Category: AI in news
Cybersecurity Snapshot: RansomHub Group Triggers CISA Warning, While FBI Says North Korean Hackers Are Targeting Crypto Orgs
by nlqip
Cybersecurity teams must beware of RansomHub, a surging RaaS gang. Plus, North Korea has unleashed sophisticated social-engineering schemes against crypto employees. Meanwhile, a new SANS report stresses the importance of protecting ICS and OT systems. And a Tenable poll sheds light on cloud-native VM. And much more! Dive into six things that are top of…
Read More“We want to provide the resources that empower businesses to scale,” AWS GM Miguel Alava said in a statement. Amazon Web Services has launched a Global Passport Program aimed at growing a select number of software partners’ business internationally, promising to connect these vendors to regional resellers and distributors to build local market pipelines. Aimed…
Read MoreFrontier has a market capitalization of about $10 billion with its stock trading at about $39 a share after market hours Wednesday, up about 11 percent. Verizon is reportedly in talks to buy rival Frontier Communications to grow its fiber network and better compete with AT&T and other rivals. The Basking Ridge, N.J.-based telecommunications vendor…
Read MoreNorth Korean threat actors have leveraged a fake Windows video conferencing application impersonating FreeConference.com to backdoor developer systems as part of an ongoing financially-driven campaign dubbed Contagious Interview. The new attack wave, spotted by Singaporean company Group-IB in mid-August 2024, is yet another indication that the activity is also leveraging native installers for Windows and…
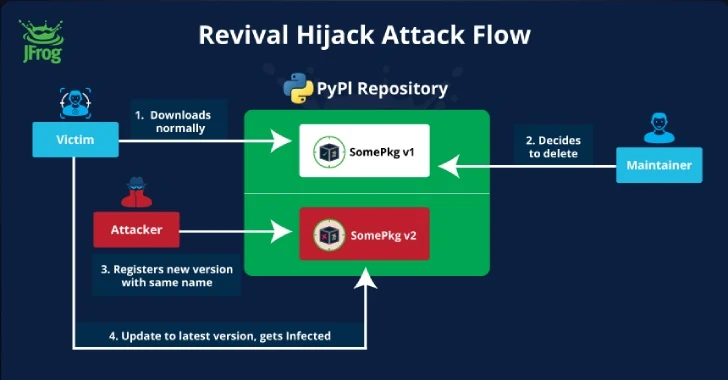
Read More“The problem is that while this is being discussed, attackers can already use this method to gain code execution on many PyPI users as we’ve demonstrated.” Advice for CISOs, app leaders Infosec leaders should warn their staff that a new version of a package can potentially include malicious code, he said, even if the last…
Read MoreSep 04, 2024Ravie Lakshmanan A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited in the wild in an attempt to infiltrate downstream organizations. It has been codenamed Revival Hijack by software supply chain security firm JFrog, which said the attack method could be used to hijack 22,000 existing…
Read MoreSep 04, 2024The Hacker NewsSaaS Security / Browser Security Account takeover attacks have emerged as one of the most persistent and damaging threats to cloud-based SaaS environments. Yet despite significant investments in traditional security measures, many organizations continue to struggle with preventing these attacks. A new report, “Why Account Takeover Attacks Still Succeed, and Why…
Read MoreSecurity Researcher Sued for Disproving Government Statements This story seems straightforward. A city is the victim of a ransomware attack. They repeatedly lie to the media about the severity of the breach. A security researcher repeatedly proves their statements to be lies. The city gets mad and sues the researcher. Let’s hope the judge throws…
Read MoreHuman error remains a significant risk for organizations when it comes to cyber threats. In fact, according to Proofpoint’s 2024 Voice of the CISO report, 74% of CISOs view human error as their organization’s biggest cyber vulnerability. However, 86% of CISOs believe employees understand their role in protecting the organization, which gives them hope for…
Read MoreSep 04, 2024Ravie LakshmananGDPR / Privacy The Dutch Data Protection Authority (Dutch DPA) has imposed a fine of €30.5 million ($33.7 million) against facial recognition firm Clearview AI for violating the General Data Protection Regulation (GDPR) in the European Union (E.U.) by building an “illegal database with billions of photos of faces,” including those of…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA