Category: AI in news
Can’t We Just Get Rid of Passwords Now? Shape Security and F5 Labs recently published the 2021 Credential Stuffing Report, which is the product of a multi-year collaborative research project that evolved from Shape’s original Credential Spill Report. This year’s report covers the lifecycle of credential theft in detail, from the original theft of usernames…
Read MoreEven Strong Defenses May Contain Weaknesses One could argue that fraudsters’ tactics are not novel and that investing in specialized products with machine learning and artificial intelligence should solve the issue of fraud. But somehow fraudsters still manage to outsmart security defenses. In a recent discussion that F5 Labs had with the head of the…
Read MoreAs Figures 5 and 6 illustrate, CAPTCHA solver services have made it possible for attackers to completely circumvent CAPTCHAs, including Google’s latest version called CAPTCHA Enterprise (not shown here). The Business of Human CAPTCHA Solvers In many respects, CAPTCHA solver services operate like any legitimate enterprise, and they are clearly in business to make a…
Read MoreHeadlines about breaches and compliance penalties give us a strong idea of what we do not want for our security programs. Of the breaches in 2020, the financial sector had the highest percentage at 17 percent, as noted in the 2021 Application Protection Report. With breaches, come regulator attention. In 2017, New York’s Department of…
Read MoreUpdate, June 22, 2022: In light of the root cause analysis published by Cloudflare for their recent outage, we thought we’d refresh this article since it remains relevant. Much as was the case with Facebook back in October 2021, the downtime was the result of a misconfiguration of BGP – in the case of Cloudflare,…
Read MoreSingle points of failure are the bane of engineering, and engineers put great effort into eliminating them from the systems they design. Increasingly, however, companies are handing over large amounts of their IT infrastructure and application portfolios to third-party providers. This reveals an interesting form of the single point of failure. If an organization uses…
Read MoreUsing Legitimate GitHub URLs for Malware Interesting social-engineering attack vector: McAfee released a report on a new LUA malware loader distributed through what appeared to be a legitimate Microsoft GitHub repository for the “C++ Library Manager for Windows, Linux, and MacOS,” known as vcpkg. The attacker is exploiting a property of GitHub: comments to a…
Read MoreTo find the correct password, attackers must check word after word until they find one which outputs the same hash value as the one they have stolen. While this sounds tedious, password cracking tool, such as Hashcat, are capable of calculating billions of hashes per second on a single computer. Renting cloud computing services allows…
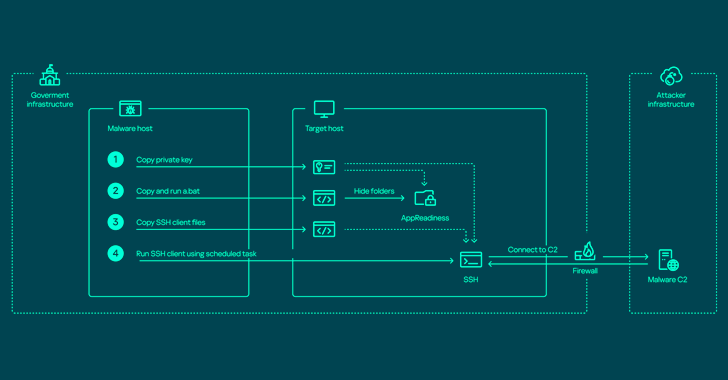
Read MoreApr 22, 2024NewsroomNetwork Security / Endpoint Security The threat actor known as ToddyCat has been observed using a wide range of tools to retain access to compromised environments and steal valuable data. Russian cybersecurity firm Kaspersky characterized the adversary as relying on various programs to harvest data on an “industrial scale” from primarily governmental organizations,…
Read MoreThe 2021 Application Protection report notes that ransomware was a factor in roughly 30 percent of U.S. breaches in 2020. Looking at the breach analyses, we found some of the most important controls were user account management, network segmentation, and data backup. We realize that implementing these controls can be difficult, so this article goes…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm