Category: AI in news
Managing privacy online is a constant balancing act. On the one hand, we need to provide a certain amount of our personal information to authenticate ourselves. In select environments, we also want to provide some additional information to our friends, family, and peers. On the other hand, we want to withhold that information from those…
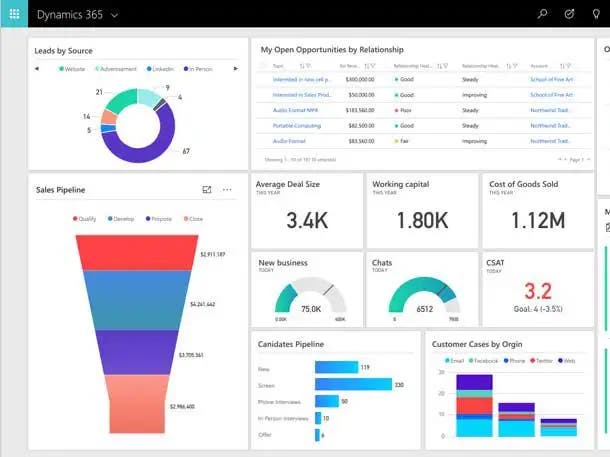
Read MoreOfferings will increase by as much as 17 percent and as little as 9 percent. Microsoft plans to increase prices for a variety of Dynamics 365 offerings on Oct. 1 by an average of 12 percent or $17 per user or per device per month as the vendor adds more generative artificial intelligence functionality and…
Read MoreScreenshots for Malwarebytes for Mac BleepingComputer Review: Malwarebytes Anti-Malware for Mac is a free security tool that allows you to scan your computer for common macOS infections and remove them. While focusing on adware infections, Malwarebytes for Mac will also scan for other known infections that are being released for the macOS operaitng system. With…
Read MoreMITRE defines NERVE as “an unclassified collaborative network that provides storage, computing, and networking resources.” However, the company’s CEO Providakes clarified that “there is no indication that MITRE’s core enterprise network or partners’ systems were affected by this incident.” Upon detection of the breach, the company said it took swift and comprehensive action including “taking…
Read MoreMicrosoft addresses 147 CVEs in its April 2024 Patch Tuesday release with three critical vulnerabilities and no zero-day or publicly disclosed vulnerabilities. Update April 10: The blog has been updated to include reference to exploitation for CVE-2024-29988 and the addition of CVE-2024-26234. View Change Log Microsoft patched 147 CVEs in its April 2024 Patch Tuesday…
Read MorePentera’s 2024 Report Reveals Hundreds of Security Events per Week, Highlighting the Criticality of Continuous Validation
by nlqip
Over the past two years, a shocking 51% of organizations surveyed in a leading industry report have been compromised by a cyberattack. Yes, over half. And this, in a world where enterprises deploy an average of 53 different security solutions to safeguard their digital domain. Alarming? Absolutely. A recent survey of CISOs and CIOs, commissioned…
Read MoreIn July 2020, the FBI Cyber Division issued Flash Alert AC-000129-TT reporting that malware had been found in the software used to calculate China’s value-added tax (VAT). However, the Chinese State Taxation Administration requires companies to install this particular software to operate within China. Third-party applications are already risky, but here a pre-infected application was…
Read MoreSalesforce’s biggest acquisition was the $28 billion purchase of Slack in 2021. Salesforce reportedly wants to buy artificial intelligence-powered cloud data management vendor Informatica, according to multiple news outlets, not long after its frequent acquisitions put Salesforce in the crosshairs of activist investors. Should Salesforce – a San Francisco-based customer relationship management software vendor –…
Read MoreScreenshots for Zemana AntiMalware BleepingComputer Review: Zemana AntiMalware is a cloud based malware scanner that provides excellent malware detection, quick scans, and easy malware removal. As it is cloud based, it always has the most current virus definitions and new definitions can be quickly pushed out by the developers when new malware is discovered. Zemana…
Read MoreProtecting information system media containing Controlled Unclassified Information (CUI), and monitoring for the use of portable storage devices and removable media is essential to protecting the integrity of information systems. Monitoring organizational communications at external boundaries, as well as key internal boundaries is essential to detect attacks, and potential indicators of attacks. Removable media is…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm