Category: AI in news
Eight vulnerabilities have been uncovered in Microsoft applications for macOS that an adversary could exploit to gain elevated privileges or access sensitive data by circumventing the operating system’s permissions-based model, which revolves around the Transparency, Consent, and Control (TCC) framework. “If successful, the adversary could gain any privileges already granted to the affected Microsoft applications,”…
Read MoreSep 03, 2024Ravie LakshmananInsider Threat / Network Security A 57-year-old man from the U.S. state of Missouri has been arrested in connection with a failed data extortion campaign that targeted his former employer. Daniel Rhyne of Kansas City, Missouri, has been charged with one count of extortion in relation to a threat to cause damage…
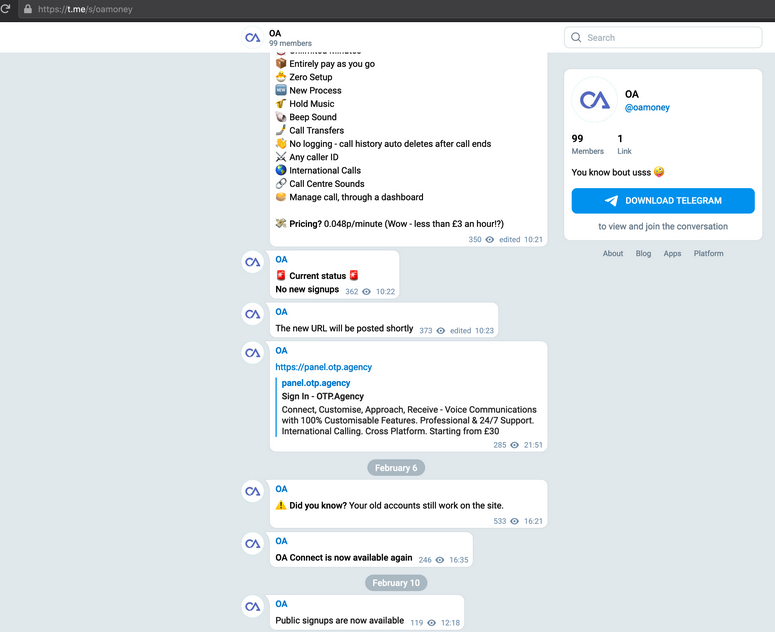
Read MoreThree men in the United Kingdom have pleaded guilty to operating otp[.]agency, a once popular online service that helped attackers intercept the one-time passcodes (OTPs) that many websites require as a second authentication factor in addition to passwords. Launched in November 2019, OTP Agency was a service for intercepting one-time passwords needed to log in…
Read MoreThreat actors linked to the RansomHub ransomware group encrypted and exfiltrated data from at least 210 victims since its inception in February 2024, the U.S. government said. The victims span various sectors, including water and wastewater, information technology, government services and facilities, healthcare and public health, emergency services, food and agriculture, financial services, commercial facilities,…
Read MoreThe report added that the FudModule rootkit has historically been shared between Citrine Sleet and Diamond Sleet (formerly Zinc), another North Korean threat actor known to target media, defense, and information technology (IT) industries globally. RCE to deliver FudModule The report explained that victims were directed to a Citrine Sleet-controlled exploit domain voyagorclub[.]space. While the…
Read MoreSQL Injection Attack on Airport Security Interesting vulnerability: …a special lane at airport security called Known Crewmember (KCM). KCM is a TSA program that allows pilots and flight attendants to bypass security screening, even when flying on domestic personal trips. The KCM process is fairly simple: the employee uses the dedicated lane and presents their…
Read MoreSep 02, 2024The Hacker NewsVulnerability Management / Webinar The world of cybersecurity is in a constant state of flux. New vulnerabilities emerge daily, and attackers are becoming more sophisticated. In this high-stakes game, security leaders need every advantage they can get. That’s where Artificial Intelligence (AI) comes in. AI isn’t just a buzzword; it’s a…
Read MoreA former IT engineer is facing federal charges in the United States after his former employer found it had been locked out of its computer systems and received a demand for $750,000. At approximately 4pm EST on November 25, 2023, staff at an industrial company headquartered in Somerset County, New Jersey, began to receive password…
Read MoreSep 02, 2024The Hacker NewsCybercrime / CISO Insights The FBI and CISA Issue Joint Advisory on New Threats and How to Stop Ransomware Note: on August 29, the FBI and CISA issued a joint advisory as part of their ongoing #StopRansomware effort to help organizations protect against ransomware. The latest advisory, AA24-242A, describes a new…
Read MoreThere’s a cultural barrier to investing proactively in cybersecurity, Johnson admits. “We are a reactionary society, but cybersecurity is finally being seen for what it is: an investment. An ounce of prevention is worth a pound of cure.” 8. Test, test, and test again “A lot of people are approaching backups from a backup point…
Read MoreRecent Posts
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners