Category: AI in news
Once upon a time I was a security consultant. I was assigned to review the firewall configuration for a sizeable Seattle startup of about 800 employees. They were in the business of hosting websites for thousands of small businesses across the world and therefore had a somewhat complex Internet connectivity setup. I sat down and…
Read MoreThe role of deception technology in modern cybersecurity is to turn the tables on cybercriminals, transforming networks from passive targets into active traps. Deception gives security teams the chance to use hackers’ own methods against them, as well as gather intelligence on their tactics. But deception’s role is evolving. Read on to learn how deception…
Read MoreBecause of an international criminal act, you can get a cheap morning latte. Historically, the country of Yemen had a monopoly on coffee, forbidding the export of the plants and seeds—their intellectual property. However, in 1616, a Dutch merchant managed to smuggle out a few coffee plants from the city of Mocha in Yemen. Holland…
Read MoreCommunication is Key – Leveraging Business Frameworks to Develop a Detection and Response Strategy | Binary Defense
by nlqip
Operating a business within the modern threat landscape can often appear like an impossible task. With a constant stream of new vulnerabilities, malware, and adversaries flowing, security leadership can often become overwhelmed and stuck in “analysis paralysis” struggling to identify what threats to invest resources towards. It’s no secret that cybercrime has become big business…
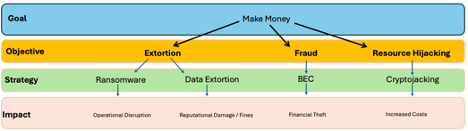
Read MoreAllow me to nitpick for a moment: There’s a difference between data and information. Data are the facts or details from which information is derived. As such, standalone pieces of data are rarely useful. It’s not really information until data points are connected with context to tell a story. This nuance is more relevant than…
Read MoreThreat intelligence is mainstreaming into a de-facto everyday tool of cyber-defense. But all that intelligence must be collected, analyzed, and prepared by someone. Enter threat researchers, the advanced scouts of cybersecurity. They are becoming more numerous and conspicuous as more intelligence on illicit hacker activity is demanded. Threat researchers trawl through the dark web, pick…
Read MoreEver wonder what security professionals see as their main barrier to achieving a strong application security posture? We wondered that, too, so we asked them. As part of F5 Labs’ first annual Application Protection Report, F5, in conjunction with Ponemon Institute, surveyed security professionals on a slew of security-related topics. In answer to this particular…
Read More“It’s highly likely that the absence of multi-factor authentication allowed attackers to circumvent the security measures of UnitedHealth Group’s [Change] Healthcare unit,” Aleem said. “Initial reports suggest that the attackers remained undetected in the environment for over a week and conducted lateral movement.” Aleem added: “It’s probable that the attackers left some traces, or ‘breadcrumbs’,…
Read MoreBetteridge’s law of headlines is an adage that explains that “Any headline that ends in a question mark can be answered by the word no.”1 Back in March 2017, I asked “Will Deception as a Defense Become Mainstream?” No, deception hasn’t become mainstream yet. But, here and there, deception does poke its fingers into the…
Read MoreWith each entity, process or service that moves from the physical world into cyberspace, there is a corresponding transformation to the threat landscape. Digital transformation doesn’t just change the business model or the supply chain dynamic. It also introduces significant new threats that go beyond monitoring web traffic and securing networks. Those threats take a variety…
Read MoreRecent Posts
- Spotify abused to promote pirated software and game cheats
- Chinese hackers exploit Fortinet VPN zero-day to steal credentials
- Multiple Vulnerabilities in Palo Alto PAN-OS Could Allow for Authentication Bypass
- Brave on iOS adds new “Shred” button to wipe site-specific data
- Palo Alto Networks patches two firewall zero-days used in attacks