Category: AI in news
Cybersecurity Snapshot: CISA Says Midnight Blizzard Swiped U.S. Gov’t Emails During Microsoft Hack, Tells Fed Agencies To Take Immediate Action
by nlqip
Check out CISA’s urgent call for federal agencies to protect themselves from Midnight Blizzard’s breach of Microsoft corporate emails. Plus, a new survey shows cybersecurity pros are guardedly optimistic about AI. Meanwhile, SANS pinpoints the four trends CISOs absolutely must focus on this year. And the NSA is sharing best practices for data security. And…
Read MoreAccenture’s Suzanne Randall, TICOM’s Madonna Peltier-Yawakie and IBM’s Brendan Kinkade share stories from their tech careers and advocacy for indigenous peoples. Suzanne Randall wrote the business case 16 years ago that started Accenture’s Native American Employee Resource Group. Madonna Peltier-Yawakie and her husband help tribal entities secure funding for broadband network designs, project implementation and…
Read MoreNeutral/Mixed Intentions Many of the actors in this system are neither completely benign nor completely malicious. Some of these practices are bifurcated into legal and illegal practices, such as the rather obvious distinction between criminal and benign payment facilitators. Some of these provide services that can genuinely be used either way, such as reshipping services…
Read MoreInriver, a developer of product information management software, has hired Cunningham and a new chief sales officer as the Sweden-based company revs up for expansion in North America – including plans to grow its channel presence. Inriver, a Sweden-based developer of product information management software, has hired former Datto chief marketing officer Brooke Cunningham as…
Read More‘When you think about how much of [our revenue] is actually managed on a day-to-day [basis] by the partners, they’re massive custodians of the brand and customer success and lifetime value,’ says Salesforce channel chief Steve Corfield. Steve Corfield, capping off his first year as Salesforce channel chief, is at work on what he calls…
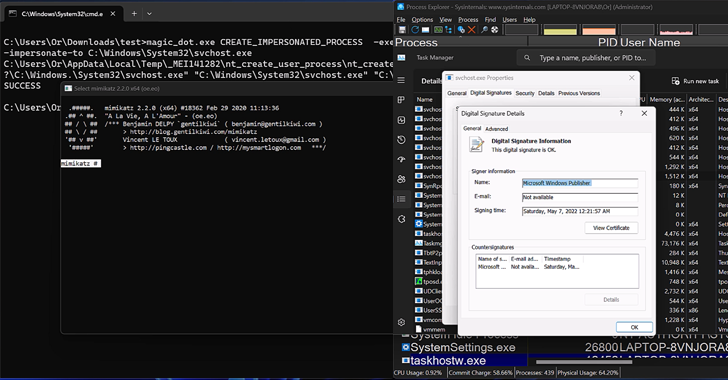
Read MoreApr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal and impersonate files, directories, and processes. “When a user executes a function that has a path argument in Windows, the DOS path at which the file or…
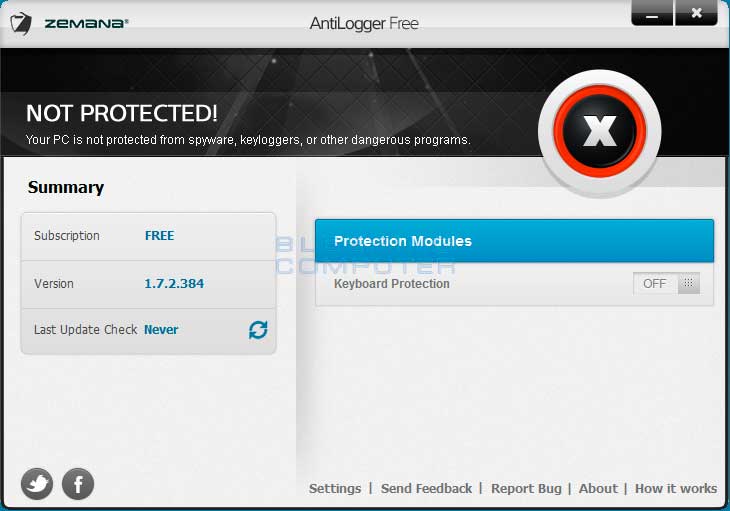
Read MoreScreenshots for Zemana AntiLogger Free BleepingComputer Review: Zemana AntiLogger Free is a program that protects your computer from keyloggers by encrypting your keystrokes. When a computer is infected with a keylogger it can see and record all keystrokes that you type on your computer. It can then log this information and send it to a…
Read MoreWhen scanning the network, organizations often have several layers of authorization and, therefore, require different permissions. All too oftentimes credentials that work on one system do not work on another. This Assurance Report Card (ARC) provides the ability to report and analyze Windows systems based on their authentication status. When managing a large enterprise,…
Read MoreMeta, the company formerly known as Facebook, is taking a proactive step to limit the spread of misinformation during India’s upcoming elections. Their AI arm, Meta AI, is blocking certain election-related keywords and redirecting users to the Indian Election Commission’s website. This decision comes amid growing concerns that AI could be used to manipulate voters…
Read MoreProofpoint, Slack, Tanium, AppDynamics, Palo Alto Networks, Nvidia and Kyndryl were among the tech companies making key executive hires during November 2023. New CEOs of Proofpoint and Slack. A new channel chief at Tanium. And a new chief marketing officer for Cisco subsidiary AppDynamics. Sumit Dhawan, formerly of VMware; Denise Holland Dresser, formerly with Slack…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm