Category: AI in news
Granted, such low-level activities don’t produce the same worker anxiety or organizational confusion that downsizing and M&As do — and, thus, don’t present the same opportunities for hackers. However, Carruthers says they still create changes that hackers can use to their advantage. “They all breed opportunities for attackers.” Carruthers knows firsthand how effective such hacker…
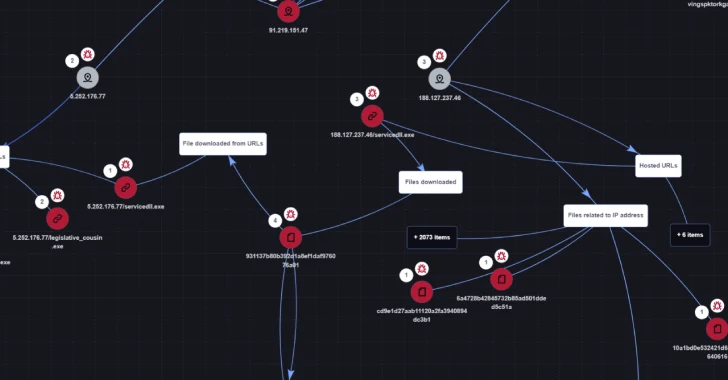
Read MoreSep 04, 2024Ravie LakshmananMalware / Network Security A new malware campaign is spoofing Palo Alto Networks’ GlobalProtect VPN software to deliver a variant of the WikiLoader (aka WailingCrab) loader by means of a search engine optimization (SEO) campaign. The malvertising activity, observed in June 2024, is a departure from previously observed tactics wherein the malware…
Read MoreIn episode 14 of “The AI Fix”, Graham makes an apology, Mark wonders if suicide drones have second thoughts, people pretend to be robots, and some researchers prove that all you need for an AI to generate a somewhat usable version of the computer game Doom out of thin air is to already have a…
Read MoreList of Old NSA Training Videos The NSA’s “National Cryptographic School Television Catalogue” from 1991 lists about 600 COMSEC and SIGINT training videos. There are a bunch explaining the operations of various cryptographic equipment, and a few code words I have never heard of before. Tags: cryptography, FOIA, history of cryptography, history of security, NSA,…
Read MoreCRN breaks down 10 major new hires and executive departures at AWS in recent months, which includes many AI executives. Amazon Web Services is snatching up major artificial intelligence talent including CEOs from AI startups along with executives who’ve worked for the likes of OpenAI, Microsoft and Google Cloud. However, AWS has also recently witnessed…
Read MoreAn old but persistent email scam known as “sextortion” has a new personalized touch: The missives, which claim that malware has captured webcam footage of recipients pleasuring themselves, now include a photo of the target’s home in a bid to make threats about publishing the videos more frightening and convincing. This week, several readers reported receiving…
Read MoreSep 03, 2024Ravie LakshmananRansomware / Malware A hacktivist group known as Head Mare has been linked to cyber attacks that exclusively target organizations located in Russia and Belarus. “Head Mare uses more up-to-date methods for obtaining initial access,” Kaspersky said in a Monday analysis of the group’s tactics and tools. “For instance, the attackers took…
Read MoreBackwards compatibility takes us … backwards Unfortunately, once you keep support for old, vulnerable versions of your software, people will continue to use old, vulnerable versions of your software. Vendors shrugged their shoulders, and pundits blamed software users for choosing to use a working-but-vulnerable version instead of a broken-but-patched version (as if that was a…
Read MoreIn the digital realm, secrets (API keys, private keys, username and password combos, etc.) are the keys to the kingdom. But what if those keys were accidentally left out in the open in the very tools we use to collaborate every day? A Single Secret Can Wreak Havoc Imagine this: It’s a typical Tuesday in…
Read MoreOn the other hand, risk tolerance needs to be a guided discussion around a particular objective or a risk scenario, where a CISO can develop a hypothesis. “If you can be explicit, if you can describe it well, then you can really have a good conversation to get everyone on the same page as to…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA