Category: AI in news
Last Update: December 28, 2021 If you are reading this, you likely have heard about Log4Shell, the December, 2021 critical zero-day remote-code execution vulnerability, and subsequent vulnerabilities in the popular Log4j software library that is developed and maintained by the Apache Software Foundation. Apache has patched these vulnerabilities in version 2.17.1, however vendors who use…
Read More[Links and resources updated on October 4, 2022] If you told me a year ago that I would meet a cold war hero at a birthday party, I wouldn’t have believed you. And I would be even more skeptical if you told me she would be an unintimidating, approachable music professor with an infectious smile.…
Read MoreSo, here’s something that blew my mind: I decided to test Google’s NotebookLM AI tool. I casually uploaded the URLs for my LinkedIn page and my blog, not expecting much more than a basic summary. After about 3–4 minutes of AI whirring away, I had…a podcast in the form of a WAV file. Curious, I clicked…
Read MoreCybersecurity Snapshot: Many Employees Overshare Work Info with AI Tools, Report Finds, as ‘Cybersecurity Awareness Month’ Kicks Off
by nlqip
Check out the best practices cyber agencies are promoting during Cybersecurity Awareness Month, as a report warns that staffers are feeding confidential info to AI tools. Meanwhile, a study highlights how business decisions can derail OT security. Plus, get the latest on Active Directory security, CISO salary trends and ransomware attacks! Dive into six things…
Read More‘So much of Tableau’s success is thanks to our partners’ investment in our customers,’ says Tableau CEO Ryan Aytay. Salesforce plans to roll out a Tableau Einstein Alliance partner community in February with the goal of furthering artificial intelligence and AI agent creation and delivery through access to experts, marketing materials and product road map…
Read More“The cultural fit of our two companies will enable our mutual success going forward,” CACI CEO John Mengucci said. CACI International has bought fellow solution provider Applied Insight in an all-cash deal that should boost its capabilities in Amazon Web Services, cloud migration, cybersecurity and productivity for government agency customers. CACI, No. 19 on CRN’s…
Read More‘I will continue to cheer you on and be here for you always!’ Tony Safoian wrote on LinkedIn. SADA CEO Tony Safoian–whose family founded the solution provider in 2000–announced his upcoming retirement from the company Tuesday, with Chief Operating Officer Dana Berg set to take the top spot. Safoian’s last day with Los Angeles-based SADA–No.…
Read MoreAs the number of IoT devices deployed globally continues to rise, cyber-physical systems and business operations are exposed to greater risk. Improving asset visibility, monitoring and risk management are critical steps to preventing breaches. As businesses continue to embrace digital transformation, the proliferation of internet of things (IoT) devices across industries has resulted in unprecedented…
Read MoreThe Irvine, Calif.-based IT distribution giant said it would use the net proceeds of an IPO to pay down a portion of the firm’s $1.16 billion in debt. Ingram Micro’s plans for an initial public offering (IPO) became clearer Monday with a new U.S. Securities and Exchange Commission filing by its holding company outlining the…
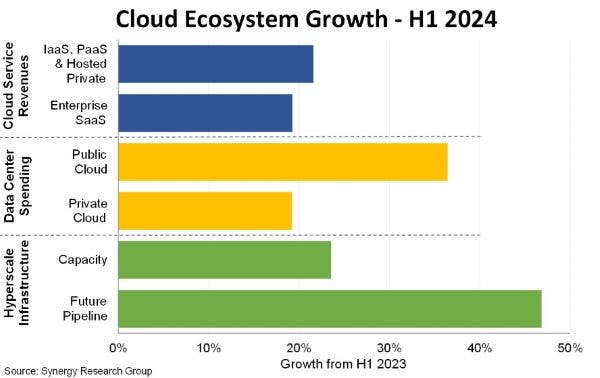
Read More‘Over the last 10 years ODMs have continued to eat up server market share, and now we see Nvidia’s explosive growth, which is largely fueled by sales to hyperscalers—either directly or indirectly,’ said John Dinsdale, Synergy Research Group’s chief analyst. Cloud revenues reached $427 billion in the first half of 2024, up 23 percent year…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA