Category: AI in news
From 66degrees and Quantiphi to World Wide Technology and Deloitte, here are 11 top Google partners that won Google Cloud’s 2024 Partner of the Year Award in areas like sales, services and expansion. Although there are thousands of Google Cloud channel partners in North America, only a select few won the cloud company’s prestigious Partner…
Read More‘When you look at the whole class of ecosystem that’ll be built around AI, it’ll be one of the most exciting ecosystem shuffles in adding value that we’ve seen,’ Red Hat CEO Matt Hicks tells CRN. Red Hat CEO Matt Hicks told CRN that channel partners have an immense opportunity to add value and drive…
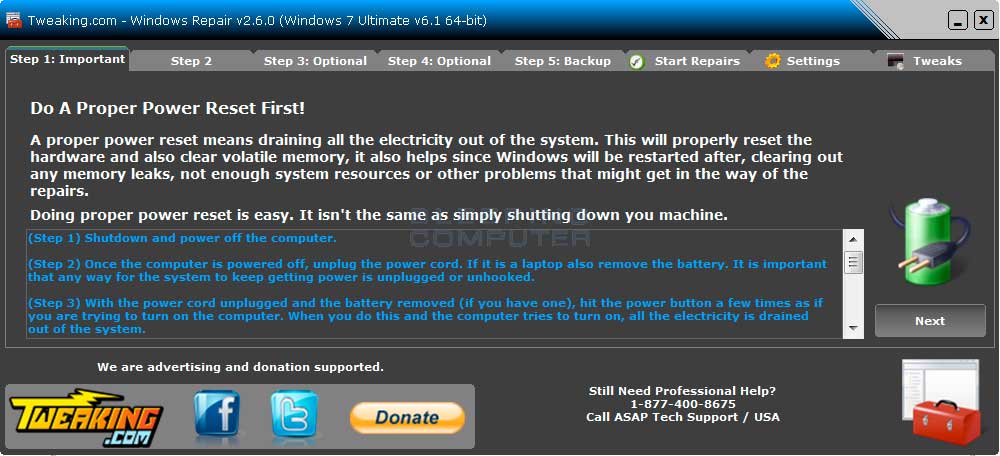
Read MoreScreenshots for Windows Repair (All In One) BleepingComputer Review: Windows Repair is a utility that contains numerous mini-fixes for Windows. This tool will allow you to repair common issues with your computer such as firewall, file permission, and Windows Update problems. When using this tool you can select the particular fixes you would like to…
Read MoreTo ensure they have the most complete information about the security posture of assets, organizations should deploy scans that use credentials. Scans that use credentials and successfully authenticate on a system (and run with Local Security Checks enabled) return a more comprehensive set of data about the system. This Assurance Report Card (ARC) provides the…
Read MoreOracle addresses 239 CVEs in its second quarterly update of 2024 with 441 patches, including 38 critical updates. Background On April 16, Oracle released its Critical Patch Update (CPU) for April 2024, the second quarterly update of the year. This CPU contains fixes for 239 CVEs in 441 security updates across 30 Oracle product families.…
Read More‘This case is not only novel, but also threatens to undermine cybersecurity by making it more difficult for companies to respond to increasingly sophisticated and highly-resourced cyber-threats,’ the Software Alliance wrote in an amicus filing with the U.S. District Court Southern District of New York Friday. A software trade group says a case pursued by…
Read MoreWe are excited to announce that F5 Labs has become a data partner of the Exploit Prediction Scoring System (EPSS). The Internet-wide scanning and attempted exploitation activity that makes up our Sensor Intel Series also happens to be good training data for the machine learning system under EPSS’ hood. F5 Labs wrote about EPSS in…
Read MoreThe MongoDB database powers Alibaba Cloud’s ApsaraDB for MongoDB database-as-a-service offering, which is seeing significant sales growth in China, especially among gaming developers, according to the companies. Next-generation database developer MongoDB and Chinese cloud platform giant Alibaba Cloud are extending by four years their strategic alliance under which the MongoDB cloud database is the foundation…
Read More“This change was made based on partner feedback and will provide greater flexibility, creating a smoother experience for both partners and customers,” according to Microsoft documents. This quarter, Microsoft plans to allow solution providers in its Cloud Solution Provider program to transfer end customer new commerce experience subscriptions from one partner to another midterm, eliminating…
Read MoreTo ensure they have the most complete information about the security posture of assets, organizations should deploy scans that use credentials. Scans that use credentials and successfully authenticate on a system (and run with Local Security Checks enabled) return a more comprehensive set of data about the system. This Assurance Report Card (ARC) provides the…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm