Category: AI in news
Cybersecurity Snapshot: Cyber Agencies Offer Secure AI Tips, while Stanford Issues In-Depth AI Trends Analysis, Including of AI Security
by nlqip
Check out recommendations for securing AI systems from the Five Eyes cybersecurity agencies. Plus, Stanford University offers a comprehensive review of AI trends. Meanwhile, a new open-source tool aims to simplify SBOM usage. And don’t miss the latest CIS Benchmarks updates. And much more! Dive into six things that are top of mind for the…
Read MoreThe National Information Assurance (NIA) Policy v2.0 requires that agencies classify their assets. Tenable recommends using the Cyber Exposure Life Cycle model in conjunction with NIAv2 compliance efforts. The first stage (Discovery) of the Cyber Exposure lifecycle includes identifying and mapping assets across computing environments. In order to maintain a standardized method of classification of…
Read MoreIntroduction Identity is one of those bedrock concepts in security that seems simple and intuitive when we use it in our daily lives (“Hi Bob!”), about ourselves (“I’m a chef!”), and in personal (“You’re my friend!”) and intimate (“I love you!”) contexts. Yet when we build or deploy systems that rely on identity — a…
Read More‘I’m really excited to come back because there’s real problems that I feel like I can help fix,’ says Arnie Bellini, ConnectWise founder. Arnie Bellini has a lot to say. And after a five-year noncompete agreement ending in February, he’s officially back in the channel and ready to make a splash. ‘I’m really excited to…
Read More‘This flexibility is crucial for adapting to business dynamics like mergers, acquisitions or shifts in customer preferences. It allows us to be more responsible and agile in how we manage our client relationships,’ Jean Prejean, president of Guardian Computer, tells CRN. Microsoft has confirmed that it is changing one of the most controversial parts of…
Read MoreThe departure of Sam Altman, Greg Brockman and, potentially, a large percentage of OpenAI employees to Microsoft may not ultimately be the best thing for the tech giant’s aspirations in GenAI. One of the biggest strengths of OpenAI has long been that it had backing, financial and otherwise, from Microsoft, without needing Microsoft to approve…
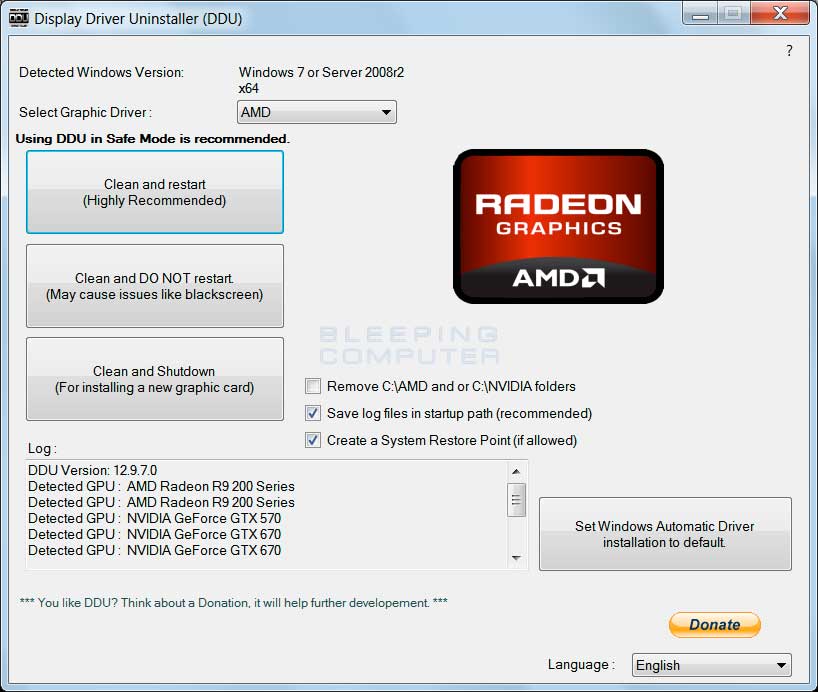
Read MoreScreenshots for Display Driver Uninstaller BleepingComputer Review: Display Driver Uninstaller, or DDU, is a driver utility programs that allows you to remove all traces of NVIDIA, AMD, and INTEL display and audio drivers from Windows. This allows you to perform a clean install of new drivers so that there are no potential issues with previous…
Read MoreThe National Information Assurance (NIA) Policy v2.0 requires that agencies classify their assets. Tenable recommends using the Cyber Exposure Life Cycle model in conjunction with NIAv2 compliance efforts. The first stage, Discovery, of the Cyber Exposure lifecycle includes identifying and mapping assets across computing environments. In order to maintain a standardized method of classification of…
Read MoreIn an evolving threat landscape, the DoD must make sure that its mission-critical operations don’t experience power outages. From illuminating command centers to fueling advanced weapons systems, uninterrupted power is vital to the Department of Defense’s (DoD) national defense mission. At the core of this critical infrastructure is operational technology (OT), which functions behind the…
Read More‘Look to N-able to trust in helping you enable your transformation,’ says N-able CEO John Pagliuca. ‘We’re the partner that can enable that transformation; we will help you bring more services to market and help you augment.’ Between new integrations with HaloPSA and Rewst and a new Cloud Commander offering, N-able is “laser-focused” on being…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm