordinary accomplishment and treasure it is. In just a few decades, much of human knowledge has been collectively written up and made available to anyone with an internet connection. But all of this…
Read MoreApr 25, 2024NewsroomCryptocurrency / Cybercrime The U.S. Department of Justice (DoJ) on Wednesday announced the arrest of two co-founders of a cryptocurrency mixer called Samourai and seized the service for allegedly facilitating over $2 billion in illegal transactions and for laundering more than $100 million in criminal proceeds. To that end, Keonne Rodriguez, 35, and…
Read MoreRecent Posts
- Chinese hackers exploit Fortinet VPN zero-day to steal credentials
- Multiple Vulnerabilities in Palo Alto PAN-OS Could Allow for Authentication Bypass
- Brave on iOS adds new “Shred” button to wipe site-specific data
- Palo Alto Networks patches two firewall zero-days used in attacks
- Vulnerability Summary for the Week of November 11, 2024 | CISA